New RTF macro Malware from the Dridex gang
March 23, 2016
In the aftermath of Locky many companies started blocking EXE files directly attached or in ZIP files on their mail gateways. Some moved further and started removing active content in DOC, XLS, and other MS Office files. Today an old file type got used again and the virus scanner hit rate was really bad again.
Details
The Malware gets delivered by mails with a RTF file attached (which is often used in the medical area), which e.g. looks like this:
The company exists if you check before opening the attachment. Normally bad RTF files did contain EXE files within them, but not this time. This time it contains highly obfuscated macro code, which MS Word executes. which looks like this:
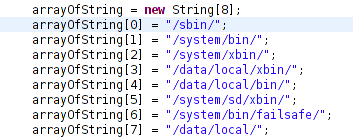
Sub Document_Open()
Dim HGFDSXDSFVV
HCFDSFDSFB = "hel"
VDSFCDSJ = "qweee"
GoTo PQOycAsH
Dim XJwoBhgN As String
Open "JQJLAG.ANU" For Binary As 66
GoTo pKlIahvf
Dim wVyQZrAv As String
Open "CTTBNH.FEB" For Binary As 18
Put #18, , wVyQZrAv
Close #18
pKlIahvf:
Put #66, , XJwoBhgN
...
which then did use WScript.exe to download a file from
http://wrkstn09.PEORIASENIORBAND.COM/dana/home.php
other researchers report followingURLs:
http://connect.businesshelpa-z.com/dana/home.php
http://wrkstn09.satbootcampaz.com/dana/home.php
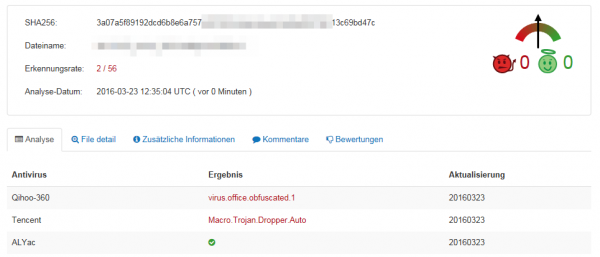
The file is called fuckyourself.ass which is in reality a EXE file, which contains the Malware itself. Uploading this (we’re one of the first it seems 😉 ) to Virustotal showed that only 2 virus scanner detected the Malware:
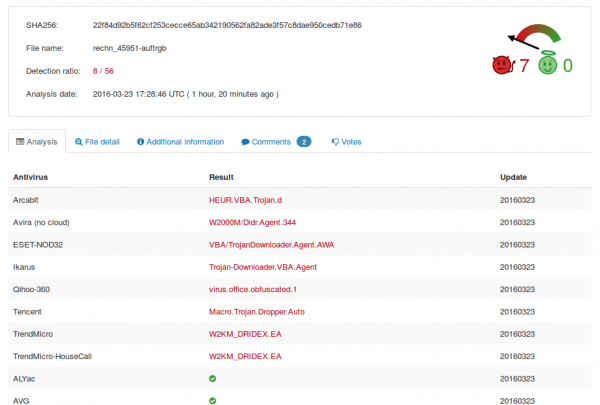
Some hours later and after others saw the file also in the wild and as we reported the file to virus vendors it looks a little bit better, but not good – for the dropper 8/56:
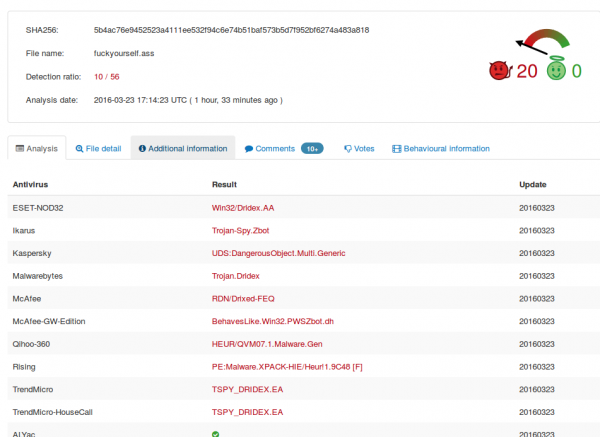
and for the malware itself 10/56:
I normally don’t write about single viruses, but this one is a show case for some opinions I’ve for some time now.
- Forget about normal virus detections – sure keep it on Windows system but don’t count on it.
- You really need to implemented procedures as described in this early blog post.
- It gets more and more important to implement a sand-boxing technology, where all your files which get to you’re company from the internet gets executed / opened. And this means every file .. not only executables. There are also sand boxing technologies that run on premise or in an European data center.
- Bigger companies can mitigate that problem easier, the problem child are home users and small companies.
I don’t have a good solutions for home users so far … maybe someone knows something that I could recommend the Windows home users I know.
Blue Code mobile payment – All show and no substance [3. Update]
March 20, 2016
[Update]
The vendor contacted me and told me they are working on a fix right now, which should be released shortly. I also got contacted by 3rd parties and they asked if the whole system is broken or not. To make it clear for the non experts. My findings are “easily” fixable and I can’t say anything about the whole system as I didn’t look at it. The vendor has fixed following 2 problems
- bad HTTPS setup for the webservice
- client certificates length (now RSA2048).
[/Update]
Shopping in my local super market I saw an other customer paying with a barcode on the display of his mobile. Looking a little bit around I saw also the ad for it. The service/product is called Blue Code and is from a local company Secure Payment Technologies GmbH based in Innsbruck and is used by some big retail stores.
As you know me, I like to know how stuff around me works and how secure they are. Searching around a little bit in the Internet I didn’t find anything above marketing stuff on how the system works. This intrigued me, as not documented normally means there are some skeletons in the closet. So this post is about the my look into the system.
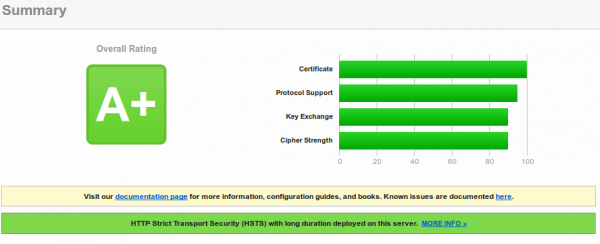
I normally start with the basics. In this case checking the HTTPS stuff and taking a look at the Android App. Both are done without installing the App on one of my devices.
First Look
Looks good, but I saw something additional:
Yes, that’s a wild card certificate. So even if they have an other more secure TLS setup for the payment stuff this certificate would be valid for it. That’s bad security practise. But maybe they use an other domain for the payment stuff or do certificate pinning. So I downloaded the APK. Use this nice site to download the Blue Code APK on your desktop for analysing. APK files are just ZIP files with a special structure, so I’ve extracted the files and took a look at the strings. I took a look at the last 3 versions which I could download.
