Howto filter “No VR found on VLAN xxx with VR Id xxx” on Extreme XOS switches
May 25, 2014
If your Extreme Networks switches are using VRRP and other devices are using it also in the same VLAN, the Exterme XOS switches will complain loudly about that … one log line per broadcast. In my case it were two per second and as the switch stores only 1000 log lines .. the log soon contained only these entries:
05/22/2014 17:29:41.11 Slot-1: No VR found on VLAN xxx with VR Id xxx
05/22/2014 17:29:40.48 Slot-2: No VR found on VLAN xxx with VR Id xxx
05/22/2014 17:29:40.11 Slot-1: No VR found on VLAN xxx with VR Id xxx
05/22/2014 17:29:39.48 Slot-2: No VR found on VLAN xxx with VR Id xxx
05/22/2014 17:29:39.11 Slot-1: No VR found on VLAN xxx with VR Id xxx
The one pitfall with using the exclude match string variable is that the VRIDs must not be treated as string variable. This does not work because Extreme XOS does not treat the VRID as a string variable, but rather as a integer. To determine the valid variables available for the specific event you’ll need to type following:
Slot-1 xxxxxxx.1 # show log events "VRRP.UnkVR" details
Component SubComponent Condition Severity Parameters
----------- ------------ ----------------------- ------------- ----------
VRRP UnkVR Warning 2 Total
0 - string
1 - number (32-bit unsigned int)
No VR found on VLAN %0% with VR Id %1%
This tells us that to filter on the VRRP.UnkVR messages, there is a string variable (%0%) equal to the VLAN name, and a integer (%1%) equal to the VRID itself. Because Extreme XOS interprets the VRID itself as a number and not a string, doing an exclude match string will not work. You must use the number variable as follows:
configure log filter "DefaultFilter" add exclude events "VRRP.UnkVR" match number xxx
From the Concept Guide:
The filter can be associated with one or more targets using the command to control the messages sent to those targets. The system has one built-in filter named DefaultFilter, which itself may be customized. Therefore, the if a filter other than DefaultFilter is desired. As its name implies, DefaultFilter initially contains the default level of logging in which every Extreme XOS component and subcomponent has a pre-assigned severity level.
PS: You can use this solution to filter out any other event, just check with show log events "xxxx" details
Why doesn’t the Ubiquiti Unifi DNS based controller location function work with Mikrotik RouterOS DNS? [Update]
May 18, 2014
Last week I ran into a problem with my Unifi UAPs after I switched the central router to Mikrotik RouterOS and also used the DNS server of the RouterOS. If the Unifi UAPs are in the same subnet as the controller, the UAPs find it via a broadcast but if there is no layer 2 connection they need a special DHCP Option or the DNS name unifi.xxxxx (xxx in this case is the domain name specified via DHCP) needs to resolve to the IP address of the controller. My setup was using the DNS variant but after I switched to the Mikrotik DNS server the UAPs stopped to connecting to the controller. I logged into the one of them via SSH and saw following in /var/log/messages.
ace_reporter.reporter_fail(): Unable to resolve (http://unifi:8080/inform)
I did at once a ping unifi, which worked so I started to sniff the traffic and saw following:
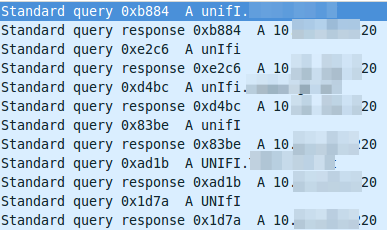
The DNS resolution is working at first glance but it seems to be funny that the requests are always different, as the case changes all the time. So I did a closer look into a requesting packet and the corresponding answer packet. The request looks this way:
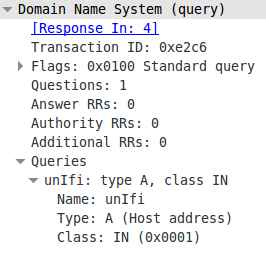
And the answer looks this way:
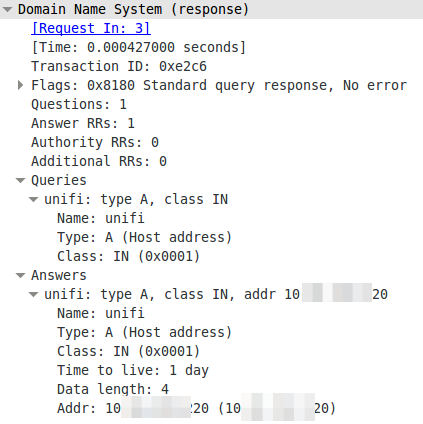
The DNS server is lower casing the answers. This seams to break it. So I searched more into the topic why the Unifi UAPs are using the case randomizing in the first place and where the blame lies for this not working. Unifi UAPs started to use randomize-case in the DNS lookup with Version 2.4.6 (the current stable version) as a security feature, which is named dns0x20 and described in this RFC draft (called Use of Bit 0x20 in DNS Labels to Improve Transaction Identity). From the abstract:
The small (16-bit) size of the DNS transaction ID has made it a frequent target for forgery, with the unhappy result of many cache pollution vulnerabilities demonstrated throughout Internet history. Even with perfectly and unpredictably random transaction ID’s, random and birthday attacks are still theoretically feasible. This document describes a method by which an initiator can improve transaction identity using the 0x20 bit in DNS labels.
The RFC draft states that further:
In practice, all question sections in responses are exact copies of question sections from requests, even if the zone data and answer section owner names differ in their uppercase/lowercase attributes from the question section. So while it is theoretically possible for a request’s question section to contain the name “www.ietf.org” and a response’s question section to contain the name “WWW.IETF.ORG”, this has not been observed, and might not even work reliably.
I guess we found one DNS server, which handles that differently. So Unifi UAPs are using a draft version of a RFC to make it more secure and Mikrotik RouterOS is one of the few it does not work with. It works with the Linux standard DNS server bind. So who to blame? its not that easy. Anyway I made a feature request to Mikrotik because returning the correct query does not break anything and more security with DNS is always good idea.
ps: I switched to the DHCP option for getting the UAPs to work with the RouterOS DNS.
Update:
Just got following back from the Mikrotik support:
Hello,
that will be possible in RouterOS v7
Regards,
Janis Krumins
How to configure SNMPv3 securely on Mikrotik RouterOS [Update]
May 11, 2014
In the last post I wrote on how to configure SNMPv3 for CentOS/RHEL/SL. I thought it might be a good idea to post the SNMPv3 configuration for various systems/devices – so this post is about Mikrotik RouterOS.
