Howto capture traffic from a Mikrotik router on Linux
February 15, 2014
If you as I need to get some traffic from a Mikrotik router and /tool sniffer quick doesn’t cut it, as you need not just the headers the best way is stream the traffic to the a Linux box. The Mikrotik configuration is easy, just set the server you want to stream to:
/tool sniffer set streaming-enabled=yes streaming-server=<ip_of_the_server>
Configure a filter as you don’t want to stream everything:
/tool sniffer set filter-ip-address=<an_example_filter_ip>
and now you need only to start it with
/tool sniffer start
and check with
/tool sniffer print
if everything is running.
But now comes the part that is not documented that well. Searching through the internet I found some posts/articles on how to use Wireshark for capturing, but that does not work correctly – at least not for me.
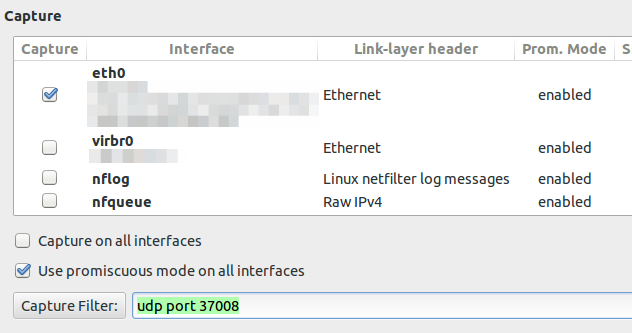
If you configure the capture filter to udp port 37008 to get everything the router sends via TZSP you will see following lines
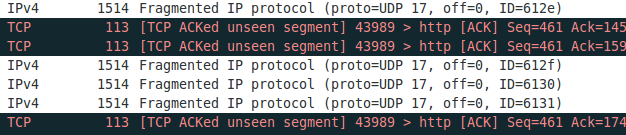
If you now set the display filter to show only TZSP these packets are not displayed any more. This packets contain information we need and I was not able to configure Wireshark 1.10.2 to work correctly. If you know how to get it to work, please write a comment. I changed my approach to use an other program to write the packets to disk and look at them later with Wireshark. And I found a program from Mikrotik directly which does that. Go to the download page and download Trafr and extract and use it like this:
$ tar xzf trafr.tgz
$ ./trafr
usage: trafr <file | -s> [ip_addr]
-s write output to stdout. pipe it into tcpdump for example:
./trafr -s | /usr/sbin/tcpdump -r -
ip_addr use to filter one source router by ip address
$ ./trafr test.pcap <ip_of_the_router>
After you stopped the program you can open the file in Wireshark and no packets are missing.
Bootable antivirus rescue CDs
January 19, 2014
There seams to be a virus wave here in Austria and Germany, don’t really know why but somehow many people click on the links and download the malware. Maybe its because the mail is a faked invoice from some well known (mobile) telecommunication providers and are written in good German – normally spam like this written in broken German. And it seams that the mail passed anti spam systems as I got the some mails on the cooperate account and at home .. normally I don’t get spam mails for month.
Anyway, while I was driving home today it was even in the local radio news .. one of the top items there. And when I was home a relative, which is not that close by called me and asked be how to get ride off that virus. He got infected as initially his anti virus didn’t detected it. I recommend him following link from Raymond. Its a comprehensive list of 26 bootable antivirus rescue CDs for offline scanning. I recommend him to use at least two of the following from the list.
- Bitdefender Rescue CD
- Kaspersky Rescue Disk
- F-Secure Rescue CD
- Windows Defender Offline
So if you get asked the same from your relative you don’t need to search further. 😉
At the Tone, the Time will be.
January 12, 2014
Last week we at work got a mail from CERT.at that 2 IP addresses in our AS where probably running misconfigured NTP Servers, which can be abused for DDoS attacks via NTP Reflection. But first we need to start with the background.
Background
In the last weeks multiple DDoS attacks were using NTP Reflection. The attackers are making use of the monlist commands, which is enabled on older versions of the NTP daemon. With that command it is possible to get a list of up to the last 600 hosts / ip address which connected to the NTP daemon. As NTP is UDP based, an attacker fakes its source IP address and the answer packet from the NTP daemon is send to the victim. Beside hiding the attackers IP addresses to the victim it amplifies the attack as the request packet is much smaller than the answer packet. The other problem with this monlist command is, that it releases potential sensitive information (the IP address of the clients using NTP)
How to verify you’re vulnerable?