I found something interesting in the Blue Code_v1.2.0_apkpure.com.apk (the oldest of the three) …
$ strings classes.dex | grep http
[Copyright (c) 2000-2014 The Legion of the Bouncy Castle Inc. (http://www.bouncycastle.org)
...
#http://202.4.114.227:8080/merchants
...
https://sdk.hockeyapp.net/
https://support.bluecode.com/a/
The Bouncy Castle is a crypto library for Java in this case and HockeyApp is for a platform for application development. The IP address is more interesting, it belongs to an ISP from Bangladesh. Hey? The company is from Tirol / Austria – outsourced development? The Blue Code_v1.3.1_apkpure.com.apk and Blue Code_v1.3.2_apkpure.com.apk does not contain that string. Also the crypto lib seems to be changed. Anyway the host was not reachable from my computer so I think that’s legacy host that got removed.
So far it seems no other domains are in the App. A search for sub domains shows following:
$ strings resources.arsc | grep bluecode.com
...
https://www.bluecode.com/login
mobile-ca.bluecode.com
mobile-api.bluecode.com
...
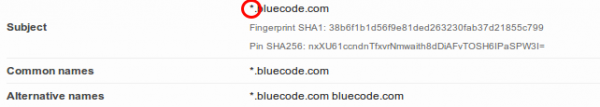
Oh, that TLS setup looks not that good:
 hm .. lets take a look at the certificate …. oh … its the same:
hm .. lets take a look at the certificate …. oh … its the same:
So different servers use the same wild card cert … that’s really “good” security practise :-). Are TLS certs too expensive? https://mobile-api.bluecode.com uses also the same certificate and the same TLS setup as https://mobile-ca.bluecode.com (run on the same IP address).
Both hosts look like web services … so I guess the App talks with them, which means the website has a better security than the payment web services? I should look deeper into it.
Note the vendor: Certificate pinning helps only if you don’t use the same wild card certificate for all services, this way if you’re web server gets compromised an attacker can use that for fake your payment webservices.
The setup for a deeper look
Now it is time to look at the traffic the App generates while talking to its servers. Looking at the files packed into the apk file I saw that under /res/raw/ multiple CA certificates (including the CA for the web site and service certificate) got shipped. So I’ll guess there is some certificates pinning done.
So I got my old Nexus 7 out from a storage drawer, and did following to it:
- Unlock Bootloader
- Factory restore with Android 5.1.1
- Rooted it
- Installed Xposed Framework
- Installed JustTrustMe and SSLUnpinnig Modules for Xposed
After that I installed Burp and configured it as an HTTPS proxy on my PC. I’ve already shown how to do that in this blog post. After that I needed only to do following on the tablet:
- configure Burp as the proxy for the Wifi connection
- install the the Burp CA on the tablet
- download and install the BlueCode App.
First launch of the App
At first launch you need to provide a PIN code for something – it was not for what I first thought, but more about that later. After entering you PIN twice the App starts talking with the server.
The two requests to
https://www.bluecode.com/json/support_mobile_app_pages.jsonandhttps://www.bluecode.com/json/support_mobile_allgemein.json
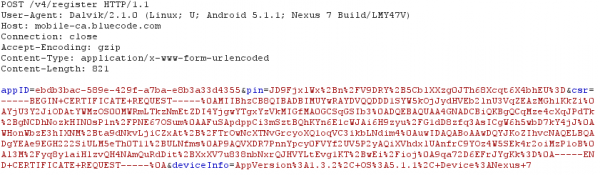
return only some text for the App. But the next request is more interesting, it is a certificate signing request (CSR):
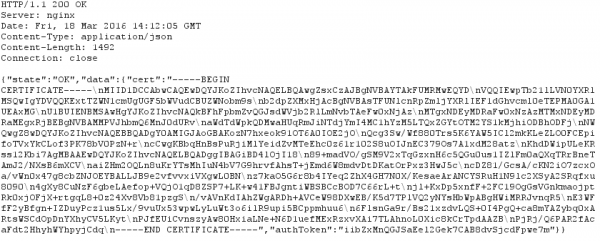
And there is also a parameter “pin” in the request (salted hash?). Looking at the CSR it seems to be a little short. Anyway the response from the server is a certificate.
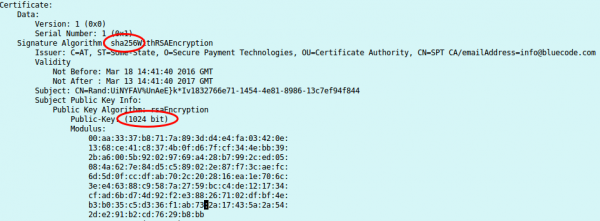
Taking a look at that certificate shows following:
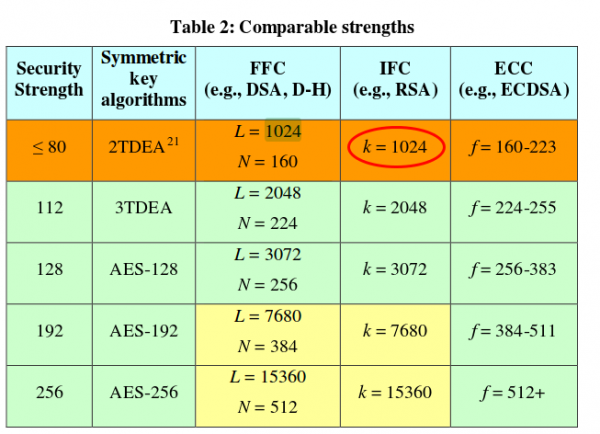
I know now why it looked that short, its a 1024 RSA certificate, but signed with SHA256. Someone didn’t understand crypto here. Signing an RSA1024 Key with SHA256, does not make any sense. If you won’t believe me take a look what NIST(National Institute of Standards and Technology) says. From the PDF:
RSA 1024 has a security of lower than 80bit and should not be used for years now!!!
After this request, the next request gets send to mobile-api, with the authToken the App got from the previous request.
