Filter traffic from and to Tor IP addresses automatically with Mikrotik RouterOS
November 30, 2014
Some newer malware communicates with their command and control servers via the Tor network, in a typical enterprise network no system should connect the Tor network. A other scenario is that you’re providing services which don’t need to be accessed via the Tor network but your servers get attacked from Tor Exit Nodes. In both cases it may be a good defence to filter/log/redirect the traffic on your router. With Mikrotiks RouterOS this is possible. You need also a small Linux/Unix server to help. This server needs to be trustworthy one as the router executes a script this server generates. This is required as RouterOS is only able to parse text files up to 4096 by itself, and the Tor IP address list is longer.
Linux Part
So first we create the script /usr/local/sbin/generateAddTorIPsScript.sh on the Linux server with following content:
#!/bin/sh
# the full path of the file we create
filename=/var/www/html/addTorIPs.rsc
# remove the comment if you want to use the List of All Current Tor Server IP Addresses
#url=http://torstatus.blutmagie.de/ip_list_all.php/Tor_ip_list_ALL.csv
# remove the comment if you want to use the List of All Current Tor Server Exit Node IP Addresses
#url=http://torstatus.blutmagie.de/ip_list_exit.php/Tor_ip_list_EXIT.csv
echo "# This scrip adds Tor IP addresses to an address-list (list created: $(date))" > $filename
echo "/ip firewall address-list" >> $filename
/usr/bin/wget -q -O - $url | sort -u | /bin/awk --posix '/^[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}/ { print "add list=addressListTor dynamic=yes address="$1" " ;}' >> $filename
The filename path works on CentOS, on Ubuntu you need to remove the html directory. Now make the file executable
chmod 755 /usr/local/sbin/generateAddTorIPsScript.sh
and execute it
/usr/local/sbin/generateAddTorIPsScript.sh
No output is good. Make sure that the file is reachable via HTTP (e.g. install httpd on CentOS) from the router. If everything works make sure that the script is called once a day to update the list. e.g. place a symlink in /etc/cron.daily:
ln -s /usr/local/sbin/generateAddTorIPsScript.sh /etc/cron.daily/generateAddTorIPsScript.sh
Mikrotik part
Copy and pasted following to get the script onto the router:
/system script
add name=scriptUpdateTorIPs policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive source="# Script which will download a script which adds the Tor IP addresses to an address-list\
\n# Using a script to add this is required as RouterOS can only parse 4096 byte files, and the list is longer\
\n# Written by Robert Penz <[email protected]> \
\n# Released under GPL version 3\
\n\
\n# get the \"add script\"\
\n/tool fetch url=\"http://10.xxx.xxx.xxx/addTorIPs.rsc\" mode=http\
\n:log info \"Downloaded addTorIPs.rsc\"\
\n\
\n# remove the old entries\
\n/ip firewall address-list remove [/ip firewall address-list find list=addressListTor]\
\n\
\n# import the new entries\
\n/import file-name=addTorIPs.rsc\
\n:log info \"Removed old IP addresses and added new ones\"\
\n"
To make the first try run use following command
/system script run scriptUpdateTorIPs
if you didn’t get an error
/ip firewall address-list print
should show many entries. Now you only need to run the script once a day which following command does:
/system scheduler add interval=1d name=schedulerUpdateTorIPs on-event=scriptUpdateTorIPs start-date=nov/30/2014 start-time=00:05:00
You can use this address list now in various ways .. the simplest is following
/ip firewall filter
add chain=forward comment="just the answer packets --> pass" connection-state=established
add chain=forward comment="just the answer packets --> pass" connection-state=related
add action=reject chain=forward comment="no internal system is allowed to connect to Tor IP addresses" dst-address-list=addressListTor
add chain=forward comment="everything from internal is ok --> pass" in-interface=InternalInterface
Google services seems to be down if you’re accessing them via an IPv6 tunnel provider [Update 2]
November 8, 2014
For one of my Internet connections I use Hurricane Electric as IPv6 tunnel broker and the Google services (also Youtube) seems to be not accessable over it. I searched through the Internet and it seems that this is a more wide spread problem also with other tunnel brokers and other users. It is also interesting that following works.
