Howto configure a Mikrotik as central DHCP server with switches as DHCP relays
April 27, 2013
I’ve found many articles about how to configure a Mikrotik RouterOS as DHCP relay or as simple DHCP server, but I didn’t find an article about following setup:
- central Mikrotik DHCP Server (e.g. in the data center)
- multiple VLANs/subnets for clients which are connected via a Layer3 Switch (or even more hops) to the central data center
According to the Mikrotik Wiki and the described options it is possible but there is no example shown and everyone uses the setup wizard to configure a DHCP Server. I’ll get most people don’t know what happens in the background … I’ll show this the old fashioned way. 😉
Setup for this example/howto
For this example we assume that we’ve 4 VLANs with following subnets:
- 10.88.0.0/24 (data center VLAN for the servers and the DHCP server)
- 10.88.10.0/24 (clients network location 1)
- 10.88.11.0/24 (clients network location 2)
- 10.88.12.0/24 (clients network location 3)
The Mikrotik has the IP 10.88.0.100 and connected via ether1 to the data center VLAN. The Layer3 switches use always the .1 IP address in the clients networks.
Layer3 Switches / DHCP Relay
Most (if not all) switches which are able to perform at least simple layer 3 tasks (often also labeled as Layer2+ switches) are able to forward DHCP requests. Check the manual of the switch for this. One setting I came across sometimes leads to problems. It is called “DHCP Relay delay” and is sometimes set to 1 or 2 seconds in the the default configuration. This setting allows a local DHCP Server to answer faster, but sometimes (specially embedded clients) don’t wait that long and run into an error. If there is no local DHCP server set this timer to 0 seconds.
You’ll need to set the DHCP Server IP on the switch to the IP of the Mikrotik.
Mikrotik as DHCP Server
First we configure our pools of the client networks, the mikrotik will give out IPs from this ranges:
/ip pool
add name=poolClientsLocation1 ranges=10.88.10.10-10.88.10.250
add name=poolClientsLocation2 ranges=10.88.11.10-10.88.11.250
add name=poolClientsLocation3 ranges=10.88.12.10-10.88.12.250
Now we need to set the configuration the DHCP Server will handout the clients:
/ip dhcp-server network
add address=10.88.10.0/24 dns-server=10.88.0.100 gateway=10.88.10.1
add address=10.88.11.0/24 dns-server=10.88.0.100 gateway=10.88.11.1
add address=10.88.11.0/24 dns-server=10.88.0.100 gateway=10.88.12.1
And at last we configure which DHCP Relay gets which configuration/pool:
/ip dhcp-server
add address-pool=poolClientsLocation1 authoritative=yes disabled=no interface=ether1 lease-time=1w name=dhcpClientsLocation1 relay=10.88.10.1
add address-pool=poolClientsLocation2 authoritative=yes disabled=no interface=ether1 lease-time=1w name=dhcpClientsLocation2 relay=10.88.11.1
add address-pool=poolClientsLocation3 authoritative=yes disabled=no interface=ether1 lease-time=1w name=dhcpClientsLocation3 relay=10.88.12.1
This is all … 😉
How to get IPv6 with a Mikrotik router via an IPv6 tunnel broker
March 2, 2013
You want to try IPv6 but you’re provider doesn’t give you IPv6 addresses? If your router is a Mikrotik this howto will show you how to use an IPv6 tunnel brocker. This setup will also work for guys with a dynamic IP as most home users do.
Signup with an IPv6 tunnel broker
Go to this Wikipedia page for a list of IPv6 tunnel brokers. I’ve chosen the guys at Hurricane Electric as its free and works also with dynamic IP addresses. Other brokers which provide also 6in4 (in RouterOS called /interface 6to4) which provide a method to update of your IP address via a web URL will work too. If you’ve a static IPv4 address the choosing gets even easier.
Following shows whats needs to be done if you use Hurricane Electric as tunnel broker. The tunnel broker wants to be able to ping your router via IPv4 … lets enable that (only if you disabled ping in the first place)
/ip firewall filter add chain=input icmp-options=8:0 protocol=icmp src-address=66.220.2.74
Move this rule to a place before the blocking rule. This rule is made in a way that it opens the least possible hole which is needed for the tunnel broker to work. Now go to the broker website and do following:
- Click on “Create Regular Tunnel”
- Under “IPv4 Endpoint (Your side):” enter your current IPv4 address
- Choose a server location, for better performance choose one thats not that far away from you. 😉
- After Creating the Tunnel you’ll be shown a web page with following important information you’ll need later:
- Tunnel ID
- Server IPv4 Address
- Server IPv6 Address
- Client IPv4 Address
- Client IPv6 Address
- Routed /64
For the commands I’ll use “Tunnel ID” if you should use your Tunnel Id and so on.