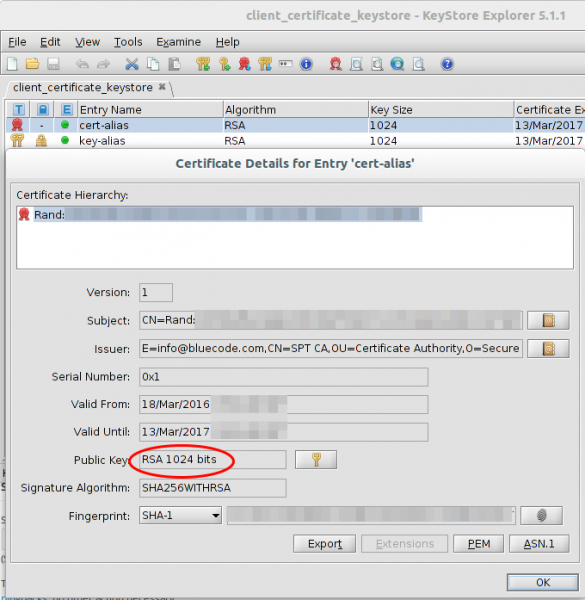
This request fails with the HTTPS proxy as the App makes a TLS client authentication, for which my proxy does not have the private key. After some short searching I found it under: /data/data/com.spt.bluecode/app_Certificates/client_certificate_keystore
I copied the file to my computer and tried to open it … I “just” need to get the private key now.
Lets stop with looking into the security of Blue Code for mow, as the weekend is almost over and the weather was really good and I needed to go ski montaineering also. But maybe I’ll look later deeper into the system …. So far I found following security problems:
- bad HTTPS setup for the webservice
- wildcard certificates used over multiple servers/services
- client certificates length (RSA 1024bit) which should not be used for years
So many security problems after looking at it only for some hours does not bode well ….
[Update]
It seems the software has a check that should detect if a devices is rooted …. does not seem to work in my case, maybe I don’t have that directories on my system … 😉
[\Update]
ps: Has someone of you documentation on the protocol of Blue Code? This would allow a high level check and theoretical security check without looking at the traffic.
Austrian Mobile Phone Signature is vulnerable against phishing and MitM attacks
February 1, 2016
Update: As some people asked. I’m not saying that the mobile phone signature is not good. It is much better than simple username and password and it protects against attacks that work against username/password. Specially as many users reuse their passwords.
Talking with various people about the Two Factor Authentication (2FA) which is used in Austria to access public services led to my impression that most people think that the system is really secure. While it is more secure than a simple user/password combination its by far not that secure. In this post I’ll show how a simple phishing and man in the middle attack can be performed. This is no 0day attack or something that runs through the media, it is just showing a design weakness which is not toughed up by mitigating techniques.
For your information: Most attackers don’t use 0days to get into systems, (spear) phishing is much easier and cheaper. The problem is that most companies and government agencies don’t take it seriously – as this case will show.
After showing the attack, I’ll provide methods to mitigate that kind of attacks – some are really easy and I don’t know why there are not deployed.
Background
Some text parts from the offical “Mobile Phone Signature or Citizen Card” webpage. The “important” parts are highlighted:
There are two alternative forms of the Citizen-Card functionality:
- Mobile Phone Signature: This requires a ready-to-receive mobile phone. The Mobile Phone Signature works with all mobile phones and is free of charge.
- Smart card: This requires a smart card with activated Citizen Card functionality (e.g. e-card) and a smart-card reading device.
Both alternatives can be used for the creation of legally valid signatures in online procedures. These signatures are legally equivalent to handwritten signatures. This way, the mobile phone and your activated e-card become your virtual ID, which can be used quite similar to your driving license. You have also the possibility to sign documents or invoices electronically with your Mobile Phone Signature or Citizen Card.
Yes you read correctly it is a qualified signature – which is:
The highest quality level for an electronic signature. Electronic Signature Act (SigG) § 4 declares that a qualified electronic signature is the legal equivalent of a written signature (with only a few exceptions such as e.g. Notary records).
So if an attacker is able to fake the signature he can get really far …..
Claims by the operator
From their offical “Mobile Phone Signature or Citizen Card” webpage:
Mobile Phone Signature and Citizen Card are particularly reliable methods to identify oneself on the Internet. Both provide high security against
- theft of access codes (such as phishing)
- attacks through the network (Man in the Middle)
- attacks on the computer (for example viruses)
…. hm that’s bold …. we should take a look at it ….
Basics
There is no legal difference between the signatures so most citizens by far took the easier and cheaper one, which is the mobile phone signature. So lets take a short look at how the mobile phone signature works from the user perceptive – which is enough for our purpose and attack.
- Go to a homepage which allows you to login via mobile phone signature
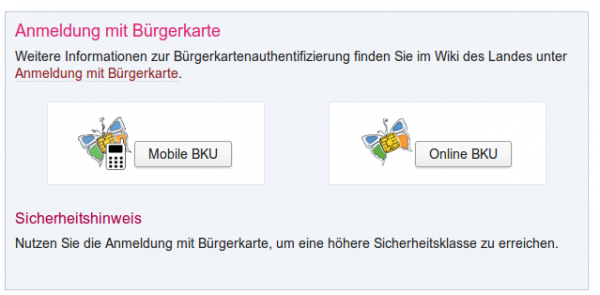
- After clicking on the “Mobile BKU”, I need to input my phone number and my signature password. The darker grey area is provided by the https://www.handy-signatur.at/mobile/https-security-layer-request/ website and not by the site I want to access.
Update: Some sites redirect to www.handy-signatur.at and some include it as an iFrame.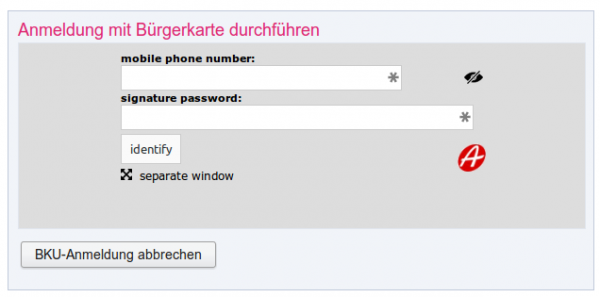
- If these entries are correct I get a SMS, which contains a TAN which I need to enter into the website. The SMS looks like this:
mobile phone signature
reference value: yt7Zqb8aTZ
TAN: 3As3Rz
(valid for 5 min.)
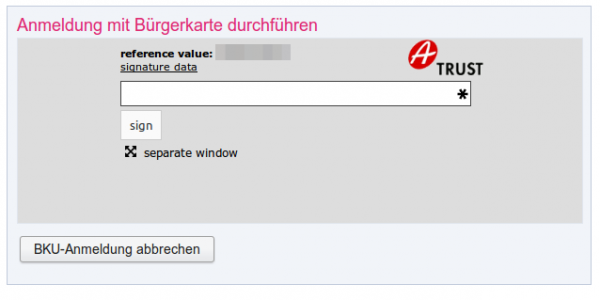
- You’re logged in.