first the dns request:
$ host www.google.com
www.google.com has address 188.21.9.57
www.google.com has address 188.21.9.56
www.google.com has address 188.21.9.59
www.google.com has address 188.21.9.53
www.google.com has address 188.21.9.52
www.google.com has address 188.21.9.55
www.google.com has address 188.21.9.54
www.google.com has address 188.21.9.58
www.google.com has IPv6 address 2a00:1450:4014:80b::1013
the ping to the IPv6 address works too:
$ ping6 2a00:1450:4014:80b::1013
PING 2a00:1450:4014:80b::1013(2a00:1450:4014:80b::1013) 56 data bytes
64 bytes from 2a00:1450:4014:80b::1013: icmp_seq=1 ttl=57 time=82.5 ms
64 bytes from 2a00:1450:4014:80b::1013: icmp_seq=2 ttl=57 time=93.3 ms
64 bytes from 2a00:1450:4014:80b::1013: icmp_seq=3 ttl=57 time=68.3 ms
64 bytes from 2a00:1450:4014:80b::1013: icmp_seq=4 ttl=57 time=75.5 ms
but a HTTP request runs into a timeout:
$ wget www.google.com
--2014-11-08 11:42:29-- http://www.google.com/
Resolving www.google.com (www.google.com)... 2a00:1450:4014:80b::1013, 188.21.9.56, 188.21.9.59, ...
Connecting to www.google.com (www.google.com)|2a00:1450:4014:80b::1013|:80... connected.
HTTP request sent, awaiting response... 302 Found
Location: http://www.google.de/?gfe_rd=cr&ei=lfNdVKbtEumk8wfgv4DgDg [following]
--2014-11-08 11:42:29-- http://www.google.de/?gfe_rd=cr&ei=lfNdVKbtEumk8wfgv4DgDg
Resolving www.google.de (www.google.de)... 2a00:1450:4014:80b::1017, 188.21.9.52, 188.21.9.56, ...
Connecting to www.google.de (www.google.de)|2a00:1450:4014:80b::1017|:80... connected.
HTTP request sent, awaiting response...
after the initial redirect … so small packets seem to go through but big not .. that looks like an MTU problem.
ps: yes
$ ping6 2a00:1450:4014:80b::1017
PING 2a00:1450:4014:80b::1017(2a00:1450:4014:80b::1017) 56 data bytes
64 bytes from 2a00:1450:4014:80b::1017: icmp_seq=1 ttl=57 time=100 ms
64 bytes from 2a00:1450:4014:80b::1017: icmp_seq=2 ttl=57 time=63.6 ms
works too. 😉
Update:
Take also a look at following links:
- https://www.sixxs.net/forum/?msg=general-12626989
- https://forums.he.net/index.php?topic=3281.0
Update 2:
The PMTUD seems to be not working .. Details on PMTUD und MTU and MSS can be found here. Workaround seems to be to set the MTU size to 1480 – it works for me and in IPv6 that’s MSS 1420 (60byte instead of 40 in IPv4). On a Mikrotik RouterOs it works like this:
/ipv6 firewall mangle add action=change-mss chain=forward new-mss=1420 protocol=tcp tcp-flags=syn tcp-mss=!0-1420 comment="max MTU size in Tunnel 1480 .. workaround for google bug"
On Linux it is similar with iptables:
ip6tables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --set-mss 1420
A practical example how broken MD5 really is
November 5, 2014
Nat McHugh did a wonderful post with two completely different monochrome pictures which have the same MD5 sum. Take a look! MD5 as a secure hash function should provide the properties shown in this Wikipedia article. But as Nat says in his own words:
I believe he is correct, nothing shows better how broken MD5 is than two images with the same MD5 sum and that really nobody should use it anymore for security reasons. Using it for checking file corruption during transfer is Ok, but the hash for ISO files or packages for Linux Distributions you download should not be checked with MD5. CPU power is cheap nowadays. The big ones like Ubuntu, Debian and CentOS already have changed to provide also SHA1 and SHA256 hashes for all the files. OpenSuse provides MD5 and SHA1 … better would be SHA256 too. Anyway use SHA256 were possible to verify your downloads!!
