Mini Howto for a simple way to block a MAC address on Extreme Network switches
September 12, 2015
Yesterday I needed to block a MAC address on an Extreme Networks switch (XOS) … sure, I could write an ACL for this but there is a better way:
To block a MAC address:
create fdbentry aa:bb:cc:dd:ee:ff vlan <VlanName> blackhole
To unblock a MAC address:
delete fdbentry aa:bb:cc:dd:ee:ff vlan <VlanName> blackhole
Howto configure a TG588 from A1 Telekom as VDSL modem and a Mikrotik device as router
September 11, 2015
Our big nation provider A1 Telekom went ahead and provided our house as first provider with VDSL – hoped FTTH makes the race … but anyway VDSL is better than the old stuff I had before. So I went ahead and ordered it and I got send an TG588 modem/router where you can almost configure nothing. e.g. UPNP is enabled and you can’t even deactivate it – when was it a good idea that a clients tells a firewall what to do in the first place? So I had to 3 options
- Buy a VDSL router like FRITZ!Box 3390, which is also a home router where I don’t like the configuration methods and feature set
- Buy a VDSL modem/bridge like Vigor130, and connect via a real router over pppoe. But the system is not on the A1 Telekom vectoring devices whitelist. No change for vectoring than ….
- Get the TG588 to play only modem and let my real router to do pppoe tunnel.
As you most likely already guested I opt for the last one. This howto shows you how to configure the TG588 as modem and an Mikrotik router as router (could be any other devices that supports pppoe in client mode). I was not that easy to gather all this information and so it maybe helps others to save time.
First lets connect the TG588 to the telephone line and the Mikrotik with one interface (in my case ether0) to it. Let everything boot up and connect your PC to the Mikrotik clients ports (in the default config). Log into the Mikrotik and configure the interface to the modem like this:
/interface ethernet set [ find default-name=ether1 ] name=ether1vlanTransitModem
/ip address add address=10.0.0.1/24 interface=ether1vlanTransitModem network=10.0.0.0
/ip firewall nat add action=masquerade chain=srcnat comment="nat the traffic to the dsl modem web interface, only activate when needed" out-interface=ether1vlanTransitModem
This gives the interface a nice name, sets the IP address of that uplink interface and configures the router to perform an source NAT, so you’re able to configure the modem even if you’re behind the Mikrotik router.Make sure that there is not DHCP Client running on the Mikrotik (specially on the ether0 interface)
Now log into your TG588 by going to http://10.0.0.138. Your default user has not the rights to change anything – so we need to change to an other default created user, with higher privileges. Click on the “admin” username:
Choose “change to other user”:
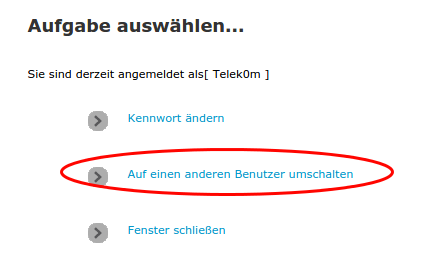
Provide following user data (worked at the time of writing, may got changed)
User: Telek0m
Password: Austria!Eur0
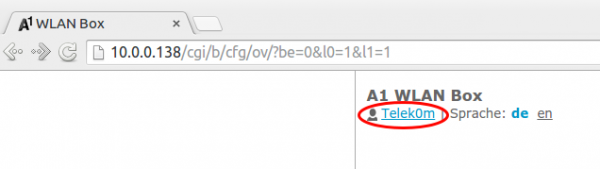
Now your user should have changed to following:
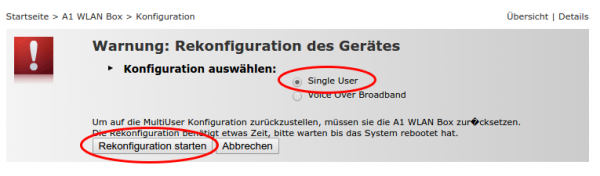
After that you will have more options to select from. Click onto “A1 WLAN Box” followed by “Configuration” and then choose “reconfigure A1 WLAN Box”
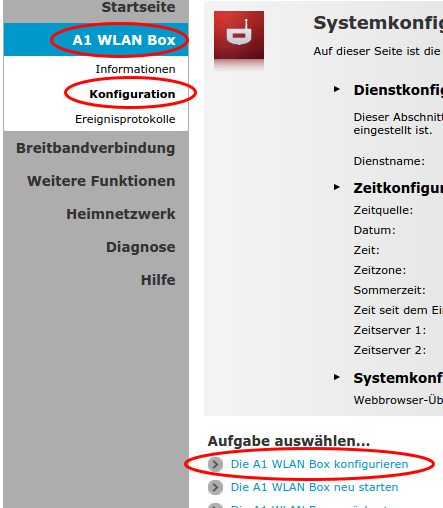
On the following page you need to select “single user” mode and click on reconfigure
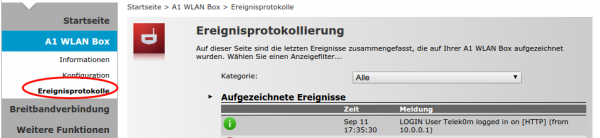
Now you’re done with the TG588 – after rebooting it should be fine. Now you need only following two pages on the TG588 – the rest is done by the Mikrotik router
First the event log, here you can check if something does not work:
And following page shows you the speed you’re connected with the provider network
The easy part
Now after all that clicking the Mikrotik part is easy:
/interface pppoe-client add add-default-route=yes disabled=no interface=ether1vlanTransitModem max-mru=1492 max-mtu=1492 mrru=disabled name=pppoeDslInternet password=XXXXXXXX use-peer-dns=no/yes user=XXXXXX
Replace XXXX with the data you got from A1 Telekom.
Now you’re internet connection should be up … test it with
ping 8.8.8.8
after that we only need some Firewall rules move the client traffic correctly to and from the Internet.
/ip firewall mangle add action=change-mss chain=forward comment="max MTU size for pppoe 1492" new-mss=1452 out-interface=pppoeDslInternet protocol=tcp tcp-flags=syn tcp-mss=!0-1452
/ip firewall nat add action=masquerade chain=srcnat comment="nat all traffic which goes over dsl into the internet" out-interface=pppoeDslInternet
Now you’re done. Hope this helped.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
28 queries. 0.050 seconds.