The attack
This attack assumes that the user is using a separated device to receive the SMS … otherwise the attack would be even easier. Following diagram shows the steps need to impersonate a user. 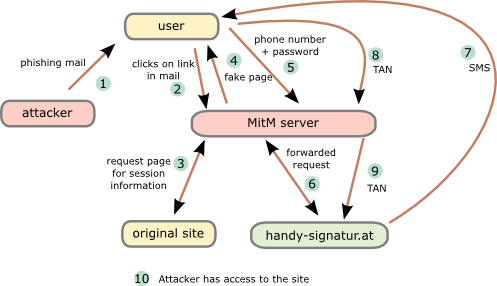
- The attacker sends a phishing email to the user. To make it more real lets be more specific. The attacker tells the user that there is something wrong with his taxes and that he needs to log into “finanz online” (tax and revenue office online portal) to fix it.
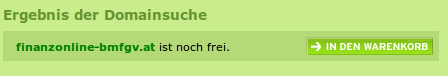
- The user clicks onto the link “finanzonline-bmfgv.at” or “finanzonline-bmf.at” which looks like the real one and even has a HTTPS certificate. How?
Getting a domain validation certificate (and often free e.g. startssl or let’s encryt) is really simple and the domains are still vacant.

- The Man in the Middle (MitM) server requests a page from the site we want to log into. It is not necessary that this is the “finanz online” site. It can be any other which uses mobile phone signature and the users has access to. The request/response are needed to get the correct link/parameters for the request to the mobile phone signature server.
- The MitM server sends the user a fake “finanz online”. The mobile phone signature frame is relayed through the MiTM server which changes the traffic accordingly.
- The user enters the phone number and password and sends it to the MitM server,
- which forwards the data to the mobile phone signature server.
- The mobile phone signature server sends a SMS to the user,
- which the user enters into the HTML form and sets to the MitM server.
- The MitM servers sends that to the mobile phone signature server,
- which redirects him to the side he wants to get to.
Important: That does not to be the site used for the phishing, as the SMS contains no information for the user to which site he authenticates. - As nice add-on …. provide the user with a page that reports that the email was send in error and that everything is ok with his taxes. 😉
That’s not that complicated … it is done against online banking sites every day of the week and the mTAN for a banking can not be used for various other sites and so trick the user into thinking its only a “unimportant” site he is loggin into.
From the claims of the operator the first 2 are not true. And also the third is not valid, everything an attacker is able to do via a phishing attack is also possible via malware on the computer. He just needs to install his own CA onto the system and is so able to redirect the traffic to its own servers. In this case the attacker does not even need to register a domain or an official TLS certificate. So all 3 claims are not correct.
Mitigation techniques
Here are some mitigations techniques. From simple to more complicated to implement:
- Tell the user in the SMS to which service he is authenticating for.
This allows the user to make sure his authentication is used for the service he wants to sign in. - Write the IP address and/or the provider name in the SMS to the user. Also add the country the IP address belongs to.
If I’m a Telekom Austria or UPC customer at home I know that, or at least I know that I’m not a China Telekom customer. - Send an email to user that he is used a new ISP, if the IP address is from an AS that does not match any old one.
This way the user at least knows that something wrong happend and is maybe able to prevent something or go the police. - With cooperation from the Austrian mobile phone providers it is possible to check if the phone is currently registered in the same country as the computer (SS7 network).
Following techniques need software on the computer:
- Provide a browser add-on which stores a secure hashed version of the signature password and checks every browser edit field if the mobile phone signature got entered into an 3rd party website. This also makes sure that the user is not using the password e.g. for facebook. 😉
- Browser add-on connects periodically (e.g. at the start of the browser) to the mobile phone signature server. If a login is performed from an other network/country block it or warn the user in the SMS.
All of the above won’t prevent all possible phishing attacks, but they will make them much much harder! As written in the beginning of this post, this attack is not some remarkably new one. It’s just about thinking the attack vectors through and some mitigations against them. I hope this post leads to a better security of the mobile phone signature server and all users and provides which use it.
Lock out of possible customers for your online shop by bad HTTPS configuration
November 1, 2015
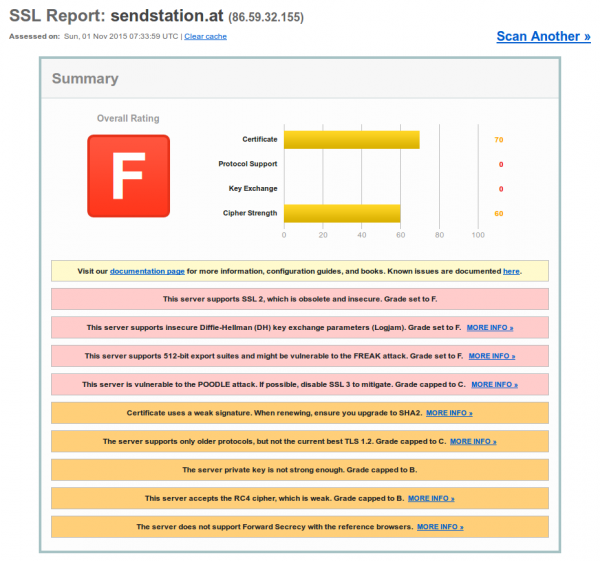
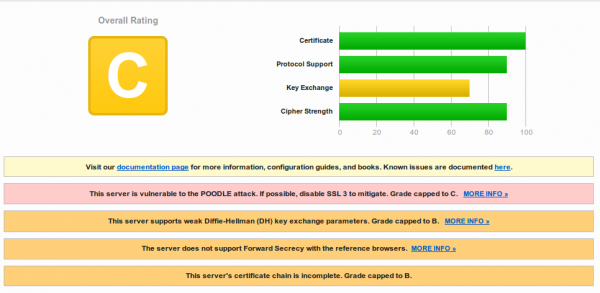
As I wanted to send a registered mail today, I did a fast google search if this is now also possible online in Austria. I found a news article what said that sendstation.at provides such a service .. so I clicked on the link and got an error message in Firefox that the HTTPS connection is not Ok. A check at SSL Labs shows that … newer seen something bad like this:
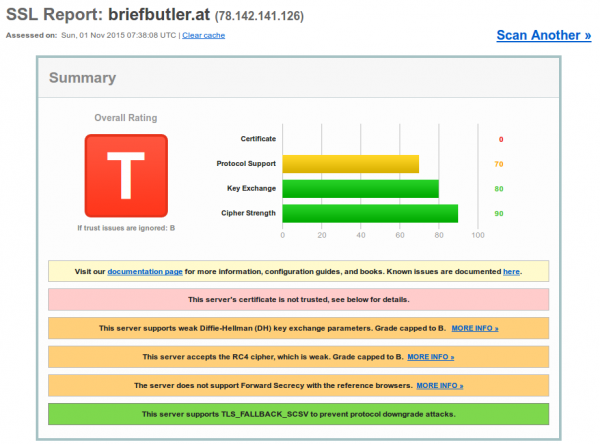
Ok, the news article was a bit older so I though lets check if the site is still in commission. So after excepting the error I was redirected to briefbutler.at and got again an error message in Firefox. And the SSL test shows that this time the configuration of the TLS is better, but the root is from A-Trust and least my Firefox, Chrome and SSL Labs don’t have that Certificate in the trust store.