Sony Xperia smart phones have an automatically recreated “Baidu” folder and connect to a server in China
November 1, 2014
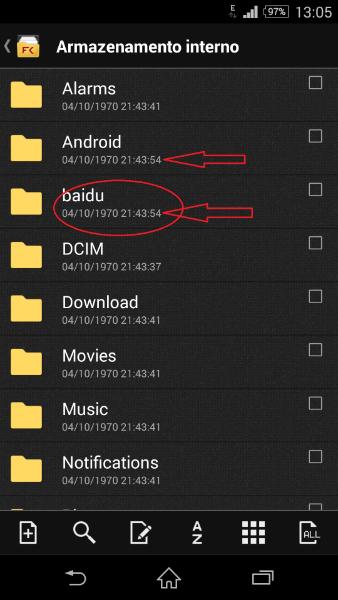
As I’m a user of a Sony Xperia smart phone I pick that thread up. In the Sony support forums a really log thread is running because all current Xperia smart phones got with the Upgrade to Android 4.4 and folder “Baidu” on the internal storage. If you delete it and reboot the phone it gets recreated. Here a screenshot from lggyjp from the forums:
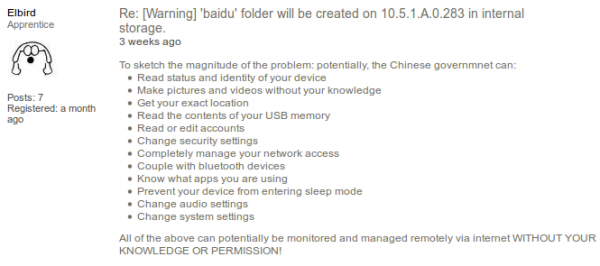
Sony is claiming that this is the connection to Baidu the Chinese Google equivalent, but the setup has some potential implications which gets user upset. An example is the post by Elbrid in the forum:
Following is the response by Sony, first by a support guy called Richard:
This folder will be removed in future software updates for the phone. Until then i can only advise that you delete it manually after a reboot if you want to remove it. It’s safe to just delete it.
and than the post yesterday by responsible manager:
Hey guys
Magnus Hilding here – I’m heading the team developing MyXperia @ Sony Mobile. As Rickard said, we built the app using both protocols to ensure both our Chinese and global users could enjoy MyXperia. However, we’ve designed later versions to package the service relevant to a specific region only – these updates are right around the corner, rolling out soon.
As Rickard said, it’s really nothing to worry about.
/Magnus
If you want to remove it at once and not wait for Sony, take a look at this article which shows the 9 steps needed to get rid of it.
Howto get an A+-Rating at Qualys SSL Labs with Apache 2.2
One of my HTTPS servers currently gets an A- on Qualys SSL Labs test, as I’m running Ubuntu 12.04 LTS with Apache 2.2 which does not support the ECHDE-Cipher suites, which is required for Perfect Forward Secrecy with the Internet Explorer.