First you need to find your NTP servers – and thats not so easy as it seams. E.g. our 2 reported NTP servers where not our official NTP servers … but more about that later. To find NTP Servers which are reachable from the Internet use e.g. nmap in a way like this:
sudo nmap -p 123 -sV -sU -sC -P0 <your_network/subnet_mask>
This will return for a linux ntp server something like this
Nmap scan report for xxxxx (xxxxxxxx)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v4
| ntp-info:
| receive time stamp: 2014-01-12T11:02:30
| version: ntpd [email protected] Wed Nov 24 19:02:17 UTC 2010 (1)
| processor: x86_64
| system: Linux/2.6.32-358.18.1.el6.x86_64
| leap: 0
| stratum: 3
| precision: -24
| rootdelay: 20.807
| rootdispersion: 71.722
| peer: 56121
| refid: 91.206.8.36
| reftime: 0xd67cedcd.b514b142
| poll: 10
| clock: 0xd67cf4be.9a6959a7
| state: 4
| offset: 0.042
| frequency: -3.192
| jitter: 0.847
| noise: 1.548
| stability: 0.163
|_ tai: 0
But you may find also something like this
Nmap scan report for xxxxx
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v4
| ntp-info:
|_ receive time stamp: 2014-01-12T11:02:55
from a system you had not on the list. After this deactivate and/or filter the services you don’t need – a running service which is not needed is always a bad idea. But surely you also want to know how to probe the NTP daemon for the monlist command – just like this:
ntpdc -n -c monlist <ip_address>
If the daemon is vulnerable you’ll get a list of ip address which connected to the daemon. If the NTP daemon is running on a Linux, Cisco or Juniper System take look at this page which describes how to configure it correctly.
But I guess you’re curious, which systems where running on the 2 ip addresses we got reported? They where Alcatel Lucent Switches which have the NTP daemon activated by default it seams. So its really important to check all your IP addresses not only the known NTP Servers.
Howto find all websites running on a given IP address
January 5, 2014
Sometimes you’ll (at leased if you’re like me 😉 ) want to know which other websites are hosted on the same server respectively the same IP address. The search engine Bing provides a nice feature for this. Just enter ip:50.57.15.204 to get a list of the website which Bing knows to run on that IP address.
But even better, Andrew Horton has done a Bash script which allows you to check that from the command line. This looks even better:
$ ./bing-ip2hosts www.theregister.co.uk
[ 50.57.15.204 | Scraping 11-13 von 13 | Found 9 | / ]]
1695693.r.msn.com
2549779.r.msn.com
forums.channelregister.co.uk
forums.theregister.co.uk
media.theregister.co.uk
m.theregister.co.uk
regmedia.co.uk
www.channelregister.co.uk
www.theregister.co.uk
Multiple consumer routers contain a backdoor
As hopefully many of my readers have already heard/read multiple consumer routers contain a backdoor, which allows the attacker to get the configuration of the router, which also contains the administrator password. I won’t rewrite here everything big IT news sites have already written. Here just the basics to get you up to speed if you didn’t hear it before:
- Eloi Vanderbeken found on his Linksys router WAG200G a process what was listening on TCP port 32764. After analyzing the code he figured out that it was possible to extract the configuration from the router over this process without knowing the password. The configuration contains also the password.
- After hey posted the information to the net, other users stepped forward and told him that other manufactures and models have the same backdoor. Don’t say “conspiracy theory” now. 😉
- On some routers the process is “only” listening on the internal network (which is also attackable over the users browser) but some are also reachable on the Internet. Scanning for this in the internet is easy with zmap .. only 45min for the whole IPv4 Internet address space.
- Click here to get the current list of affected routers – its a long list containing vendors like Cisco, Linksys, Netgear, Diamond, LevelOne
- To verify if your router is also affected download this Python Script (Linux has normally Python preinstalled on Windows you need to install it). And call it like this:
python poc.py --ip <IP-Address of your router>. If it found something you can extract the configuration by adding--print_confto the command line. - To check if the process is also reachable from the Internet use a Website like this.
Possible workarounds to get the hole fixed fast:
- On some routers you can configure a local firewall which allows you to block the Port 32764. Depending on your router this is possible for the Internet interface and/or the internal interface.
- Install a OpenSource software like OpenWRT.
- Install the new firmware release of your vendor when and if it is released … I wouldn’t wait for this. 😉
Howto install Teamviewer 9.x on Ubuntu >= 12.04 64bit (in my case 13.10)
January 2, 2014
Basically it is simple but the 64bit makes it a little bit more difficult. It is not logical from the outside but don’t use the 64bit version. Why? As described here distributions with multiarch support can’t resolve the ia32-libs packages. But there is a simple solution to this which is not described there, as adding an additional architecture doesn’t feel right.