Not sure how many customers this site gets .. maybe its in the Windows Trust Store and that’s ok from them if IE customers can visit them. Who needs more customers. The lesson learned here should be to check your HTTPS not only with your PC – check with other devices and services like https://www.ssllabs.com/ssltest/.
Howto configure a TG588 from A1 Telekom as VDSL modem and a Mikrotik device as router
September 11, 2015
Our big nation provider A1 Telekom went ahead and provided our house as first provider with VDSL – hoped FTTH makes the race … but anyway VDSL is better than the old stuff I had before. So I went ahead and ordered it and I got send an TG588 modem/router where you can almost configure nothing. e.g. UPNP is enabled and you can’t even deactivate it – when was it a good idea that a clients tells a firewall what to do in the first place? So I had to 3 options
- Buy a VDSL router like FRITZ!Box 3390, which is also a home router where I don’t like the configuration methods and feature set
- Buy a VDSL modem/bridge like Vigor130, and connect via a real router over pppoe. But the system is not on the A1 Telekom vectoring devices whitelist. No change for vectoring than ….
- Get the TG588 to play only modem and let my real router to do pppoe tunnel.
As you most likely already guested I opt for the last one. This howto shows you how to configure the TG588 as modem and an Mikrotik router as router (could be any other devices that supports pppoe in client mode). I was not that easy to gather all this information and so it maybe helps others to save time.
First lets connect the TG588 to the telephone line and the Mikrotik with one interface (in my case ether0) to it. Let everything boot up and connect your PC to the Mikrotik clients ports (in the default config). Log into the Mikrotik and configure the interface to the modem like this:
/interface ethernet set [ find default-name=ether1 ] name=ether1vlanTransitModem
/ip address add address=10.0.0.1/24 interface=ether1vlanTransitModem network=10.0.0.0
/ip firewall nat add action=masquerade chain=srcnat comment="nat the traffic to the dsl modem web interface, only activate when needed" out-interface=ether1vlanTransitModem
This gives the interface a nice name, sets the IP address of that uplink interface and configures the router to perform an source NAT, so you’re able to configure the modem even if you’re behind the Mikrotik router.Make sure that there is not DHCP Client running on the Mikrotik (specially on the ether0 interface)
Now log into your TG588 by going to http://10.0.0.138. Your default user has not the rights to change anything – so we need to change to an other default created user, with higher privileges. Click on the “admin” username:
Choose “change to other user”:
Provide following user data (worked at the time of writing, may got changed)
User: Telek0m
Password: Austria!Eur0
Now your user should have changed to following:
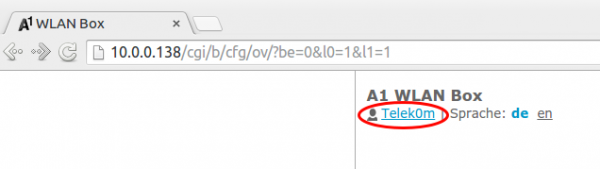
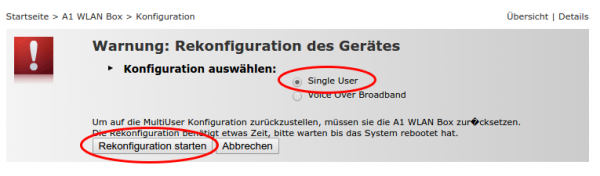
After that you will have more options to select from. Click onto “A1 WLAN Box” followed by “Configuration” and then choose “reconfigure A1 WLAN Box”
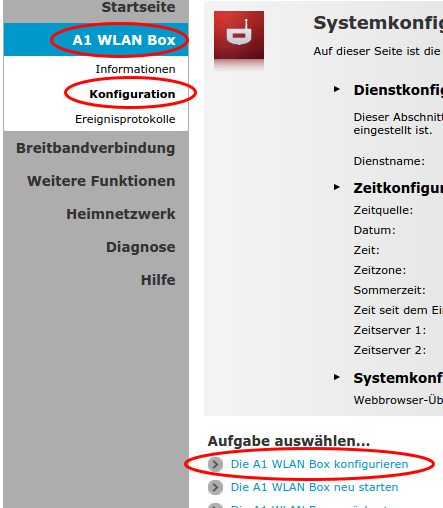
On the following page you need to select “single user” mode and click on reconfigure
Now you’re done with the TG588 – after rebooting it should be fine. Now you need only following two pages on the TG588 – the rest is done by the Mikrotik router
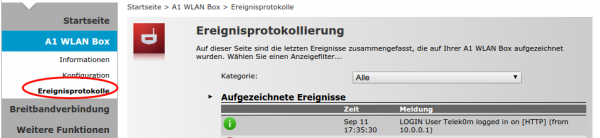
First the event log, here you can check if something does not work:
And following page shows you the speed you’re connected with the provider network
The easy part
Now after all that clicking the Mikrotik part is easy:
/interface pppoe-client add add-default-route=yes disabled=no interface=ether1vlanTransitModem max-mru=1492 max-mtu=1492 mrru=disabled name=pppoeDslInternet password=XXXXXXXX use-peer-dns=no/yes user=XXXXXX
Replace XXXX with the data you got from A1 Telekom.
Now you’re internet connection should be up … test it with
ping 8.8.8.8
after that we only need some Firewall rules move the client traffic correctly to and from the Internet.
/ip firewall mangle add action=change-mss chain=forward comment="max MTU size for pppoe 1492" new-mss=1452 out-interface=pppoeDslInternet protocol=tcp tcp-flags=syn tcp-mss=!0-1452
/ip firewall nat add action=masquerade chain=srcnat comment="nat all traffic which goes over dsl into the internet" out-interface=pppoeDslInternet
Now you’re done. Hope this helped.
My heart misgives me, if I think about them implementing smart meters
July 30, 2015
Update: The site is used by TINETZ but not operated by it – so their IT department is not responsible. The Whois entries shows this also.