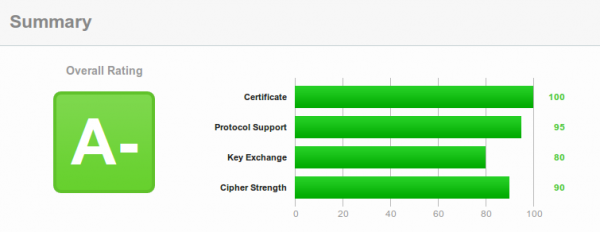
Upgrading to Ubuntu 14.04 needs some major rework for which I currently don’t have the time for.But there is now a trick to get that A-Rating and it is called TLS Interposer. It uses LD_PRELOAD to intercept the OpenSSL API calls and adds some additional features and security settings.
Currently there is no deb package for Ubuntu 12.04, so we need to compile it for our-self:
wget https://github.com/Netfuture/tlsinterposer/archive/master.zip
unzip master.zip
cd tlsinterposer-master/
make
Possible errors:
make: cc: Command not found-> install the gcc (apt-get install gcc)tlsinterposer.c:29:25: error: openssl/ssl.h: No such file or directory–> Install the OpenSSL Development package (apt-get install libssl-dev)
Now we need only an make install and we’re ready to try it. For this we add
export LD_PRELOAD=/usr/local/lib/libtlsinterposer.so
at the end of
/etc/apache2/envvars
and restart Apache with
/etc/init.d/apache2 restart
And you get
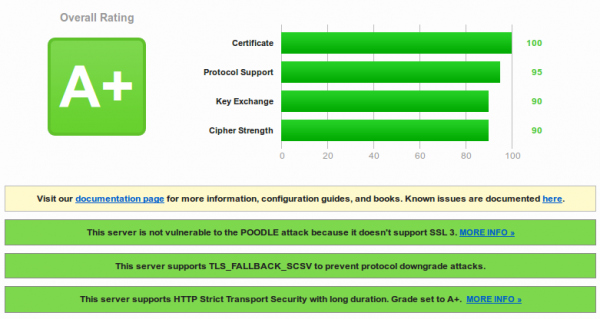
Success!!!
You need also following for an A+ Rating:
- Following needs to be still in the Apache config:
SSLProtocol ALL -SSLv2 -SSLv3
SSLHonorCipherOrder On
SSLCompression Off
# SSLCipherSuite settings will be ignored - You need to HSTS configured, check this link for how to enable it on Apache 2.2
So this is with Ubuntu 12.04 … I’ve tried the same with Centos 6 but I didn’t have success. Following problems did arise
1. Makefile
The Makefile does not support the names of the ssl libs on Centos 6 – when you compile, you get:
tlsinterposer.c:85: error: ‘DEFAULT_SSLLIB’ undeclared here (not in a function)
The Makefile has a regex that does not work with Centos 6. I changed following
# diff Makefile.orig Makefile
32c32
< ldconfig -p | sed -n -e 's/^\t*\(libssl\.so\.[0-9]\.[0-9]\.[0-9]\).*/#define DEFAULT_SSLLIB "\1"/p' > $@
---
> ldconfig -p | sed -n -e 's/^\t*\(libssl\.so\.[0-9][0-9]\).*/#define DEFAULT_SSLLIB "\1"/p' > $@
and deleted the file ssl-version.h and called make again and it compiled. I’ve reported that to author.
2. application’s cipher is not overwritten
Loading the TLS Interposer with putting it in /etc/sysconfig/httpd and than doing an /etc/init.d/httpd restart worked but the application’s cipher didn’t get changed. I could verify that with the test scripts which come with TLS Interposer:
# ./run_tests
gcc -O2 -Wall -Wextra simple_server.c -lcrypto -lssl -o simple_server
Test 1a pass
Test 1b FAIL!
Test 1c pass
Test 1d pass
Test 1e pass
Test 2a pass
Test 2b pass
Test 2c pass
Test 3a pass
Test 3b pass
Test 4a pass
Test 4b pass
Test 4c pass
Test 5a pass
Test 5b pass
Test 5c pass
Test 5d pass
I’ve reported that to the author. If I get an update on this I’ll report in my blog about this.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
32 queries. 0.057 seconds.