This time it is even easier than on Linux, just one line:
/snmp community set [ find default=yes ] name=snmpv3user security=private authentication-password=snmpv3authPass authentication-protocol=SHA1 encryption-password=snmpv3encPass encryption-protocol=DES read-access=yes write-access=no addresses=10.0.0.0/24
If you want to keep the default SNMP configuration and add just another, use this:
/snmp community add name=snmpv3user security=private authentication-password=snmpv3authPass authentication-protocol=SHA1 encryption-password=snmpv3encPass encryption-protocol=DES read-access=yes write-access=no addresses=10.0.0.0/24
But the RouterOS has also one weakness, it only supports DES and not AES. So the test command looks like this:
snmpwalk -u snmpv3user -A snmpv3authPass -a SHA -X snmpv3encPass -x DES -l authPriv 10.7.7.1 -v3
If you now look at the answer of a request in Wireshark you’ll only see encrypted text:
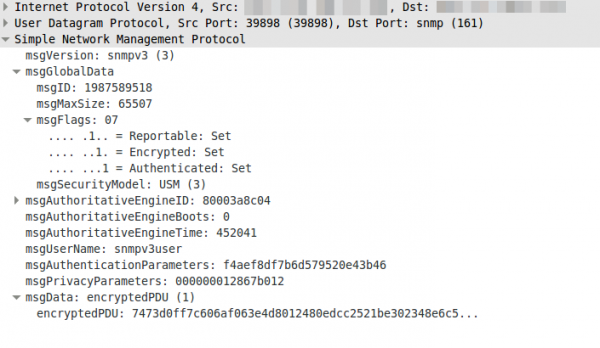
Update: Starting with RouterOS 6.16rc17 (2014-Jul-09 09:52) AES encryption (rfc3826) for SNMP is supported according to the changelog.
How to configure SNMPv3 securely in CentOS/RHEL/SL
May 4, 2014
Looking through the Internet I found more often than not insecure SNMP setups explained in Howtos, maybe the authors where happy to got running in the first place – don’t know. The Simple Network Management Protocol (SNMP) is used to monitor (and configure in the case of network equipment) systems via the network in a standardized way. There are 3 versions of it in the wild:
Version 1
The first version, it is really old and only uses community strings to “protect” access. If you look with Wireshark what the packet for the request contains you’ll see following:
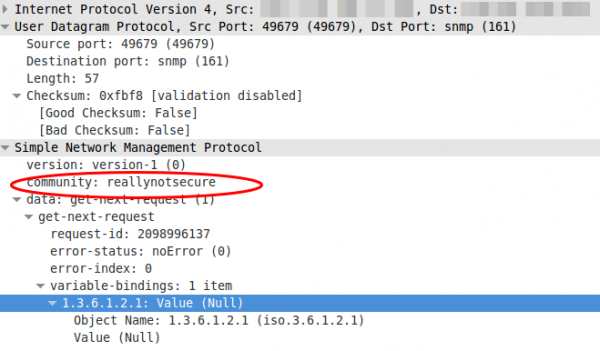
Yes, thats the community in clear text …. so don’t use it, if you must not. If you must (old devices which supports only this) use it on a secure network and make sure that the device only accepts quests from a given source IP address.
Version 2c
Not better in any security related way. The e.g. traffic counters are just bigger, as on fast interfaces it was possible with v1 that the counter rotated more than ones within the interval you queried so you didn’t know how many bytes really got transfered over the link.
Version 3
Now we’re talking. This versions supports authentication passwords, that get not transfered in the clear and it also supports encryption passwords so a attacker does not see what is transfered. I’ll show you now how you configure your CentOS/RHEL/SL to let it be queried via SNMPv3 in a secure way.
- We need to install the package we need:
yum install net-snmp - We create our user. SHA1 is used for the authentication and AES for the encryption of the traffic. And for security it is important to use two separated passwords.
service snmpd stop
net-snmp-create-v3-user -ro -A snmpv3authPass -a SHA -X snmpv3encPass -x AES snmpv3user
service snmpd startThis will print something like this
adding the following line to /var/lib/net-snmp/snmpd.conf:
createUser snmpv3user SHA "snmpv3authPass" AES snmpv3encPass
adding the following line to /etc/snmp/snmpd.conf:
rouser snmpv3user - Secure the SNMP daemon with a host firewall and only allow requests from source IP addresses you know and which need to query the system.
- Verify that everything works with following command:
snmpwalk -u snmpv3user -A snmpv3authPass -a SHA -X snmpv3encPass -x AES -l authPriv 127.0.0.1 -v3
So as you see it is quite easy, so there is now reason to use anything less secure!
If you want to delete the user, just edit the two files mentioned above. In /etc/snmp/snmpd.conf delete the line rouser snmpv3user and in /var/lib/net-snmp/snmpd.conf look for a line like this and remove it:
usmUser 1 3 0x80001f88801e15113fbf17bf5100000000 0x736e6d7076337573657200 0x736e6d7076337573657200 NULL .1.3.6.1.6.3.10.1.1.3 0xaaa3bc2aa941d932a581bbb11956699a7d807238 .1.3.6.1.6.3.10.1.2.4 0xcd6eed84f9d1aa903e92162f0e3fcb26 ""
restart the daemon with service snmpd restart and the user is gone.
Ubuntu 14.04 apt-get update –> Reading package lists… Error!
May 3, 2014
Today I just wanted to make an apt-get update but I got following:
Reading package lists... Error!
W: Encountered status field in a non-version description
W: Encountered status field in a non-version description
W: Encountered status field in a non-version description
E: Encountered a section with no Package: header
E: Problem with MergeList /var/lib/dpkg/status
E: The package lists or status file could not be parsed or opened.
And Synaptic and update manager would not start .. I just checked to make sure as I don’t use them normally. Anyway the solution is really simple. If you take a look into the above mentioned directory you see 2 status files:
$ ll /var/lib/dpkg/status*
-rw-r--r-- 1 root root 2752482 Mai 1 09:27 /var/lib/dpkg/status
-rw-r--r-- 1 root root 2753380 Mai 1 09:27 /var/lib/dpkg/status-old
I just did following:
$ sudo mv /var/lib/dpkg/status /var/lib/dpkg/status-new
$ sudo mv /var/lib/dpkg/status-old /var/lib/dpkg/status
And it worked again. Hope this helps others.
I get only a A- on Qualys SSL Labs tests – Why? and what can I do?
April 19, 2014
In the last months more and more sysadmins started looking into their SSL configuration of their HTTPS websites. And one of the major sites that is used to rate/check the quality of the SSL configuration on a given HTTPS server is the Qualys SSL Labs SSL Server Test which can be reached via this link. If a sysadmin gets a not so good rating he search through the Internet and uses something like this settings (Apache 2.2 on Centos 6) to fix it:
SSLEngine on
SSLProtocol All -SSLv2 -SSLv3
Header add Strict-Transport-Security "max-age=15768000"
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4
SSLHonorCipherOrder On
This leads at the time of writing (Quality SSL Labs changes the rating from time to time to following) to:
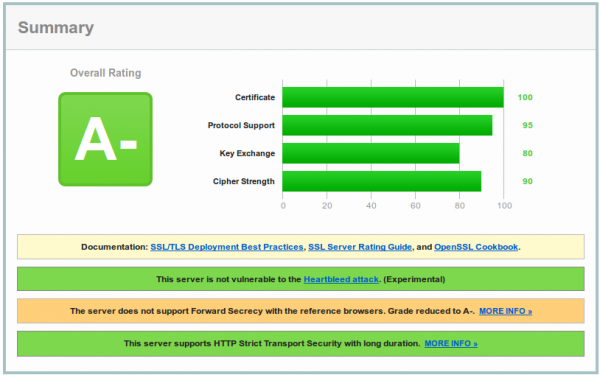
And now you are wondering why you get only a A- and what the problem with your configuration is. To make your journey shorter, the problem is most likely not the SSL configuration, it is the software you’re running. As you see on the screenshot the test reports that Forward Secrecy is not supported by all browsers and if you take a look at the details,
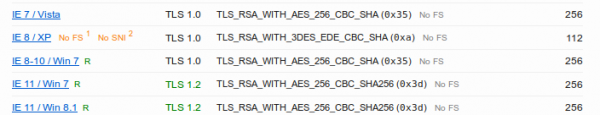
you’ll see that the problem is the Internet Explorer and that Forward Secrecy works for all other browsers.
