Bootable antivirus rescue CDs
January 19, 2014
There seams to be a virus wave here in Austria and Germany, don’t really know why but somehow many people click on the links and download the malware. Maybe its because the mail is a faked invoice from some well known (mobile) telecommunication providers and are written in good German – normally spam like this written in broken German. And it seams that the mail passed anti spam systems as I got the some mails on the cooperate account and at home .. normally I don’t get spam mails for month.
Anyway, while I was driving home today it was even in the local radio news .. one of the top items there. And when I was home a relative, which is not that close by called me and asked be how to get ride off that virus. He got infected as initially his anti virus didn’t detected it. I recommend him following link from Raymond. Its a comprehensive list of 26 bootable antivirus rescue CDs for offline scanning. I recommend him to use at least two of the following from the list.
- Bitdefender Rescue CD
- Kaspersky Rescue Disk
- F-Secure Rescue CD
- Windows Defender Offline
So if you get asked the same from your relative you don’t need to search further. 😉
At the Tone, the Time will be.
January 12, 2014
Last week we at work got a mail from CERT.at that 2 IP addresses in our AS where probably running misconfigured NTP Servers, which can be abused for DDoS attacks via NTP Reflection. But first we need to start with the background.
Background
In the last weeks multiple DDoS attacks were using NTP Reflection. The attackers are making use of the monlist commands, which is enabled on older versions of the NTP daemon. With that command it is possible to get a list of up to the last 600 hosts / ip address which connected to the NTP daemon. As NTP is UDP based, an attacker fakes its source IP address and the answer packet from the NTP daemon is send to the victim. Beside hiding the attackers IP addresses to the victim it amplifies the attack as the request packet is much smaller than the answer packet. The other problem with this monlist command is, that it releases potential sensitive information (the IP address of the clients using NTP)
How to verify you’re vulnerable?
First you need to find your NTP servers – and thats not so easy as it seams. E.g. our 2 reported NTP servers where not our official NTP servers … but more about that later. To find NTP Servers which are reachable from the Internet use e.g. nmap in a way like this:
sudo nmap -p 123 -sV -sU -sC -P0 <your_network/subnet_mask>
This will return for a linux ntp server something like this
Nmap scan report for xxxxx (xxxxxxxx)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v4
| ntp-info:
| receive time stamp: 2014-01-12T11:02:30
| version: ntpd [email protected] Wed Nov 24 19:02:17 UTC 2010 (1)
| processor: x86_64
| system: Linux/2.6.32-358.18.1.el6.x86_64
| leap: 0
| stratum: 3
| precision: -24
| rootdelay: 20.807
| rootdispersion: 71.722
| peer: 56121
| refid: 91.206.8.36
| reftime: 0xd67cedcd.b514b142
| poll: 10
| clock: 0xd67cf4be.9a6959a7
| state: 4
| offset: 0.042
| frequency: -3.192
| jitter: 0.847
| noise: 1.548
| stability: 0.163
|_ tai: 0
But you may find also something like this
Nmap scan report for xxxxx
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v4
| ntp-info:
|_ receive time stamp: 2014-01-12T11:02:55
from a system you had not on the list. After this deactivate and/or filter the services you don’t need – a running service which is not needed is always a bad idea. But surely you also want to know how to probe the NTP daemon for the monlist command – just like this:
ntpdc -n -c monlist <ip_address>
If the daemon is vulnerable you’ll get a list of ip address which connected to the daemon. If the NTP daemon is running on a Linux, Cisco or Juniper System take look at this page which describes how to configure it correctly.
But I guess you’re curious, which systems where running on the 2 ip addresses we got reported? They where Alcatel Lucent Switches which have the NTP daemon activated by default it seams. So its really important to check all your IP addresses not only the known NTP Servers.
Howto find all websites running on a given IP address
January 5, 2014
Sometimes you’ll (at leased if you’re like me 😉 ) want to know which other websites are hosted on the same server respectively the same IP address. The search engine Bing provides a nice feature for this. Just enter ip:50.57.15.204 to get a list of the website which Bing knows to run on that IP address.