Install gdebi (gdebi lets you install local deb packages resolving and installing its dependencies. apt does the same, but only for remote (http, ftp) located packages.):
sudo apt-get install gdebi
Download the 32bit version
wget http://www.teamviewer.com/download/teamviewer_linux.deb
Use gdebi to install and resolve the dependencies:
$ sudo gdebi teamviewer_linux.deb
Reading package lists... Done
Building dependency tree
Reading state information... Done
Building data structures... Done
Building data structures... Done
Requires the installation of the following packages: libxtst6:i386
TeamViewer (Remote Control Application)
TeamViewer is a remote control application. TeamViewer provides easy, fast and secure remote access to Linux, Windows PCs, and Macs.
.
TeamViewer is free for personal use. You can use TeamViewer completely free of charge to access your private computers or to help your friends with their computer problems.
.
To buy a license for commercial use, please visit http://www.teamviewer.com
Do you want to install the software package? [y/N]:y
Get:1 http://at.archive.ubuntu.com/ubuntu/ saucy/main libxtst6 i386 2:1.2.2-1 [13.8 kB]
Fetched 13.8 kB in 0s (0 B/s)
Selecting previously unselected package libxtst6:i386.
(Reading database ... 250452 files and directories currently installed.)
Unpacking libxtst6:i386 (from .../libxtst6_2%3a1.2.2-1_i386.deb) ...
Setting up libxtst6:i386 (2:1.2.2-1) ...
Processing triggers for libc-bin ...
Selecting previously unselected package teamviewer.
(Reading database ... 250454 files and directories currently installed.)
Unpacking teamviewer (from teamviewer_linux.deb) ...
Setting up teamviewer (9.0.24147) .
Thoughts on IPv6 /64 scanning and NDP cache size
December 24, 2013
Today I was talking with some friends about the possibility to make a DOS attack against an IPv6 router/switch if I was in the same /64 subnet by simply sending IPv6 NDP Packets to fill the neighbour cache on the router. But the question I was thinking than about was how many packets can I send e.g. over an 1Gbit link per second? How many entries will the neighbour cache need to hold if the timeout is e.g. set to 120 sec? How long would it take to scan the whole /64? So I sat down and looked at the questions.
How man packets can I send in one direction send over an 1Gbit Ethernet link?
The amount of packets which can be sent over a link depends on the size of the packets. The smallest ones used for calculation are 64byte in the IP world. We need to put that into a Ethernet frame which adds up to 84 octets Details can be found here. Which leads to following formula:
1000MbitPerSec / 8 Bits / 84 OctetsPerFrame= 1.488.095 FramesPerSec
As only one packet can be in a frame we can send 1.488.095 packets per second (often called: pps), which is also often called line speed or wire speed. The calculation is true for pure Ethernet, but I changes if you use VLAN Tags, QinQ or MPLS … in these cases take a look at this article.
How many entries will the neighbour cache need to hold if the timeout is e.g. 120 sec?
So now we know how many packets a can send at most and forget that we need some additional bytes for the NDP, which makes it easy to set the limit for the neigbour cache of our router.
1.488.095 PacketsPerSecond * 120 SecondsTimeout = 178571400 entries = 178 Million Entries
Lets say that this is only a RAM problem and everything else would work. Each entry contains a least the IP address and the MAC address. (There would be an optimization possible in only to store the host part of the IP address). An IPv6 address has 128bit = 16byte and the MAC address has 48bit = 6byte which leads to a total of 22byte per entry. A router needs 3,6Gbyte of RAM to store this table … not impossible but not common also. 😉
How long would it take to scan the whole /64?
And as bonus question we talk on how long it would take to scan that many IP addresses. First we need to get the amount of IP addresses a /64 can hold.
2^64 = 18.446.744.073.709.551.616 = 1,844674407×10¹⁹ IP Addresses
We know that we can scan 1.488.095 IP addresses per second which leads to
1,844674407×10¹⁹IPaddresses / 1488095 packetsPerSec / 60/ 60 / 24 / 365 = 393081 years
Ok not practical. But wait … we need only to scan for /48 IP addresses as the host part is derived from the MAC … this makes only 2,814749767×10¹⁴ IP addresses
2,814749767×10¹⁴IPaddreses / 1488095 packetsPerSec / 60/ 60 / 24 / 365 = 6 years
Much smaller but still too long for my spare time. 😉
Some thoughts on NFS
December 23, 2013
In the last weeks I was working (from time to time 😉 ) on a new setup of my NAS at home. During this I learn some stuff I didn’t know about NFS which I want to share here. I assume that you got the basis NFS stuff working or know how it works and want some addition tips and ticks
- How to query a NFS server for the exported directories and the settings? Easy, use
showmount -e <servername>. Here an example:
$ showmount -e 10.x.x.x
Export list for 10.x.x.x:
/data/home 10.x.x.0/255.255.255.0 - Use fsid – why?