(Perfect) Forward Secrecy
But what is (Perfect) Forward Secrecy in the first plage and why should you care. PFS ensures the integrity of a session key in the event that the private key of the server gets compromised. This is done by generating a separate session key for every new HTTPS session/connection.
Why should you care?
An attacker could record the SSL traffic for some time and later he got the private key and now without PFS he would be able to extract all the SSL traffic he was not able to look into before. Basically without PFS if a private key gets compromised you not only need to look the now and the future but also a the past and consider everything that was encrypted/signed by this key as compromised. With PFS you’re sure that an attacker is not able to extract data from before he got the private key. With the Heartbleed Bug in OpenSSL such an attack was possible or by hacking the server.
The cipher suites (the ones you choose with SSLCipherSuite in the Apache configuration) that provide Perfect Forward Secrecy are those that use an ephemeral form of the Diffie-Hellman key exchange. The disadvantage of them is that they have a performance overhead, but the security is worth it and it is not that much overhead. With some elliptic curve variants the performance would be better.
A- and the workarounds
And how to the problem with the A- rating – I’ll quote Shadow Zhang who described it nicely in his post:
With Apache 2.2.x you have only DHE suites to work with, but they are not enough. Internet Explorer (in all versions) does not support the required DHE suites to achieve Forward Secrecy. (Unless youre using DSA keys, but no one does; that’s a long story.) Apache does not support configurable DH parameters in any version, but there are patches you could use if you can install from source. Even if openssl can provide ECDHE the apache 2.2 in debian stable does not support this mechanism. You need apache 2.4 to fully support forward secrecy.
Patching and compiling Apache is not the best idea, as you need to do it again for every security update. I see following options:
- Use a distribution version which supports Apache 2.4
- If you’re using RHEL 6.5 take a look at the Red Hat Software Collections 1.1 currently in beta, which provides Apache 2.4 – don’t know about CentOS at this point.
- Upgrade your Ubuntu to 14.04 which provides Apache 2.4
- Use Nginx as reverse proxy in front of the Apache because it fully supports ECDHE.
- Change to a web server that is shipped with your distribution and that does support ECDHE.
I hope this post helped and saved you some time looking through the internet for a solution.
Howto setup a redundant and secure BGP (full table) Internet connection with Mikrotik Routers
March 22, 2014
Looking through the Internet, there are much howto’s specially in the OpenSource field but a guide line for a redundant and secure internet connection based on BGP (full table) is not something you find on many sites. So I thought I write such a documentation and I’m hoping it helps some networks admins in setting up their company internet connection. BGP is not that hard ;-).
General conditions
Following points are the general conditions for this howto:
- Two Internet Uplinks to two different providers, each connected via one fibre link
- One provides the BGP peer in the same VLAN and one peer is only reachable via a routing hop (to show the different configuration)
- One provider hands the customer only one peering IP address and the other two (to show the different configuration)
- We use 2 BGP routers on our side for redundancy
- Both provide IPv4 and IPv6 Full Tables
- No traffic engineering to steer traffic to one provider over the other is done
- A failure of
- one router must not change anything for the user/customer
- one switch is allowed to lose one Uplink but not both, so traffic for the user/customers needs to be unaffected
- one fibre link leads to one Uplink down, but the traffic for the user/customers needs to be unaffected
- Secure setup
- Setting up the layer 2 switches and the redundant firewall behind the routers is not part of this howto
- Using Mikrotik RouterOS devices as the routers in the config part, but the same setup would also work with Cisco or Vayatta routers, which I’ve also used for BGP based Internet connections.
Setup
Following drawing shows the setup for the BGP Internet connection.
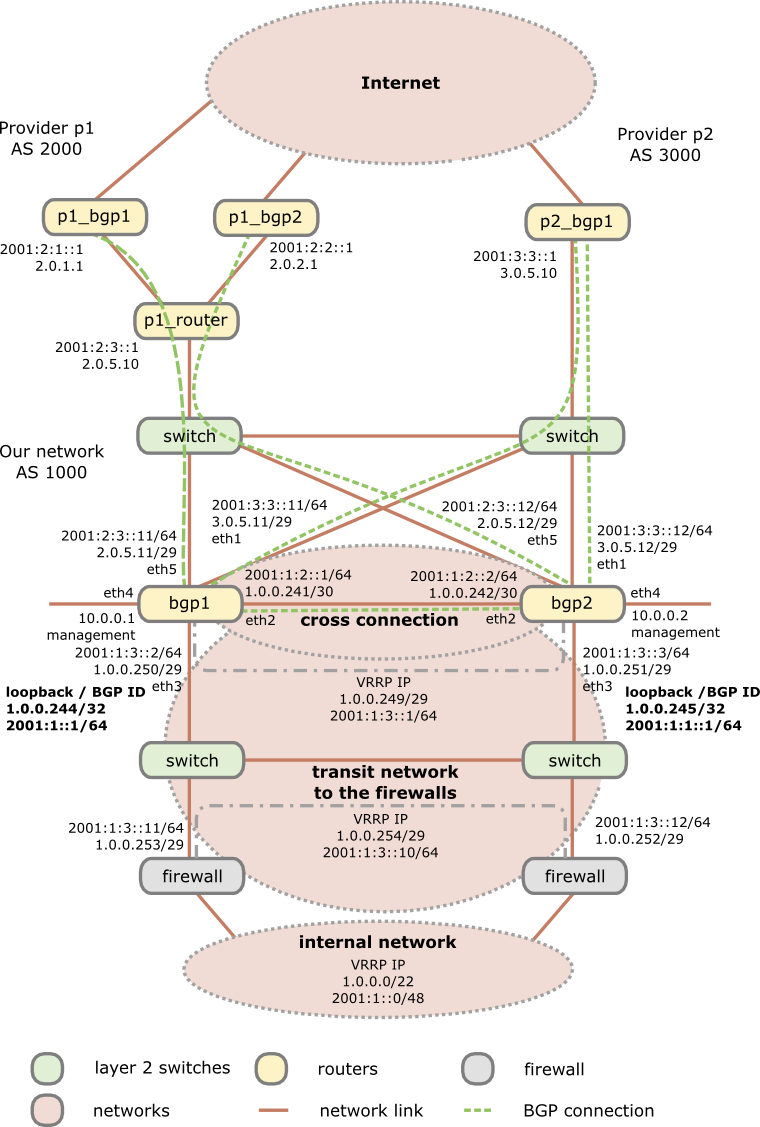
As you see I’m using 2 switches as media converters and to distribute the provider transit networks to both routers. Why I do this as there are Mikrotik routers with SPF and SPF+ modules? First using a Mikrotik on a x86 provides you with no switching (just bridging). Secondly even if you use a Mikrotik Hardware router with switching support, a switch that is only used for layer 2 stuff and has no IP interface in the public networks (only in the management network) will be more stable specially concerning firmware updates than routers which are used for active interaction with other systems. No update for multiple years is not uncommon for switches in this scenario, which is not valid for the routers, specially if you use some special features on the routers. This means you can update a router without the Ethernet link to the provider going down and as the Mikrotik boots under 30 seconds its a minimal impact. The default switching time for BGP is 180 seconds (3*60 seconds) which is much longer than a boot after a firmware update.