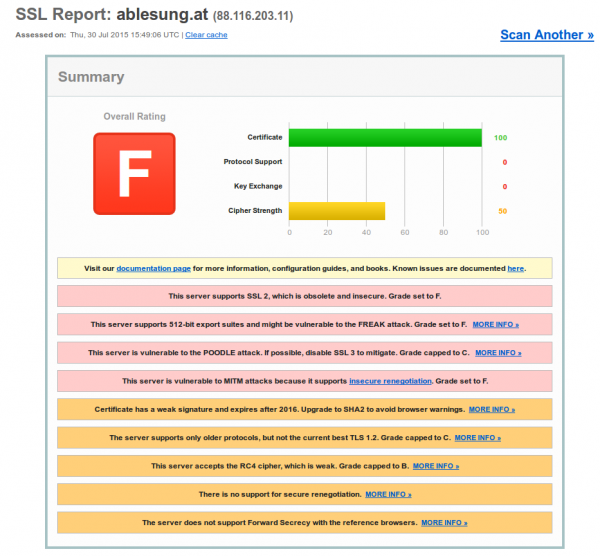
I got today a letter that requests me to enter my electric meter counter reading into the web website of the electric supply company. After getting a warning in my browser I checked the site – and oh my god … they can’t even implement TLS correctly and they want to deploy smart meters with a remote kill switch? Opt-Out if you can 😉
ps: I heard they are ISO 27001 certified – guess not for the website. 😉
Austrian consumer organization Konsument.at slips on web security
June 26, 2015
Today I just surfed on the web site www.konsument.at of the Verein für Konsumenteninformation (VKI), which is a consumer organization in Austria. So you would think that the security of user data (=consumers) is high on their list – but it is not. Just looking at the homepage for 5 minutes shows you that they don’t really care. Lets take a look:
1. Login data not encrypted
On their start page customers of them are able to login:
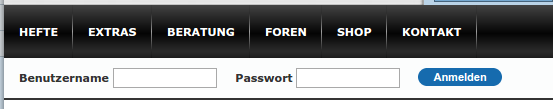
Ok, the page itself, which shows the login mask, is not HTTPS, thats not good as an attacker can change it. But when you click on the logon button it gets worse.
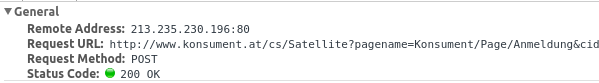
Yes, it is also not encrypted and surely the login data is in clear text as form data:
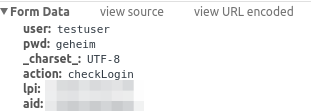
So you would think that they just don’t have any HTTPS, but that’s not correct. If you go the create account page you get HTTPS.

And if you look at the form sent button you’ll see:
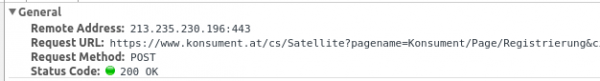
WTF? That’s the same URL – just different parameter and of course this time with HTTPS. So they just have forgotten that HTTPS the first time?
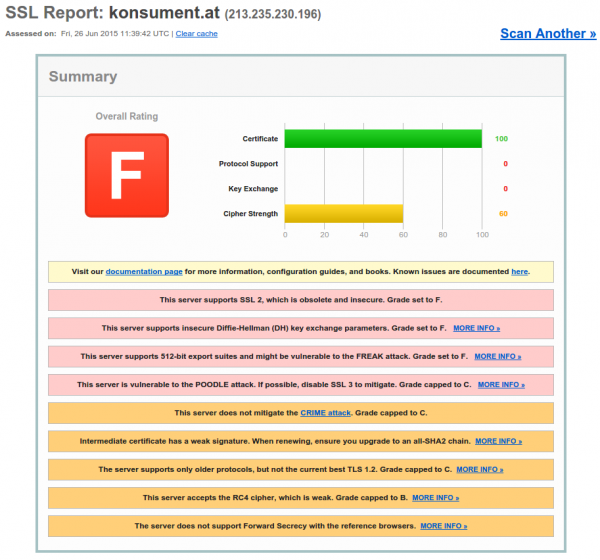
2 TLS at its worst
After the first fiasco I thought – let’s check the HTTPS config, and it is a F grade (=that is bad).
Everything you possible could forget to secure was forgotten here.
major website in Tirol deanonymizes users
February 9, 2015
Important: This is a new version of the post, which does not contain the name of the website, as the owner removed the code and explained to my why he did it.
As you most likely know I’m running NIDS (Network Intrusion detection systems) to monitor the traffic going into and out of multiple networks. Today I saw a traffic which is normal if one is using VoIP via the Internet – but the source address did not use VoIP at that time.
[**] [1:2016149:2] ET INFO Session Traversal Utilities for NAT (STUN Binding Request) [**] [Classification: Attempted User Privilege Gain] [Priority: 1] {UDP} xxx.xxx.xxx.xxx:47865 -> 54.172.47.69:3478
Together with 2 friends I started investigating. The destination IP address belongs to Amazon AWS … even more interesting. So we took a look at the DNS requests the PC made and that resolved to that IP address, which showed:
stun1.webrtc.us-east-1.prod.mozaws.net
So that originates from the Firefox browser and is connected to WebRTC. So we went to the PC and looked through the browsing history, but the pages looked “normal”, so we started to access them again to find out which one triggers the request. And we found it, visiting thread pages on XXX did trigger the requests. Even more interesting was that we were able to reproduce the requests on a Firebox browser running NoScripts! So we looked at the HTML code of the page and found following:
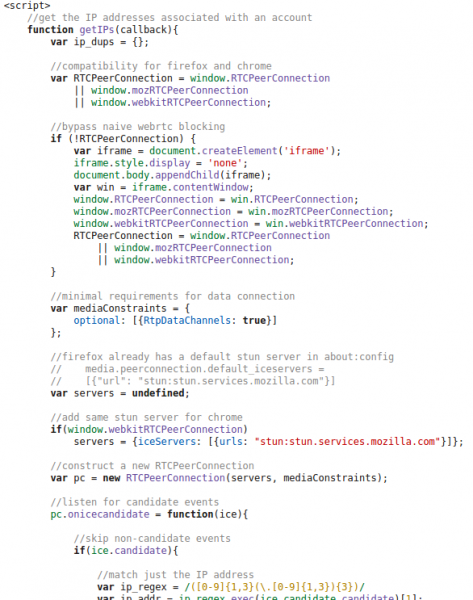
And at the end there are following lines:
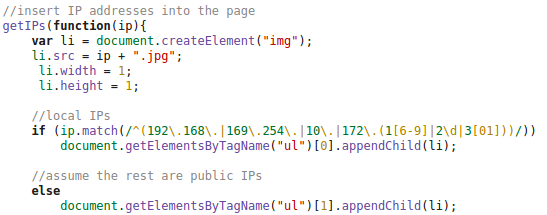
So we did take a look at the HTTP requests made by the client and at the DOM tree and found following:
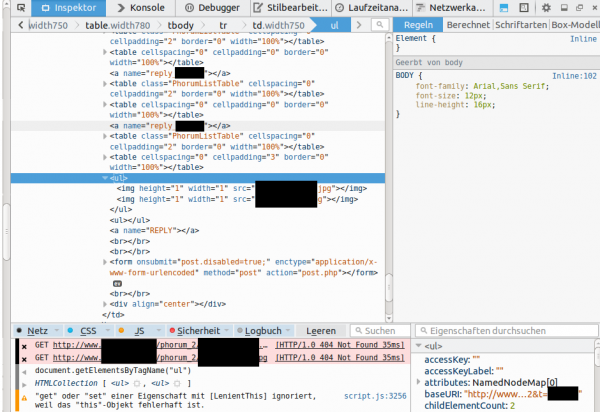
This shows that the local IP addresses (behind a NAT router) and the external IP address used for the WebRTC request is sent in an JPG image request to the server. This seemed to be aimed at deanonymizing the client, if the user accesses it via a VPN connection. Some weeks ago there was a post about something like this – deanonymizing Tor users – a little searching revealed following page. Looking at the source code there, showed that the most parts are identical, just adding it to the DOM tree was new. The exploit works for Firefox and Chrome currently – Internet Explorer does not support WebRTC so far.