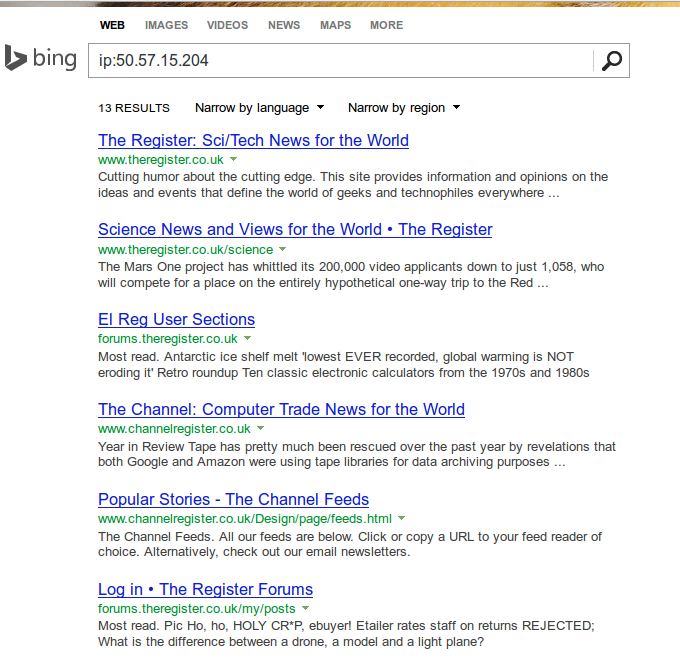
But even better, Andrew Horton has done a Bash script which allows you to check that from the command line. This looks even better:
$ ./bing-ip2hosts www.theregister.co.uk
[ 50.57.15.204 | Scraping 11-13 von 13 | Found 9 | / ]]
1695693.r.msn.com
2549779.r.msn.com
forums.channelregister.co.uk
forums.theregister.co.uk
media.theregister.co.uk
m.theregister.co.uk
regmedia.co.uk
www.channelregister.co.uk
www.theregister.co.uk
Multiple consumer routers contain a backdoor
As hopefully many of my readers have already heard/read multiple consumer routers contain a backdoor, which allows the attacker to get the configuration of the router, which also contains the administrator password. I won’t rewrite here everything big IT news sites have already written. Here just the basics to get you up to speed if you didn’t hear it before:
- Eloi Vanderbeken found on his Linksys router WAG200G a process what was listening on TCP port 32764. After analyzing the code he figured out that it was possible to extract the configuration from the router over this process without knowing the password. The configuration contains also the password.
- After hey posted the information to the net, other users stepped forward and told him that other manufactures and models have the same backdoor. Don’t say “conspiracy theory” now. 😉
- On some routers the process is “only” listening on the internal network (which is also attackable over the users browser) but some are also reachable on the Internet. Scanning for this in the internet is easy with zmap .. only 45min for the whole IPv4 Internet address space.
- Click here to get the current list of affected routers – its a long list containing vendors like Cisco, Linksys, Netgear, Diamond, LevelOne
- To verify if your router is also affected download this Python Script (Linux has normally Python preinstalled on Windows you need to install it). And call it like this:
python poc.py --ip <IP-Address of your router>. If it found something you can extract the configuration by adding--print_confto the command line. - To check if the process is also reachable from the Internet use a Website like this.
Possible workarounds to get the hole fixed fast:
- On some routers you can configure a local firewall which allows you to block the Port 32764. Depending on your router this is possible for the Internet interface and/or the internal interface.
- Install a OpenSource software like OpenWRT.
- Install the new firmware release of your vendor when and if it is released … I wouldn’t wait for this. 😉
Howto install Teamviewer 9.x on Ubuntu >= 12.04 64bit (in my case 13.10)
January 2, 2014
Basically it is simple but the 64bit makes it a little bit more difficult. It is not logical from the outside but don’t use the 64bit version. Why? As described here distributions with multiarch support can’t resolve the ia32-libs packages. But there is a simple solution to this which is not described there, as adding an additional architecture doesn’t feel right.
Install gdebi (gdebi lets you install local deb packages resolving and installing its dependencies. apt does the same, but only for remote (http, ftp) located packages.):
sudo apt-get install gdebi
Download the 32bit version
wget http://www.teamviewer.com/download/teamviewer_linux.deb
Use gdebi to install and resolve the dependencies:
$ sudo gdebi teamviewer_linux.deb
Reading package lists... Done
Building dependency tree
Reading state information... Done
Building data structures... Done
Building data structures... Done
Requires the installation of the following packages: libxtst6:i386
TeamViewer (Remote Control Application)
TeamViewer is a remote control application. TeamViewer provides easy, fast and secure remote access to Linux, Windows PCs, and Macs.
.
TeamViewer is free for personal use. You can use TeamViewer completely free of charge to access your private computers or to help your friends with their computer problems.
.
To buy a license for commercial use, please visit http://www.teamviewer.com
Do you want to install the software package? [y/N]:y
Get:1 http://at.archive.ubuntu.com/ubuntu/ saucy/main libxtst6 i386 2:1.2.2-1 [13.8 kB]
Fetched 13.8 kB in 0s (0 B/s)
Selecting previously unselected package libxtst6:i386.
(Reading database ... 250452 files and directories currently installed.)
Unpacking libxtst6:i386 (from .../libxtst6_2%3a1.2.2-1_i386.deb) ...
Setting up libxtst6:i386 (2:1.2.2-1) ...
Processing triggers for libc-bin ...
Selecting previously unselected package teamviewer.
(Reading database ... 250454 files and directories currently installed.)
Unpacking teamviewer (from teamviewer_linux.deb) ...
Setting up teamviewer (9.0.24147) .
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
27 queries. 0.058 seconds.