Configuration of the routers
If not specified the configuration is the same for both routers and the syntax works with RouterOS 6.10, but it does not change that much normally, at least not since version 4 when I started using Mikrotiks.
First we start with the names of the routers
BGP1:
/system identity set name=bgp1
BGP2:
/system identity set name=bgp2
And now to the actual work – we need to configure our interfaces. We create a loopback interface for at least following reasons:
- This interface is always up, so the IP address is always up – good for monitoring the node vs interfaces
- We use the IP address on this interface as our OSFP and BGP ID
- We use it to blackhole routed traffic .. more later in this post
/interface bridge add name=loopback
/interface ethernet
set [ find default-name=ether1 ] name=ether1vlanTransitProvider2
set [ find default-name=ether2 ] name=ether2vlanCrossConnection
set [ find default-name=ether3 ] name=ether3vlanTransitFirewall
set [ find default-name=ether4 ] name=ether4vlanMgmt
set [ find default-name=ether5 ] name=ether5vlanTransitProvider1
As Mikrotik allows to rename the interface we do so as it makes configuration lines which use these interfaces much easier to understand … believe me I’ve routers with > 100 interfaces :-). For the transit network to the firewall we’ll setup a VRRP and to be somewhat more secure than normal VRRP we also set a long and random password. We configure also a no default VRID, as most system use 1 as default and who knows what the firewalls use. 😉
BGP1:
/interface vrrp add interface=ether3vlanTransitFirewall name=vrrpTransitFirewall password=XXXXXXX priority=250 vrid=10
BGP2:
/interface vrrp add interface=ether3vlanTransitFirewall name=vrrpTransitFirewall password=XXXXXXX priority=200 vrid=10
So if the BGP1 is up, it always will be the master. Now we need to configure the IP addresses …. lets start with IPv4
BGP1:
/ip address
add address=1.0.0.244/32 interface=loopback
add address=3.0.5.11/29 interface=ether1vlanTransitProvider2
add address=1.0.0.241/30 interface=ether2vlanCrossConnection
add address=1.0.0.250/29 interface=ether3vlanTransitFirewall
add address=1.0.0.249/29 interface=vrrpTransitFirewall
add address=10.0.0.1/24 interface=ether4vlanMgmt
add address=2.0.5.11/29 interface=ether5vlanTransitProvider1
BGP2:
/ip address
add address=1.0.0.245/32 interface=loopback
add address=3.0.5.12/29 interface=ether1vlanTransitProvider2
add address=1.0.0.242/30 interface=ether2vlanCrossConnection
add address=1.0.0.251/29 interface=ether3vlanTransitFirewall
add address=1.0.0.249/29 interface=vrrpTransitFirewall
add address=10.0.0.2/24 interface=ether4vlanMgmt
add address=2.0.5.12/29 interface=ether5vlanTransitProvider1
And now we do the same for IPv6 … just the internal management is kept IPv4 only, as you don’t need it there normally (at least I’m not)
BGP1:
/ipv6 address
add address=2001:1::1/64 interface=loopback
add address=2001:3:3::11/64 interface=ether1vlanTransitProvider2
add address=2001:1:2::1/64 interface=ether2vlanCrossConnection
add address=2001:1:3::2/64 interface=ether3vlanTransitFirewall
add address=2001:1:3::1/64 interface=vrrpTransitFirewall
add address=2001:2:3::11/64 interface=ether5vlanTransitProvider1
BGP2:
/ipv6 address
add address=2001:1:1::1/64 interface=loopback
add address=2001:3:3::12/64 interface=ether1vlanTransitProvider2
add address=2001:1:2::2/64 interface=ether2vlanCrossConnection
add address=2001:1:3::3/64 interface=ether3vlanTransitFirewall
add address=2001:1:3::2/64 interface=vrrpTransitFirewall
add address=2001:2:3::12/64 interface=ether5vlanTransitProvider1
Now we add our static routes we need. We need to set one for our management network, so we can be reached via the admin computers and set the route for provider 1 as the BGP routers are not in the same subnet. Also the router to the firewalls for our internal network is clear, but we need one more feature which needs some explaining. If the link to the firewalls goes down on a router, the IP address / network also goes down and its routes over this interface. As the router redistributes the connected and static routes via BGP it will not anymore send it out. This is basically ok, but now something comes into play that is called “BGP Route Flap Damping“, which can lead to the problem that everything is running again but some AS are not setting traffic to you for some time. So it is paramount to keep the announcing running as stable as possible, which leads us to black hole routes. As in IPv6 Mikrotik does not support it (as of yet) we use a workaround to accomplish the same. PS: you can use the same to black hole an attacker .. really fast and without much load on the system … just saying 🙂
/ip route
add distance=1 dst-address=10.0.0.0/8 gateway=10.0.0.254
add distance=1 dst-address=2.0.1.1/32 gateway=2.0.5.10
add distance=1 dst-address=2.0.2.1/32 gateway=2.0.5.10
add distance=1 dst-address=1.0.0.0/22 gateway=1.0.0.254
add comment="if interface to firewall goes down, this route is used" distance=254 dst-address=1.0.0.0/22 type=blackhole
/ipv6 route
add distance=1 dst-address=2001:2:1::1/128 gateway=2001:2:3::1
add distance=1 dst-address=2001:2:2::1/128 gateway=2001:628:1400:1003::1
add distance=1 dst-address=2001:1::0/48 gateway=2001:1:3::10
BGP1:
add comment="if interface to firewall goes down, this route is used" distance=254 dst-address=2001:1::0/48 gateway=2001:1::ffff
BGP2:
add comment="if interface to firewall goes down, this route is used" distance=254 dst-address=2001:1::0/48 gateway=2001:1:1::1:ffff
After the IP addresses and static routes are configured we need to secure our setup before doing anything else. As the BGP routers are in front of the firewalls they can get attacked directly from the Internet, sure, but traffic (e.g. attacks, P2P, …) to systems behind it can also make problems for the routers, so we’ll do something that we normally don’t do. We’ll disable connection tracking – we are a plain and stupid router … let the firewall track connections, we don’t care. This takes much work from the router if you’ve many many connections over it. Sure it makes the firewall settings on the router harder but as said, let the router focus on its single task – route traffic as much and as fast as possible. I sometimes see BGP routers overloaded with other tasks and than people complain that they have problems with high loads. If your network/uplinks is so small, that it does not matter, sticking with connection tracking is also ok – you’ll just can change the firewall rules to use connection awareness.