- NFS needs to be able to identify each filesystem that it exports. Normally it will use a UUID for the filesystem (if the filesystem has such a thing) or the device number of the device holding the filesystem (if the filesystem is stored on the device). If you want to an export different file system (e.g. replacement HDD) the fsid changes and you’re clients have to remount (as they have a stale NFS mount). Read more on this topic here.
- Some file systems don’t have a UUID, e.g. encfs does not … use a separate fsid for each export!
- You can export multiple file system with one mount request by the client, if you use nohide. Normally, if a server exports two file systems one of which is mounted on the other, then the client will have to mount both file systems explicitly to get access to them. If it just mounts the parent, it will see an empty directory at the place where the other file system is mounted. That file system is “hidden” – if you don’t want that use nohide, like in this example:
/data/media 10.x.x.0/255.255.255.0(fsid=1,rw,async,no_subtree_check)
/data/media/movies 10.x.x.0/255.255.255.0(fsid=2,rw,async,no_subtree_check,nohide) - If you changed
/etc/exportsyou don’t need to restart your NFS daemon. If the init script provides a reload thats good – if not useexportfs -rav.
So far that are my new learned tips and tricks … I think there was one more but I can’t remember it now. Will add it later if I remember.
OeBB Railjet WiFi second, even bigger security problem
November 5, 2013
Yesterday I wrote about the the information leak at the Railjet Wifi. Today I’m traveling back to Tirol again with a Railjet and I found something other disturbing. I believe its even more problematic as it concerns the mail system. I used a openssl client to check various SSL and TLS connections to my servers, and when I called following:
$ openssl s_client -connect smtp.xxx.at:25 -starttls smtp
I got something I didn’t expect:
CONNECTED(00000003)
didn't found starttls in server response, try anyway...
Hey, my server does not support STARTTLS? I’m sure it does. I did a SSH to a server of mine and checked typed the same command and got my server certificate complete with chain. So something is not right here. I switched to Wireshark (which is running all the time … Ok, I launched it 😉 ) and looked at the traffic:
server: 220 profinet.at SurgeSMTP (Version 6.3c2-2) http://surgemail.com
client: EHLO openssl.client.net
server: 250-profinet.at. Hello openssl.client.net (194.112.182.213)
server: 250-AUTH LOGIN PLAIN
server: 250-ETRN
server: 250-X-ID 5043455352563431333833323030373135
server: 250-SIZE 50000000
server: 250 HELP
client: STARTTLS
server: 500 Sorry SSL/TLS not allowed from (194.112.182.213)
Hey? Thats not my mail server. Its not my IP address and its sure not the mail server software I use. WTF?
Someone is intercepting my SMTP traffic and if my mail clients would use the default setting (use TLS if possible) I would now send my login data (which is for most people the same as for fetching mails) in the clear over an unprotected WiFi. Block port 25 if you have fear of spammers, but don’t force unencrypted traffic over a open wifi.
Anyway whats that profinet.at stuff …. can’t be profi as in professionals. The Whois tells following:
Domaininhaber:
Organisationsname: OeBB Telekom Service GmbH
Strasse: Bruenner Strasse 20
PLZ: 1210
Stadt: Wien
Land: AT
Ok, thats the OeBB by itself. Real experts. 😉
So keep an eye on your SMTP/IMAP configuration and make sure you’re forcing TLS/SSL otherwise someone in the same train is seeing your data.
Information Leak due OEBB Railjet WiFi
November 4, 2013
Today I traveled with the OEBB Railjet which provides a free WiFi. As the journey took some hours I had time to look at my networks traces and found something. After the captive portal with the Terms of Services was acknowledged, a page with some infos is shown. One of the infos is the original URL the user requested. If the users clicks on the link a separate tab opens with the page. The problem is that the URL the browser was given to access this info page has following format:
http://10.20.43.1:4990/www/portal/index.html?res=notyet&uamip=10.20.43.1&uamport=3990&challenge=7e623f476a0cd811b414ad6aa9cfce13&called=00-C0-3A-9D-55-E8&mac=xx-xx-xx-xx-xx-xx&ip=10.20.43.33&nasid=nas01&sessionid=5277d1c60000000b&userurl=http%3a%2f%2fwww.orf.at%2f
Which is sent as referrer to the original requested page if you click onto the link. As you see this referrer contains the full MAC address of the requesting device. Normally the MAC address is only visible via Layer 2 but with the information leak in my case www.orf.at knows my MAC address and if I have already gotten a cookie, they could add now my MAC to the list of know IDs. Ok, I guess the ORF doesn’t do that, but others might.
A solution would be simple for the OEBB, but until then don’t click on this link – type the URL again.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
30 queries. 0.074 seconds.





