A practical example how broken MD5 really is
November 5, 2014
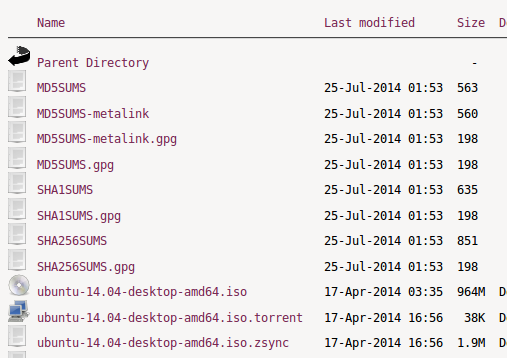
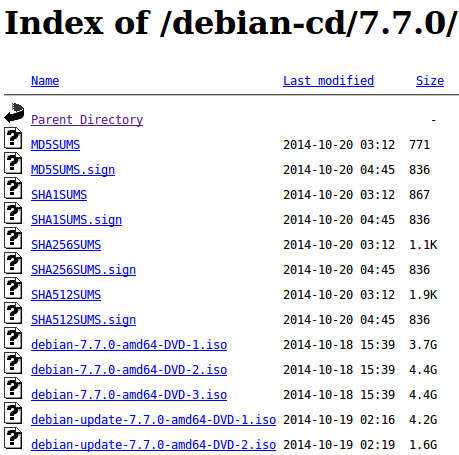
Nat McHugh did a wonderful post with two completely different monochrome pictures which have the same MD5 sum. Take a look! MD5 as a secure hash function should provide the properties shown in this Wikipedia article. But as Nat says in his own words:
I believe he is correct, nothing shows better how broken MD5 is than two images with the same MD5 sum and that really nobody should use it anymore for security reasons. Using it for checking file corruption during transfer is Ok, but the hash for ISO files or packages for Linux Distributions you download should not be checked with MD5. CPU power is cheap nowadays. The big ones like Ubuntu, Debian and CentOS already have changed to provide also SHA1 and SHA256 hashes for all the files. OpenSuse provides MD5 and SHA1 … better would be SHA256 too. Anyway use SHA256 were possible to verify your downloads!!
Sony Xperia smart phones have an automatically recreated “Baidu” folder and connect to a server in China
November 1, 2014
As I’m a user of a Sony Xperia smart phone I pick that thread up. In the Sony support forums a really log thread is running because all current Xperia smart phones got with the Upgrade to Android 4.4 and folder “Baidu” on the internal storage. If you delete it and reboot the phone it gets recreated. Here a screenshot from lggyjp from the forums:
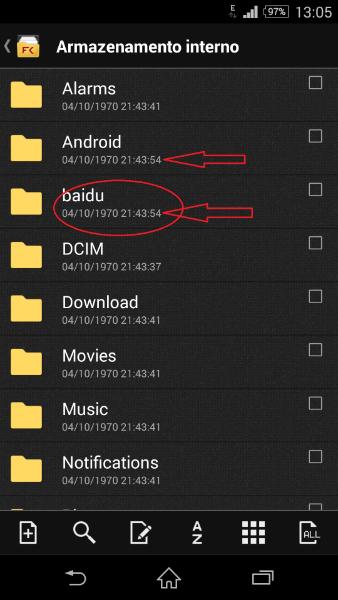
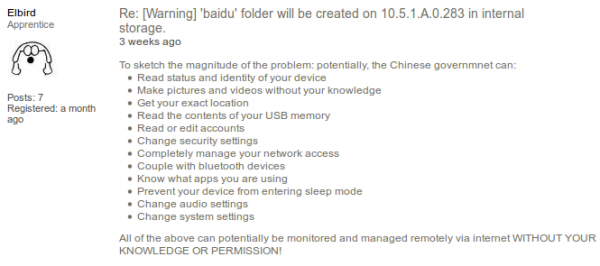
Sony is claiming that this is the connection to Baidu the Chinese Google equivalent, but the setup has some potential implications which gets user upset. An example is the post by Elbrid in the forum:
Following is the response by Sony, first by a support guy called Richard:
This folder will be removed in future software updates for the phone. Until then i can only advise that you delete it manually after a reboot if you want to remove it. It’s safe to just delete it.
and than the post yesterday by responsible manager:
Hey guys
Magnus Hilding here – I’m heading the team developing MyXperia @ Sony Mobile. As Rickard said, we built the app using both protocols to ensure both our Chinese and global users could enjoy MyXperia. However, we’ve designed later versions to package the service relevant to a specific region only – these updates are right around the corner, rolling out soon.