/ip firewall connection tracking set enabled=no
/ip settings set tcp-syncookies=yes
Now we create a address list of our BGP peers which we will allow to connect to our BGP daemon. Don’t forget your routers, as they talk also between themselves:
/ip firewall address-list
add address=2.0.1.1 list=listBgpIPv4Peers
add address=2.0.2.1 list=listBgpIPv4Peers
add address=3.0.5.10 list=listBgpIPv4Peers
add address=1.0.0.241 list=listBgpIPv4Peers
add address=1.0.0.242 list=listBgpIPv4Peers
/ipv6 firewall address-list
add address=2001:2:1::1 list=listBgpIPv6Peers
add address=2001:2:2::1 list=listBgpIPv6Peers
add address=2001:3:3::1 list=listBgpIPv6Peers
add address=2001:1:2::1 list=listBgpIPv6Peers
add address=2001:1:2::2 list=listBgpIPv6Peers
And now to actual firewall rules:
/ip firewall filter
add chain=input comment="BGP incomming is ok on all interfaces from our peers" src-address-list=listBgpIPv4Peers dst-port=179 protocol=tcp
add chain=input comment="without conntrack we need to allow that" dst-port=1024-65535 protocol=tcp src-address-list=listBgpIPv4Peers
add chain=input comment="OSFP is on the crosslink ok" in-interface=ether2vlanCrossConnection protocol=ospf
add chain=input comment="VRRP is ok on the interface to the firewalls" dst-address=224.0.0.18 in-interface=ether3vlanTransitFirewall protocol=vrrp
add chain=input comment="everyone can ping us" protocol=icmp
add action=drop chain=input comment="we drop any request from not from the Mgmt Interface" in-interface=!ether4vlanMgmt
/ipv6 firewall filter
add chain=input comment="BGP incomming is ok on all interfaces from our peers" src-address-list=listBgpIPv4Peers dst-port=179 protocol=tcp
add chain=input comment="without conntrack we need to allow that" dst-port=1024-65535 protocol=tcp src-address-list=listBgpIPv6Peers
add chain=input comment="OSFP is on the crosslink ok" in-interface=ether2vlanCrossConnection protocol=ospf
add chain=input comment="VRRP is ok on the interface to the switches" dst-address=ff02::12/128 in-interface=ether3vlanTransitFirewall protocol=vrrp
add chain=input comment="everyone can ping us" protocol=icmpv6
add action=drop chain=input comment="we drop any request from not from the Mgmt Interface" in-interface=!ether4vlanMgmt
Looks like a secure setup .. hopefully it also is :-). Now we’re ready to configure the BGP part, starting with the configuration of the instance.
BGP1:
/routing bgp instance set default as=1000 redistribute-connected=yes redistribute-ospf=yes redistribute-static=yes router-id=1.0.0.244
BGP2:
/routing bgp instance set default as=1000 redistribute-connected=yes redistribute-ospf=yes redistribute-static=yes router-id=1.0.0.245
Now we need to set our networks to announce:
/routing bgp network
add network=1.0.0.0/22
add network=2001:1::0/48
And now we configure our peers. For the 2 BGP routers which are reachable only via an other router we need to set multihop to yes. We need also to make a link between our 2 routers if one sees a peer the other does not but he still is the the VRRP master.
/routing bgp peer
BGP1:
add in-filter=filterIpv4AS2000in multihop=yes name=p1_bgp1 out-filter=filterIpv4GLOBALout remote-address=2.0.1.1 remote-as=2000 tcp-md5-key=xxxxxxxx
add in-filter=filterIpv4AS3000in name=p2_bgp1 out-filter=filterIpv4GLOBALout remote-address=3.0.5.10 remote-as=3000 tcp-md5-key=xxxxxxx
add address-families=ipv6 in-filter=filterIpv6AS2000in multihop=yes name=p1_bgp1 out-filter=filterIpv6GLOBALout remote-address=2001:2:1::1 remote-as=2000 tcp-md5-key=xxxxxxx
add address-families=ipv6 in-filter=filterIpv6AS3000in name=p2_bgp1 out-filter=filterIpv6GLOBALout remote-address=2001:3:3::1 remote-as=3000 tcp-md5-key=xxxxxxx
add name=bgp2 remote-address=1.0.0.242 remote-as=1000
add name=bgp2ipv6 remote-address=2001:1:2::2 remote-as=1000
BGP2:
add in-filter=filterIpv4AS2000in multihop=yes name=p1_bgp2 out-filter=filterIpv4GLOBALout remote-address=2.0.2.1 remote-as=2000 tcp-md5-key=xxxxxxxx
add in-filter=filterIpv4AS3000in name=p2_bgp1 out-filter=filterIpv4GLOBALout remote-address=3.0.5.10 remote-as=3000 tcp-md5-key=xxxxxxx
add address-families=ipv6 in-filter=filterIpv6AS2000in multihop=yes name=p1_bgp2 out-filter=filterIpv6GLOBALout remote-address=2001:2:2::1 remote-as=2000 tcp-md5-key=xxxxx
add address-families=ipv6 in-filter=filterIpv6AS3000in name=p2_bgp1 out-filter=filterIpv6GLOBALout remote-address=2001:3:3::1 remote-as=3000 tcp-md5-key=xxxxxxx
add name=bgp1 remote-address=1.0.0.241 remote-as=1000
add name=bgp1ipv6 remote-address=2001:1:2::1 remote-as=1000
That was not that hard, but what are all this filter names? As I told you in the beginning we’re paranoid so we don’t trust anyone so we’re filtering all routes going in and out. So lets start with the out filters as they are much easier. They just let us announce our own networks, so we won’t account networks of the one provider to the other and therefore make a link for them over us.
