Decoding SNMPv3 encrypted traffic in Wireshark
January 7, 2016
Talking with fellows about SNMPv3 I hear often that its not that critical that SNMP is encrypted and that encryption makes debugging more complicated as they can’t see what is send over the network.I won’t talk about the need for encrypting SNMP as it is like SSH gets used instead of Telnet. This post shows how easy it is to decode SNMPv3 encrypted messages with Wireshark (if you know the secrets 🙂 ). This is possible as SNMPv3 is a simple UDP protocol which encodes the packets with a shared secret and does not use forward secrecy like TLS does.
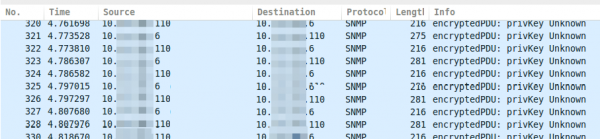
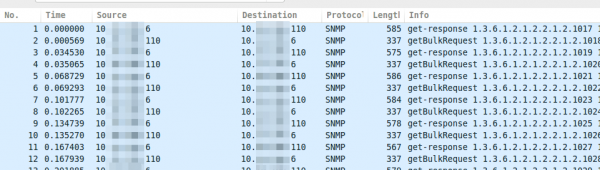
If you take a look on properly encrypted SNMPv3 traffic it looks like this.
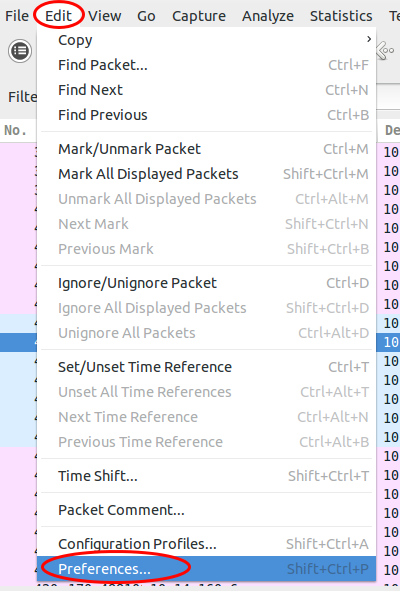
Now you just click on “Edit | Preferences”:
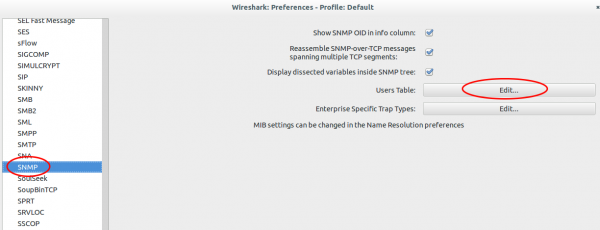
Search for “Protocols | SNMP” and click on “User Table | Edit”.
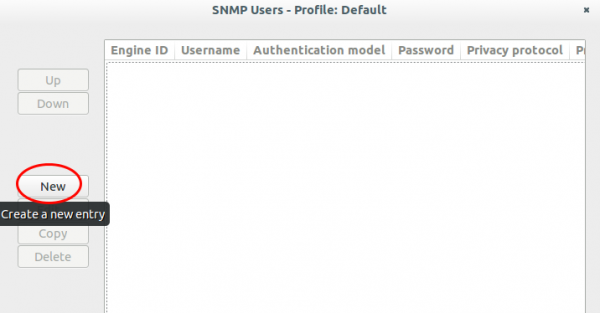
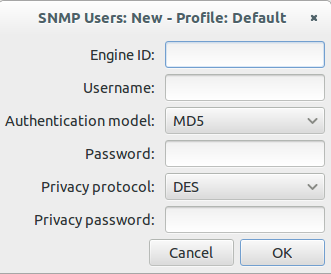
Click onto the “New” button:
Now enter your user name, select the authentication and encryption method and provide the 2 passwords. You don’t need to provide the Engine ID normally.
After clicking onto Ok multiple times the traffic looks like this:
If you use one SNMP profile for multiple systems its nice that the values get stored in the Wireshark preferences. Hope this takes some fear away from SNMPv3. 🙂
Mobile security apps often leak information via ad network libraries
January 5, 2016
Why you should not use so called security software, specially if they are “free”, on your mobile? Because they make your security worse most of the time. And no I’m not talking about vulnerabilities in the software itself – sure there a plenty. No there is principle problem as they use ads to finance their software. Why is that bad for your security?