As Rickard said, it’s really nothing to worry about.
/Magnus
If you want to remove it at once and not wait for Sony, take a look at this article which shows the 9 steps needed to get rid of it.
Howto get an A+-Rating at Qualys SSL Labs with Apache 2.2
One of my HTTPS servers currently gets an A- on Qualys SSL Labs test, as I’m running Ubuntu 12.04 LTS with Apache 2.2 which does not support the ECHDE-Cipher suites, which is required for Perfect Forward Secrecy with the Internet Explorer.
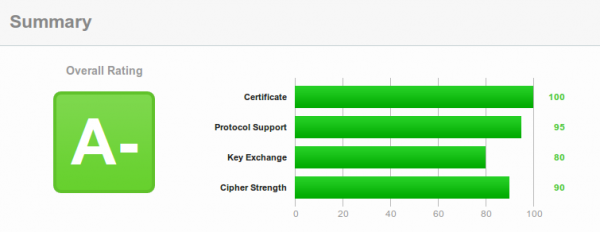
Upgrading to Ubuntu 14.04 needs some major rework for which I currently don’t have the time for.But there is now a trick to get that A-Rating and it is called TLS Interposer. It uses LD_PRELOAD to intercept the OpenSSL API calls and adds some additional features and security settings.
Currently there is no deb package for Ubuntu 12.04, so we need to compile it for our-self:
wget https://github.com/Netfuture/tlsinterposer/archive/master.zip
unzip master.zip
cd tlsinterposer-master/
make
Possible errors:
make: cc: Command not found-> install the gcc (apt-get install gcc)tlsinterposer.c:29:25: error: openssl/ssl.h: No such file or directory–> Install the OpenSSL Development package (apt-get install libssl-dev)
Now we need only an make install and we’re ready to try it. For this we add
export LD_PRELOAD=/usr/local/lib/libtlsinterposer.so
at the end of
/etc/apache2/envvars
and restart Apache with
/etc/init.d/apache2 restart
And you get
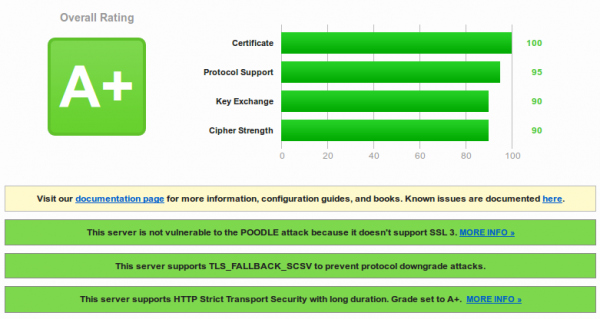
Success!!!
You need also following for an A+ Rating:
- Following needs to be still in the Apache config:
SSLProtocol ALL -SSLv2 -SSLv3
SSLHonorCipherOrder On
SSLCompression Off
# SSLCipherSuite settings will be ignored - You need to HSTS configured, check this link for how to enable it on Apache 2.2
So this is with Ubuntu 12.04 … I’ve tried the same with Centos 6 but I didn’t have success. Following problems did arise
1. Makefile
The Makefile does not support the names of the ssl libs on Centos 6 – when you compile, you get:
tlsinterposer.c:85: error: ‘DEFAULT_SSLLIB’ undeclared here (not in a function)
The Makefile has a regex that does not work with Centos 6. I changed following
# diff Makefile.orig Makefile
32c32
< ldconfig -p | sed -n -e 's/^\t*\(libssl\.so\.[0-9]\.[0-9]\.[0-9]\).*/#define DEFAULT_SSLLIB "\1"/p' > $@
---
> ldconfig -p | sed -n -e 's/^\t*\(libssl\.so\.[0-9][0-9]\).*/#define DEFAULT_SSLLIB "\1"/p' > $@
and deleted the file ssl-version.h and called make again and it compiled. I’ve reported that to author.