/routing filter
add action=accept chain=filterIpv4GLOBALout prefix=1.0.0.0/22
add action=discard chain=filterIpv4GLOBALout
add action=accept chain=filterIpv6GLOBALout prefix=2001:1::0/48
add action=discard chain=filterIpv6GLOBALout
The in filters are at little bit more complicated, but not that hard. We make sure that every AS path we get from the provider starts with his AS. It had happened that some provider are a little bit messy there.
add action=jump chain=filterIpv4AS2000in jump-target=filterIpv4Nomartians
add action=accept bgp-as-path="^2000(,[0-9]+)*\$" chain=filterIpv4AS2000in
add action=accept chain=filterIpv4AS2000in
add action=jump chain=filterIpv4AS3000in jump-target=filterIpv4Nomartians
add action=accept bgp-as-path="^3000(,[0-9]+)*\$" chain=filterIpv4AS3000in
add action=accept chain=filterIpv4AS3000in
add action=jump chain=filterIpv6AS2000in jump-target=filterIpv6Nomartians
add action=accept bgp-as-path="^2000(,[0-9]+)*\$" chain=filterIpv6AS2000in
add action=accept chain=filterIpv6AS2000in
add action=jump chain=filterIpv6AS3000in jump-target=filterIpv6Nomartians
add action=accept bgp-as-path="^3000(,[0-9]+)*\$" chain=filterIpv6AS3000in
add action=accept chain=filterIpv6AS3000in
After this is clear, I only need to explain the reason for the filterIpv4Nomartians and filterIpv6Nomartians filters. Its quite easy, these lists contain IP subnets that we should not get via BGP, because they are not used on the Internet (at least not by good people) so we’ll filter them.
add action=discard chain=filterIpv4Nomartians prefix=0.0.0.0/8
add action=discard chain=filterIpv4Nomartians prefix=127.0.0.0/8
add action=discard chain=filterIpv4Nomartians prefix=192.0.2.0/24
add action=discard chain=filterIpv4Nomartians prefix=10.0.0.0/8
add action=discard chain=filterIpv4Nomartians prefix=172.16.0.0/12
add action=discard chain=filterIpv4Nomartians prefix=192.168.0.0/16
add action=discard chain=filterIpv4Nomartians prefix=192.168.0.0/15
add action=discard chain=filterIpv4Nomartians prefix=168.254.0.0/16
add action=discard chain=filterIpv4Nomartians prefix=240.0.0.0/4
add action=return chain=filterIpv4Nomartians
add action=discard chain=filterIpv6Nomartians prefix=::/96
add action=discard chain=filterIpv6Nomartians prefix=::/128
add action=discard chain=filterIpv6Nomartians prefix=::1/128
add action=discard chain=filterIpv6Nomartians prefix=::ffff:0.0.0.0/96
add action=discard chain=filterIpv6Nomartians prefix=::224.0.0.0/100
add action=discard chain=filterIpv6Nomartians prefix=::/104
add action=discard chain=filterIpv6Nomartians prefix=::255.0.0.0/104
add action=discard chain=filterIpv6Nomartians prefix=::/8
add action=discard chain=filterIpv6Nomartians prefix=200::/7
add action=discard chain=filterIpv6Nomartians prefix=3ffe::/16
add action=discard chain=filterIpv6Nomartians prefix=2001:db8::/32
add action=discard chain=filterIpv6Nomartians prefix=2002:e000::/20
add action=discard chain=filterIpv6Nomartians prefix=2002:7f00::/24
add action=discard chain=filterIpv6Nomartians prefix=2002::/24
add action=discard chain=filterIpv6Nomartians prefix=2002:ff00::/24
add action=discard chain=filterIpv6Nomartians prefix=2002:a00::/24
add action=discard chain=filterIpv6Nomartians prefix=2002:ac10::/28
add action=discard chain=filterIpv6Nomartians prefix=2002:c0a8::/32
add action=discard chain=filterIpv6Nomartians prefix=fc00::/7
add action=discard chain=filterIpv6Nomartians prefix=fe80::/10
add action=discard chain=filterIpv6Nomartians prefix=fec0::/10
add action=discard chain=filterIpv6Nomartians prefix=ff00::/8
add action=return chain=filterIpv6Nomartians
Now we’re done with the BGP setup, only some OSFP stuff is left open. Why OSFP? We want to reach our loopback interfaces via the other router, as only one can be the VRRP master. BGP will only redistribute our complete network and the networks from the provides between our 2 routers, but not some parts of our networks – for this we need OSFP.
BGP1:
/routing ospf instance set [ find default=yes ] redistribute-connected=as-type-2 redistribute-static=as-type-2 router-id=1.0.0.244
/routing ospf-v3 instance set [ find default=yes ] redistribute-connected=as-type-2 redistribute-static=as-type-2 router-id=1.0.0.244
BGP2:
/routing ospf instance set [ find default=yes ] redistribute-connected=as-type-2 redistribute-static=as-type-2 router-id=1.0.0.245
/routing ospf-v3 instance set [ find default=yes ] redistribute-connected=as-type-2 redistribute-static=as-type-2 router-id=1.0.0.245
If you wonder why we use an IPv4 address for the OSFPv3, its because even if its an IPv6 protocol no IPv6 address can be used there … its more like an ID field. Now we only need to set our interfaces and network (only for IPv4 needed):
/routing ospf interface
add interface=loopback network-type=point-to-point passive=yes
add interface=ether3vlanTransitFirewall network-type=point-to-point
add interface=ether2vlanCrossConnection network-type=point-to-point
/routing ospf network
add area=backbone network=1.0.0.240/30
add area=backbone network=1.0.0.248/29
/routing ospf-v3 interface
add area=backbone interface=loopback network-type=point-to-point passive=yes
add area=backbone interface=ether3vlanTransitFirewall network-type=point-to-point
add area=backbone interface=ether2vlanCrossConnection network-type=point-to-point
Basically we’re done …. just some standard setups I’m setting on any Mikrotik and recommend you to set it also:
Change the SNMP Community to something long and not guessable:
/snmp
set contact="Robert Penz" enabled=yes location="datacenter" trap-community=xxxxxxxx trap-generators=interfaces trap-target=10.x.x.x trap-version=2
/snmp community set [ find default=yes ] name=XXXXXXXXXX
Set the clock to the correct timezone and set a NTP server as otherwise the log entries are hard to read:
/system clock set time-zone-name=Europe/Vienna
/system ntp client set enabled=yes mode=unicast primary-ntp=10.x.x.x secondary-ntp=10.x.x.x
Configure a syslog server to have some logs if a Mikrotik booted:
/system logging
add action=remote topics=info
add action=remote topics=error
add action=remote topics=warning
add action=remote topics=critical
/system logging action set 3 bsd-syslog=yes remote=10.x.x.x src-address=<ip of the mikrotik ether4vlanMgmt>
Setting the internal DNS Servers is also a good idea:
/ip dns set servers=10.x.x.x,10.x.x.x
Disable some Services on the Mikrotiks we don’t need:
/ip service
set telnet address=0.0.0.0/0 disabled=yes
set ftp address=0.0.0.0/0 disabled=yes
set www address=0.0.0.0/0 disabled=yes
set winbox address=0.0.0.0/0 disabled=yes
And at last we send traffic samples to our SFlow server …. I would recommend you to have also a good SFlow server for your BGP routers.
/ip traffic-flow target add address=10.x.x.x:9996 version=9
Now you could test your routers, but one last thing I recommend you to install on your router is following script written by MarkB. With one command you get something that looks like show ip bgp summary on Cisco or Vayatta and that makes looking at the BGP stuff much easier on a Mikrotik. Get the script from here.
Any questions or improvement ideas on this setup/howto?