After this findings I did sent an email to the owner of the homepage, asked if this is by purpose or if the homepage got hacked. He responded a day later and explained that it was needed against an attacker. Anyway as some people rely on their anonymity I wrote this post, to get the word out that if you need anonymity you need to take actions – not only for this page but for other too. The code is out in the wide – it will be used and misused.
Solutions:
- The best solution is to set the Tor/VPN Tunnel up on the router and not the PC – also for similar exploits in the future.
- Fast solution for this is to install a special plugin: Firefox, Chrome (does currently not work with Chrome V40.0.2214.111, as a reader just reported to me – ScriptSafe does) – this is also a good idea if you’re not using Tor or a VPN.
- Verify that you’re secure on this page or this page
ps: I want to thank my two friends (Benjamin Kostner and one friend who wants to stay anonymous) for helping as that made the process of finding the source of the problem much easier and faster.
Hypo Tirol – Repeat after me: HTTP is bad, HTTPS is good
January 24, 2015
As I know many friends which are Hypo Tirol banking customers and are using the mobile banking app – and my wife is on a business trip and its dark outside – I took a short look at the mobile banking app for Android. And “Oh my God” the same mistakes banks made 10 years ago with online banking are made again.
I downloaded the app and launched it … I got to following
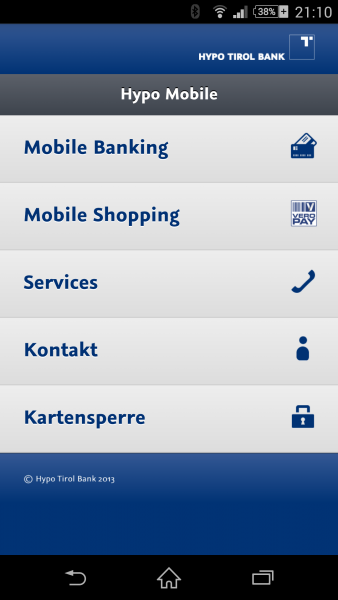
So what does Wireshark tell me after the I started the app?
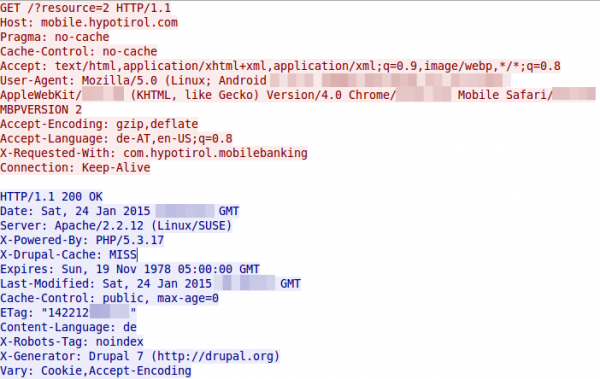
Yes, there is some (most part) HTTP … so lets open the URL on my PC.
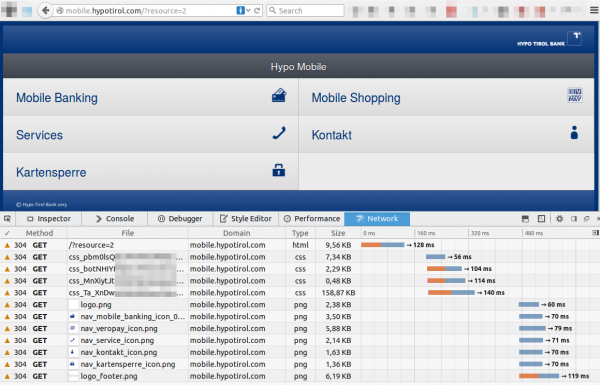
so the whole starting GUI of the banking app is transferred from the server via HTTP.
Attack vector
An attacker can use this to change the content to his liking and as the URL is not shown in the app it could be anything. An idea would be a site that looks like the banking site. The link “Mobile Banking” goes to the HTTPS URL
https://mbp.banking.co.at/appl/mbp/login.html?resource=002
The attacker just can copy and paste the pages and change the links, so it looks identical for the user ;-). So the only question remains – how an attacker can change the content:
- The DNS servers return the IP address of the attacker for mobile.hypotirol.com
- there are many know worms that change the DNS server settings of consumer internet routers
- DNS poisoning attacks … seen in the wild for banking attacks
- A Man in the Middle attack on a public Wifi, but the first two are much easier and can be exploited remotely.
Fix
Use HTTPS everywhere – no HTTP. And check the certificates.
The insecurity of the online version of the Tiroler Tageszeitung
January 17, 2015
This is the first post in over a month, why? As always I was at the Chaos Communication Congress in Hamburg and as I came back there was finally snow –> so I went ski mountaineering. Anyway here is new post, as today its raining so let’s write a post. 😉
This post is about the lack of security awareness at the major tyrolian news paper Tiroler Tageszeitung (in short TT). So lets start why I believe that is true. To be more accurate what I found within 5minutes of looking – it took much longer to write this post.
The subscriber area
When you access http://user.tt.com/ you get following Login prompt.