2. application’s cipher is not overwritten
Loading the TLS Interposer with putting it in /etc/sysconfig/httpd and than doing an /etc/init.d/httpd restart worked but the application’s cipher didn’t get changed. I could verify that with the test scripts which come with TLS Interposer:
# ./run_tests
gcc -O2 -Wall -Wextra simple_server.c -lcrypto -lssl -o simple_server
Test 1a pass
Test 1b FAIL!
Test 1c pass
Test 1d pass
Test 1e pass
Test 2a pass
Test 2b pass
Test 2c pass
Test 3a pass
Test 3b pass
Test 4a pass
Test 4b pass
Test 4c pass
Test 5a pass
Test 5b pass
Test 5c pass
Test 5d pass
I’ve reported that to the author. If I get an update on this I’ll report in my blog about this.
Take care if using Ubuntu 12.04 as a client – TLS 1.2 is not enabled by default
October 24, 2014
It got fixed with Ubuntu 14.04 but 12.04 is still supported and many people are still using 12.04 and even with the OpenSSL package update (2014-10-02) TLS 1.2 is not enabled by default. Take a look at this bug report and the statement from Marc Deslauriers (Ubuntu Security Engineer):
That USN doesn’t re-enable TLSv1.2 by default for clients in Ubuntu 12.04. It simply fixes an issue if someone _forced_ TLSv1.2 to be enabled.
You’re asking why we got into that problem in the first place … Marc tells us also this:
Ubuntu 12.04 contains openssl 1.0.1, which supports TLS v1.2. Unfortunately, because of the large number of sites which incorrectly handled TLS v1.2 negotiation, we had to disable TLS v1.2 on the client.
So someone thought again he is smarter than the OpenSSL guys … but this was not the first time …. lets remember this “optimization” of OpenSSL by the Debian guys .. could they please clean up their mess and enable TLS 1.2 by default as in 14.04?
Mikrotik changed the update policy in their license agreement
October 13, 2014
Just as information for you guys using Mikrotik’s RouterOS but who don’t monitor the wiki for changes or are regular readers of the forum. Mikrotik changed its license concerning the updates. Before this summer following paragraph was on their license wiki page:
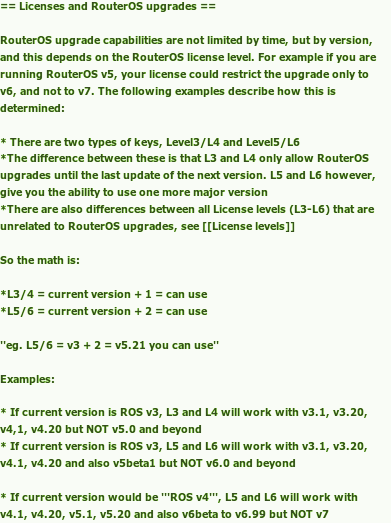
You can take a look at the full old version here. Anyway this whole paragraph has been removed. Also with RouterOS 6.20 the following got removed when typing /system license print on the router:
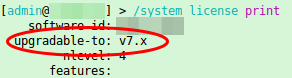
So what does that mean now? jarda from the forums put it nicely:
Protect your PC against the BadUSB attack on Linux and Windows
October 12, 2014
At the Black Hat conference this year researchers from Berlin-based Security Research Labs (SRLabs) showed an attack method they called “BadUSB“, which allowed them, with manipulated USB device firmwares (e.g. from a USB Stick), to simulate an keyboard. With this keyboard they executed commands on the victims computer without he/she knowing it. The victim just inserted a USB stick to copy some data …. but the new keyboard executes some commands in the background.
To protect yourself against such an attack the computer needs to configured in a way that it does not bind any newly added device as new keyboard without asking the user. For Linux there is a kernel feature starting with 2.6.13-rc3 ( = since 2005) which allows to bind and unbind drivers from devices manually from user space. More information can be found on this topic here and here. And this blog post from Christian Vogel shows how to use it against BadUSB. What is currently missing is a simple GUI program which allows you to allow/deny devices with on click.
On the Windows site there is already such a program. This freeware program is made by the German security vendor (e.g. anti virus software) G DATA and is called “G DATA USB KEYBOARD GUARD” and can be downloaded from here. After installing you’ll be prompted following screen if a new keyboard is inserted.