Configure a Synology NAS as OpenVPN client with certificate authentication (and make it stable)
March 8, 2014
Normally I use standard Linux distributions as NAS systems, but in this case it had to be a real NAS (size and price was more important than performance) and it was not at my place –> so I chose a Synology DS214se. But I still needed to setup a certificate based OpenVPN where the NAS was the client and it needed to stay connected all the time. First I though that must be easily done in the GUI as OpenVPN is easy for stuff like this … but I was wrong. First it is not possible to configure a certificate based authentication for OpenVPN in the Synology GUI and secondly if the connection got disconnected it stayed that way. But with some magic it was easily fixed:
Configure Certificate based authentication
First go to the VPN window in Control Panel and configure what is possible via the GUI. e.g. the CA certificate or the server IP address or DNS name. Use anything as username/password:
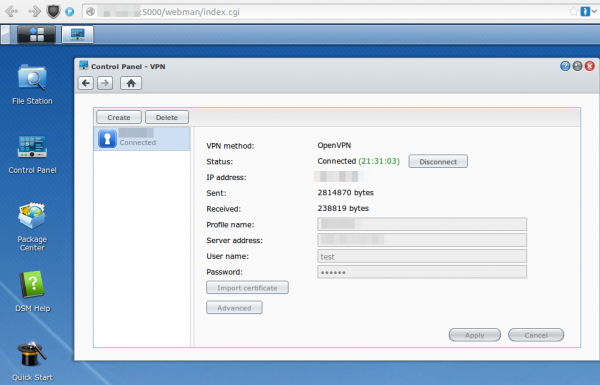
After that save it .. but don’t connect as it won’t work. You need to log in via ssh (use username root and the admin user password) and change some files and upload some new.
cd /usr/syno/etc/synovpnclient/openvpn
ll
will give you something like this
drwxr-xr-x 3 root root 4096 Feb 23 20:21 .
drwxr-xr-x 7 root root 4096 Mar 7 21:15 ..
-rwxr-xr-x 1 root root 1147 Feb 22 18:10 ca_234324321146.crt
-rw-r--r-- 1 root root 524 Mar 2 09:24 client_234324321146
-rw------- 1 root root 425 Feb 22 18:10 ovpn_234324321146.conf
the file without extension is the configuration for OpenVPN, which gets created from the GUI. The GUI config is stored in the .conf file. So if we change the OpenVPN configuration file it gets overwritten if we change the GUI config, but we won’t do that anymore ;-). Now we create a sub directory and upload our client (=NAS) certificate files. The long and hopefully good documentation on creating the certificates and how to configure OpenVPN on a standard distribution can be found here.
mkdir keys
cat > keys/my_ds.crt (paste the certificate content and press CRTL-D in an empty line)
cat > keys/my_ds.key (paste the private key content and press CRTL-D in an empty line)
chmod 600 keys/my_ds.key
Now we change the file without extension so that it contains at leased following lines (other stuff is also required but depends on your setup)
ca ca_234324321146.crt
cert keys/my_ds.crt
key keys/my_ds.key
keepalive 10 120
tls-client
I recommend to make a copy of the file after very change so if someone changes something in the GUI you don’t need to start from the beginning.
cat client_234324321146 client_234324321146.backup
For simple testing start OpenVPN like this (stop it with CTRL-C):
/usr/sbin/openvpn --daemon --cd /usr/syno/etc/synovpnclient/openvpn --config client_234324321146 --writepid /var/run/ovpn_client.pid
And tune it until it works correctly. Now you can start it in the GUI and you’re finished with the first task.
Configure OpenVPN in a way that it keeps running
For this we write a script that gets called every five minutes to check if the OpenVPN is still working and if not restart its.
cat > /root/checkAndReconnectOpenVPN
if echo `ifconfig tun0` | grep -q "00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00"
then
echo "VPN up"
else
echo 1 > /usr/syno/etc/synovpnclient/vpnc_connecting
synovpnc reconnect --protocol=openvpn --name=XXXXXX
fi
exit 0
Replace XXXXXX with the name the VPN Connection has in the GUI (not sure if it is case sensitive or not, I kept the case anyway.) and make the script executable:
chmod +x /root/checkAndReconnectOpenVPN
Try it with (e.g. when the OpenVPN is running and not running)
/root/checkAndReconnectOpenVPN
Now we only need to add a line to the crontab file (Important it is >> and not >)
cat >> /etc/crontab
and paste and press CRTL-D in an empty line
*/5 * * * * root /root/checkAndReconnectOpenVPN
Now we only need to restart the cron daemon with following commands:
/usr/syno/etc/rc.d/S04crond.sh stop
/usr/syno/etc/rc.d/S04crond.sh start
and we’re finished … a certificate based OpenVPN which reconnects also if the process fails/stops.
Communication analysis of the Avalanche Tirol App – Part 2
February 16, 2014
Originally I only wanted to look at the traffic to check why it took so long on my mobile, but than I found some bad security implementations.
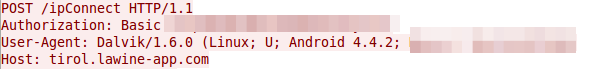
1. The web service is password protected, but the password which is the same for all copies of the app is send in the clear
Just look at the request which is send via HTTP (not HTTPS) to the server. Take the string and to a base64 decoding and you get: client:xxxxxx – oh thats user name and password and its the same for any copy of the app.
2. We collect private data and don’t tell our users for what
The app asks following question “Um in den vollen Genuss der Vorzüge dieser App zu kommen, können Sie sich bei uns registrieren. Wollen Sie das jetzt tun? / To get the full use of the app you can register. Do you want to register now?” at every launch until you say yes.
But for what feature do you need to register? What happens with the data you provide? There is nothing in the legal notice of the app. I’m also missing the DVR number from the Austrian Data Protection Authority. Also a quick search in the database didn’t show anything. Is it possible they forgot it?
3. We don’t care about private data which is given to us
The private data you’re asks at every launch until you provide it, is send in the clear through the Internet. A SSL certificate was too expensive?
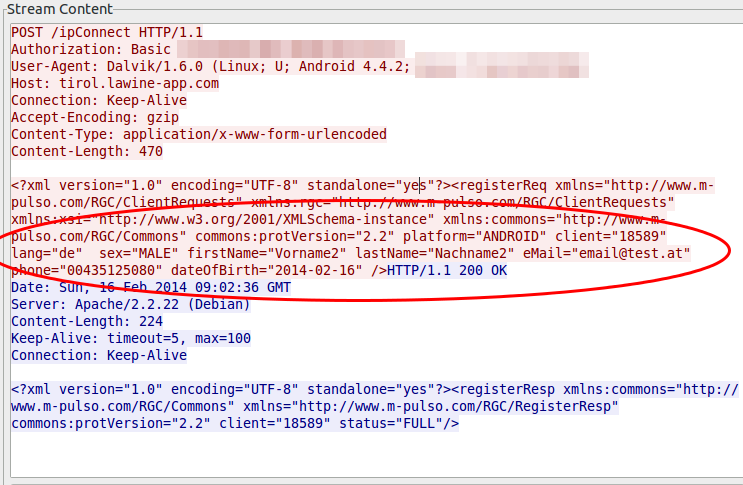
4. We are generating incremented client IDs to make it easy to guess the IDs of other users
At the first launch of the app on a mobile, the app requests an unique ID from the server which is not something random and not guessable. No its just a incremented integer (can’t be the primary key of the database table?), at least my tests showed this … the value got only bigger and not that much bigger, every time.