Most big websites like Google and Facebook use today HTTPS for anything you transfer to/from them. But what most people miss is that most ad networks still use HTTP for tracking the user. If you’re just using an app or sometimes even in the background, it sends your information in the clear to the tracking network. Its bad that you get tracked in the first place but in a public WiFi, this information can be used to target and attack you. Lets show you an example.
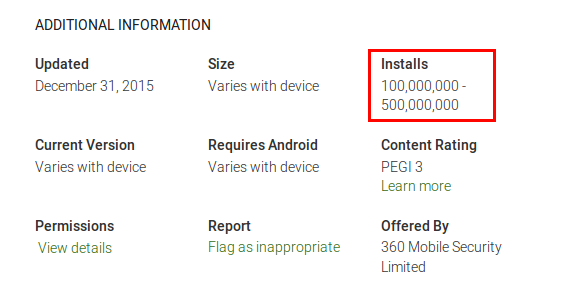
Lets take a look at 360 Security – Antivirus Boost
And yes their claim for 200 million users seems to be valid
As the app is free they include some ads … e.g. from vungle.com
What is vungle?
Vungle helps mobile application developers promote and monetize their apps through in-app video trailers. They enable developers to get a short, snappy video trailer made and distributed through their in-app mobile video platform. They also generate incremental revenue for developers by displaying video trailers inside of their apps. (Text from CrunchBase)
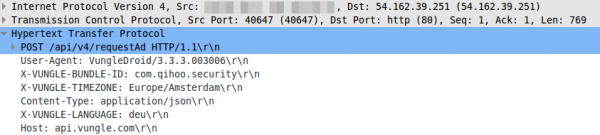
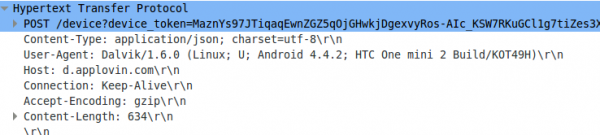
Lets take a look what their library does – it sends an HTTP post request in the clear
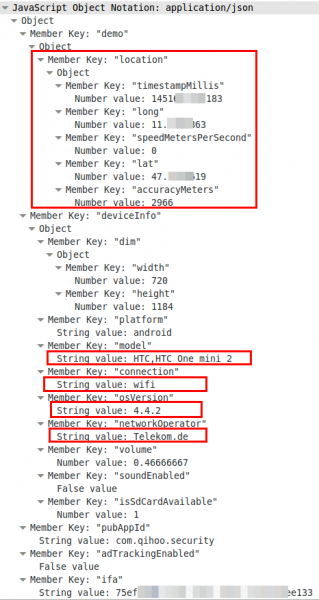
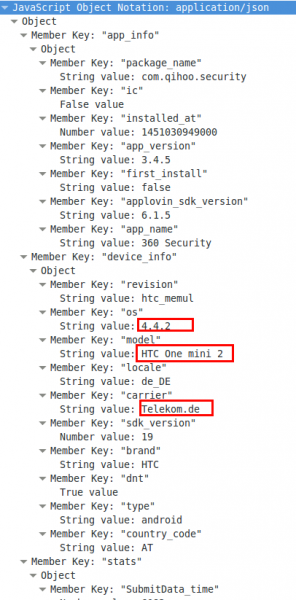
So far so good, but lets take a look at the body, which is a json file.
Oh nice, now we know the location, the mobile phone type, the Android version and the mobile provider. If you know which phone your target uses you now got his/her IP address and Android version for the exploit to inject. For 4.4.2 there should be some easily available. 😉
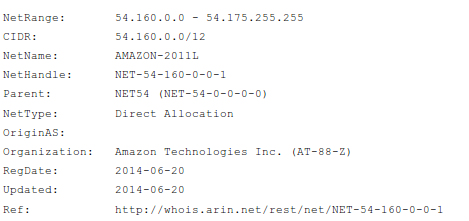
ps: the NSA does not need to track your location via the mobile operator in a foreign nation … they just look at the internet traffic which goes to AWS cloud to get your location.
Buts not the only ad network which the app includes:
Lets take a look at www.applovin.com .. the homepage looks similar to the first … hmm
Here the HTTP request again
oh, this time no location …. 🙁
“360 Security – Antivirus Boost” is just one test case … most apps which use ads libraries leak such information.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
32 queries. 0.114 seconds.