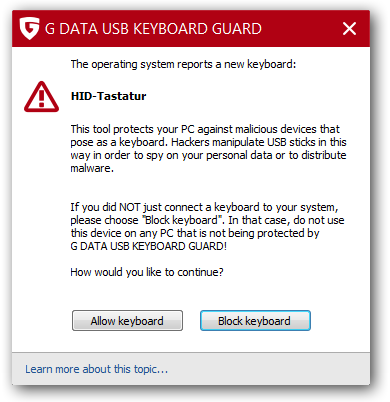
It would be nice if the various desktop environments on Linux add a similar feature … the kernel support is there already.
Check your hardening index of your Linux systems
October 6, 2014
I found a small program called Lynis, which does a system check of your Linux and Unix System. From the homepage:
Lynis is an open source security auditing tool. Primary goal is to help users with auditing and hardening of Unix and Linux based systems. The software is very flexible and runs on almost every Unix based system (including Mac). Even the installation of the software itself is optional!
To test a system is really easy, just download the tar.gz from here and extract the tar as root (otherwise it will complain) and change into its directory and call
./lynis -c
for the interactive mode (waits after each section) or
./lynis -q
for the quick mode which only logs the results to the log file. In both cases the log is written to /var/log/lynis.log.
For the following screenshots a I did setup a test system with some changes to show you some errors and warnings :-):
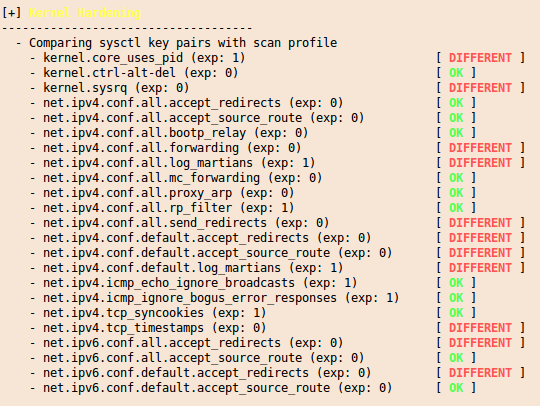
and at the end you get a summary with entries like this:
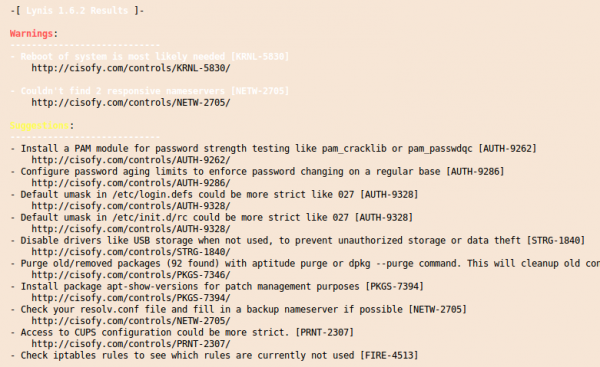
And you’ll get also a “Hardening index” which allows you to compare various systems against each other. 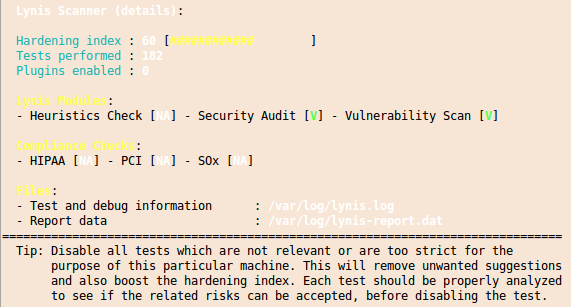
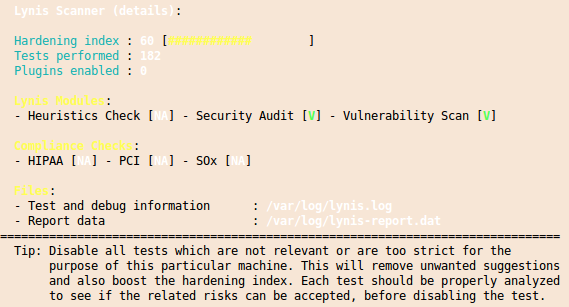
I you want to check multiple systems it it also possible to create an rpm file with the lynis.spec file from the Lynis homepage. You should run this software every time you setup a new system to make sure that you didn’t leave the big whole open.