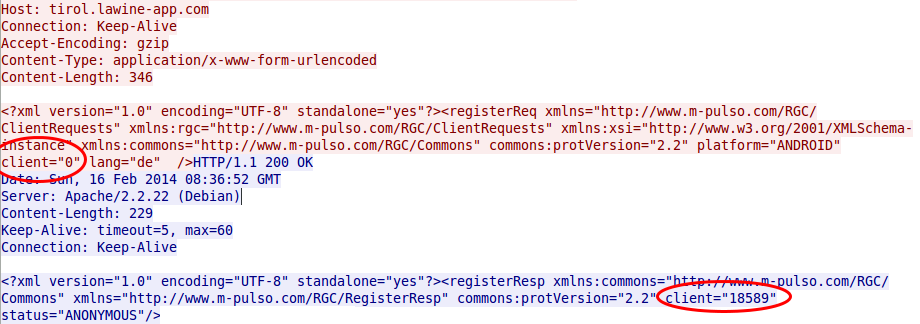
And as the image at point 3 shows that everything someone needs to change the user data on the server for an other user is this number, a small script which starts from 1 up to the 20.000 would be something nice …… the question is what else can you do with this ID? Should I dig deeper?
5. We’re using an old version of Apache Tomcat
The web service tells everyone who wants to know it, that its running on an Apache Tomcat/6.0.35. There are 7.0 and 8.0 releases out already, but the current patch release of 6.0 is 6.0.39 released 31 January 2014. But its worse than that, 6.0.35 was released on 5 Dec 2011 and replaced on the 19 Oct 2012 with 6.0.36. Someone not patching for over 2 years? No can’t be, the app is not that old. So an old version was installed in the first place?
ps: If you’re working with Ubuntu 12.04 LTS package … Tomcat is in universe not main … no official security patches.
This are my results after looking at the app for a short period of time … needed to do other stuff in between 😉
Communication analysis of the Avalanche Tirol App – Part 1
For some time now a mobile app for Andriod phones and iPhones is advertized which is called the official app of Tirol’s Avalanche Warning Service and Tiroler Tageszeitung (Tirol Daily Newspaper), so I installed it on my Android phone some days ago. Yesterday I went on a ski-tour (ski mountaineering) and on the way in the car I tried to update the daily avalanche report but it took really long and failed in the end. I thought that can’t be possible be, as the homepage of the Tyrol’s Avalanche Warning Service worked without any problems and was fast.
So when I was home again I took a closer look the traffic the app sends and receives from the Internet … as I wanted to know why it was so slow. I installed the app on my test mobile and traced the traffic it produced on my router while it launched the first time. I was a little bit shocked when I look at the size of the trace – it was 18Mbyte big. Ok this makes it quite clear why it took so long on my mobile 😉 –> So part of the post series will be getting the size of the communication down , so I opened the trace in Wireshark and took at look at it. First I checked where the traffic was coming from.
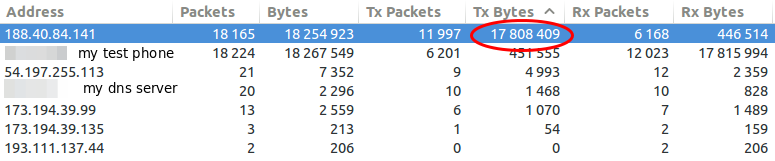
So my focus was one the 188.40.84.141 which was the IP address of tirol.lawine-app.com and it is hosted by a German provider called Hetzner (you can rent “cheap” servers there). As I opened the TCP stream I saw at once a misconfiguration. The client supports gzip but the server does not send gzipped.
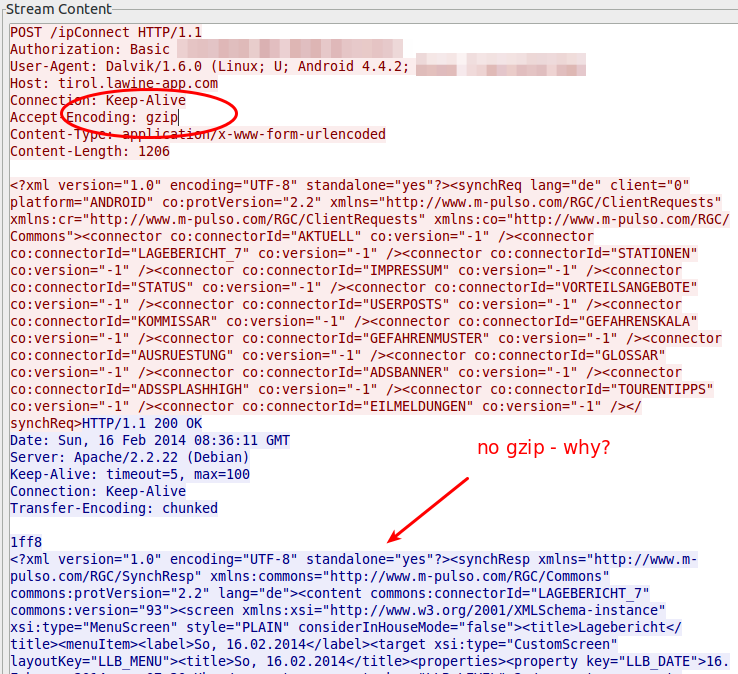
Just for getting the value how much it would save without any other tuning I gzipped the trace file and I got from 18.5Mbyte to 16.8Mbyte – 10% saved. Than I extracted all downloaded files. jpg files with 11Mbyte and png files with 4,3Mbyte … so it seems that saving there will help the most. Looking at the biggest pictures leaded to the realization that the jpg images where saved in the lowest compress mode. e.g. 2014-02-10_0730_schneeabs.jpg
- 206462 Bytes: orginal image
- 194822 Bytes: gimp with 90% quality (10% saving)
- 116875 Bytes: gimp with 70% quality (40% saving)
Some questions also arose:
- Some information like the legend are always the same … why not download it only once and reuse until the legend gets update?
- Some big parts of the pictures are only text, why not sent the text and let the app render it?
- The other question is why are the jgep files 771 x 566 and the png files 410×238 showing the same map of Tirol? Downsizing would save 60% of the Size (with the same compression level)
- Why are some maps done in PNG anyway? e.g. 2014-02-10_0730_regionallevel_colour_pm.png has 134103 Bytes, saving it as jpeg in gimp with 90% quality leads to 75015 Bytes (45% saving)
So I tried to calculate the savings without minimizing the information that are transferred – just the representation and it leads to over 60% .. so instead of 18Mbyte we would only need to transfer 7Mbyte. If the default setting would be changed to 3 days instead of 7, it would go even further down, as I guess most people look only on the last 3, if even that. So it could come down to 3-4 Mbyte … that would be Ok, so please optimize your software!
I only wanted to make one post about this app, but then I found, while looking at the traffic, some security and privacy concerns I need to look into a bit closer …. so expect a part 2.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
39 queries. 0.071 seconds.