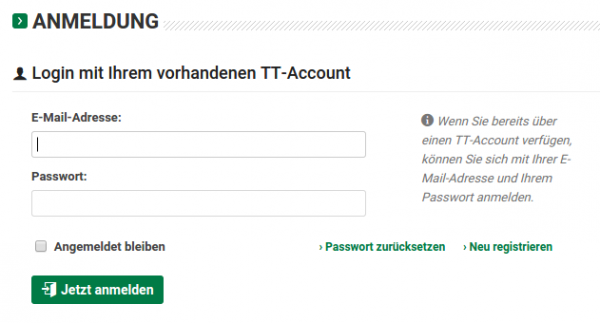
But look above ….
Yes, this site is not HTTPS protected. This is generally not a good idea as an attacker is able to change the URL the passwords are sent to after pressing the login button. But Ok, in 2011 that was not that bad, bad but not that bad. Why I talk about 2011 I’ll tell you later.
So lets enter our mail address and password and click the login button. What request is send?
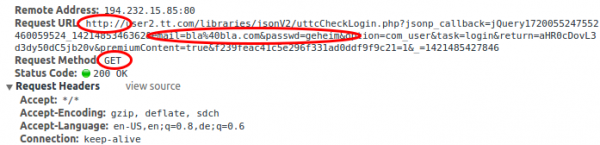
Yeap!
- It is HTTP and not HTTPS? In 2014 using HTTP for login? That was even in 2011 bad.
- They are using HTTP GET with the password as parameter. I can’t believe it. Why? GET parameters are logged on web servers and even worse on proxy servers. Newer, Newer summit passwords with GET, use POST and use HTTPS!
So reading the online TT while waiting for something in a public WiFi network (which is most likely unencrypted) is not a good idea. How many TT users are reusing their password (the email address is a given) ? How may users a potentially affected?
At least I’m able to answer the second question. There is the Österreichische Auflagenkontrolle (ÖAK) … which counts how many copies of a given print media are sold.
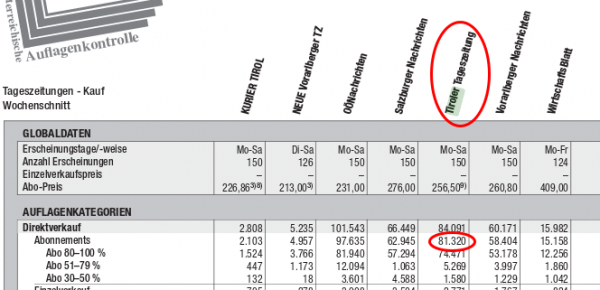
Thats from 2012, the ones from 2013 are sightly smaller but not that formated that nicely for showing a screenshot here. So over 80.000 affected users. The state of Tirol has about 720.038 citizens according to Wikipedia. So over 10% of the population is affected.
The server side
While looking at the get request I found something else interesting. At least the user.tt.com server seems to be running Debian Lenny.
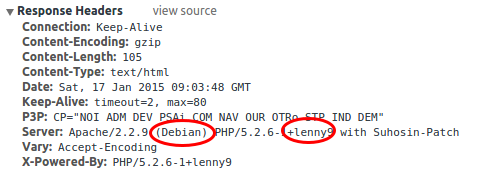
Why is that important? Let’s go to the Debian Wiki and have a look.
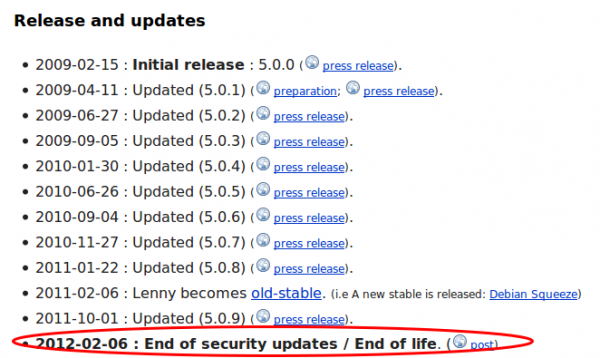
Yes, you read that correctly. No security updates since 2012 and it I believe nobody installs a system with a operation system that is old-stable, the server install and setup must be at least be from 2010. So lets take a look what vulnerabilities be could possible find for Apache 2.2 and PHP 5.2.6 patched the last time in 2012. Let’s have a look at PHP first and followed by Apache. Apache is better than PHP, but for PHP there are some pretty high rated vulnerabilities, one even with the highest rating. Basically you can get everything from the box if you want. When I took a look which JavaScript made the HTTP GET request with the password I found following.
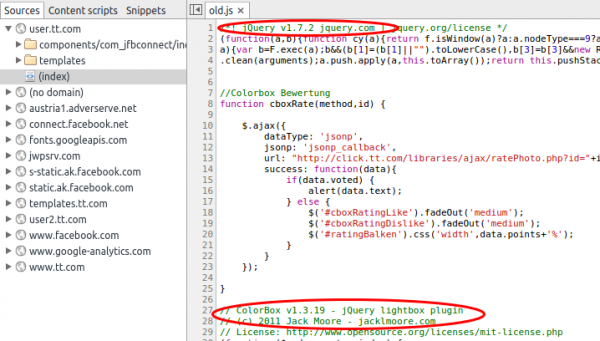
jQuery 1.7.2 that sounds old …. a look at the release notes tells 21.3.2012, not new but only a medium vulnerability … attacking PHP is easier.
Basically we could own the user.tt.com server easily, but whats about the other servers. Are they better? What is obvious from the start that the servers for the main site are different ones and they are using Varnish as is an HTTP accelerator and the learned to hight the Apache version in the HTTP header.
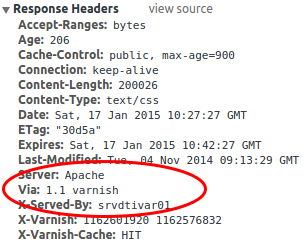
A short look in the Whois shows that the user.tt.com seems to be hosted by the TT itself and the frontend server for www.tt.com by the APA guys. It seems that they are filtering the bad stuff from the backend TT servers. As I didn’t want to dig deeper than whas possible in 5 minutes I stopped here … Just one thing I found which is not security related: tt.com is heavy using Google services for example Google Analytics.
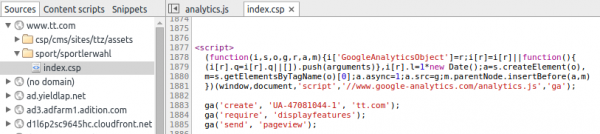
The option _anonymizeIp() is missing here to not violate the Austrian data protections law and you need to post a information for your visitors (could not find one on tt.com) and make a opt-out possible.
So much for my 5 minutes analytics of the Tiroler Tageszeitungs homepage. 😉
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
55 queries. 0.071 seconds.