Solution for high CPU load when using the flash player in the browser on Linux
September 17, 2014
For some time now I wondered why I had such a high CPU load while watching e.g. YouTube videos, even if I’ve a Nvidia GeForce GTX 760 in my PC. Ok thats not the latest card, but normal HD video should be accelerated with it also. 20% CPU load on my modern CPU is too much for a simple YouTube video:
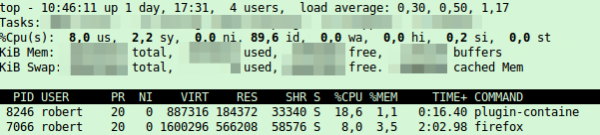
The solution is quite easy – the flash player has disabled the hardware acceleration by default. Following steps need to be done to enable it – as I only have an Nvidia card I was only able to test it for it, but looking around I found some tips for the other cards too.
- Check if you’ve
libvdpau1installed. On Ubuntu its done like this:
# dpkg -l | grep vdpau
ii libvdpau1:amd64 0.7-1 amd64 Video Decode and Presentation API for Unix (libraries) - You need a fitting graphics card driver:
- Nvidia: Nouveau and Closed Source driver should work
- AMD Radeon: You need the Mesa projects drivers (r300g, r600g or radeonsi)
- Intel: You need also following library/packaged installed:
libvdpau-va-gl1(as Intel supports only the libva interface for video acceleration)
- You need (most likely) to create following file
/etc/adobe/mms.cfgwith following content. It is possible that the directory and file exists in this case add the lines:
EnableLinuxHWVideoDecode=1
OverrideGPUValidation=1 - Now you need to make sure that the player is not running anymore:
# ps aux | grep plugin-containe
robert 8246 0.1 0.9 798312 153260 ? Sl Sep16 0:57 /usr/lib/firefox/plugin-container /usr/lib/flashplugin-installer/libflashplayer.so -greomni /usr/lib/firefox/omni.ja -appomni /usr/lib/firefox/browser/omni.ja -appdir /usr/lib/firefox/browser 7066 true plugin
# kill 8246 - Now open the YouTube page again you tried before and top should show following – under 10% CPU Load, thats better.
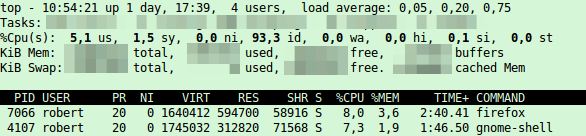
US-CERT releases virtual appliance for MitM attacks
August 24, 2014
Some time ago I wrote a blog post on Burp as a MitM Proxy (Man-in-the-Middle) – now there is for some purposes an even easier way. The US-CERT has released the first version of a virtual appliance with the name Tapioca (Transparent Proxy Capture Appliance). With it, it is easy to check if programs don’t do certificates validation correctly. I really recommend to try it out! Some areas that are often good for a bad implementations are: mobile apps, hardware and embedded devices and generally stuff that needs a high domain specify know how and that often goes with less software engineering know how. 😉
Check if your mailserver is encrypting SMTP to/from other mail servers
August 10, 2014
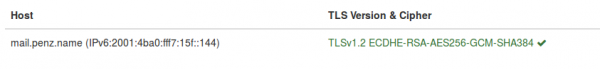
For readers with their own mail server (or if you want to check what your provider is doing) – verify that your mail server accepts encrypted communication and that PFS is enabled. Just click on this link and enter the domain name to test. Some big players goof there …. It should at least look like in the screen shot. DANE would be cool, but that’s not that easy at this point as you need a working DNSsec DNS server, which not all registrars provide. Sure you can host your own authoritative DNS servers but that is work …
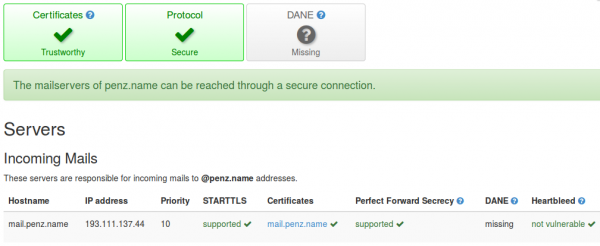
ps: send also a mail to [email protected] to check if sending mails is also encrypted. It should look like this:
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
42 queries. 0.077 seconds.