Mikrotik Tunnel Setup
First make sure that you’ve the IPv6 package enabled -use following command:
[admin@mikrotik] > /system package print
Flags: X - disabled
# NAME VERSION SCHEDULED
0 X ipv6 6.0rc11
.....
In this example it is not enabled, so we need to enable it and reboot.
[admin@mikrotik] > /system package enable ipv6
[admin@mikrotik] > /system reboot
Now it should look like this:
[admin@mikrotik] > /system package print
Flags: X - disabled
# NAME VERSION SCHEDULED
0 ipv6 6.0rc11
.....
After this is done we can start configuring. First we need to create the tunnel endpoint on our side.
[admin@mikrotik] /ip firewall filter> /interface 6to4 add comment="Hurricane Electric IPv6 Tunnel Broker" disabled=no local-address="Client IPv4 Address" mtu=1280 name=sit1 remote-address="Server IPv4 Address"
After that we need to tell the router this is his new default gateway.
[admin@mikrotik] /ip firewall filter> /ipv6 route add dst-address=2000::/3 gateway="Server IPv6 Address"
And of course we need also an IPv6 address.
[admin@mikrotik] /ip firewall filter> /ipv6 address add address="Client IPv6 Address"/64 advertise=yes eui-64=no interface=sit1
Now we can test our setup the first time. Lets check if the router is able to ping an IPv6 address in the Internet … we use for this the Google DNS servers.
[admin@mikrotik] > ping 2001:4860:4860::8844
HOST SIZE TTL TIME STATUS
2001:4860:4860::8844 56 58 36ms echo reply
2001:4860:4860::8844 56 58 35ms echo reply
2001:4860:4860::8844 56 58 46ms echo reply
sent=3 received=3 packet-loss=0% min-rtt=35ms avg-rtt=39ms max-rtt=46ms
If this does not work .. try to ping “Server IPv6 Address”. If this does work you got something wrong which the default gateway. If this also does not work .. check your tunnel setup and your IPv6 address.
Mikrotik Setup for the Clients
Now we got it working for the Mikrotik but it would be even better to have IPv6 for the clients. To achieve this we need to configure an IPv6 address on the LAN interface and enable
the advertisement to the clients. Take the “Routed /64” address and add an 1 between the :: and the “/” – this give you the first IP address in the routed subnet.
e.g. 2001:xxx:xxx:xxx::/64 –> 2001:xxx:xxx:xxx::1/64
This leads to following command:
/ipv6 address add interface="your LAN interface" address="IP address in your routed IPv6 subnet" advertise=yes
Now wait a little bit (some minutes) and check if your client operation system got an IPv6 address from the routed subnet. I’ll show it here on an Ubuntu 12.04:
$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:xx:xx:xx:xx:xx
inet addr:10.xx.xx.xx Bcast:10.xx.xx.xx Mask:255.255.255.0
inet6 addr: 2001:470:xxx:xxx:xxx:xxx:xxx:xxx/64 Scope:Global
inet6 addr: 2001:470:xxx:xxx:xxx:xxx:xxx:xxx/64 Scope:Global
inet6 addr: fe80::xxx:xxx:xxx:xxx/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5733100 errors:0 dropped:0 overruns:0 frame:0
TX packets:4191113 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4271914251 (4.2 GB) TX bytes:841997928 (841.9 MB)
Interrupt:22 Memory:f6ae0000-f6b00000
You’ll see 3 IPv6 addresses, which are used for following:
- Scope: Link: Only used for communication within the local VLAN … is always there if IPv6 is enabled on the client
- Scope:Global: The second one has the MAC address of this interface in it. This is already a worldwide IP address, but it will tell everyone your MAC address .. which is not that good. So there is the first global one which uses a random part. This feature is called “privacy extension” and the IP is changed by the system after some time. If the privacy extension is activated this IP will be used for communicating.
If you’ve 2 or better 3 IPv6 addresses you can try to ping the Google DNS server:
$ ping6 2001:4860:4860::8844
PING 2001:4860:4860::8844(2001:4860:4860::8844) 56 data bytes
64 bytes from 2001:4860:4860::8844: icmp_seq=1 ttl=57 time=36.7 ms
64 bytes from 2001:4860:4860::8844: icmp_seq=2 ttl=57 time=39.6 ms
64 bytes from 2001:4860:4860::8844: icmp_seq=3 ttl=57 time=48.6 ms
64 bytes from 2001:4860:4860::8844: icmp_seq=4 ttl=57 time=55.3 ms
So this seems to work .. now we need to check if your DNS server reports IPv4 and IPv6 addresses back .. if this is not the case your need to configure your DNS correctly or change to an other server … e.g. the Google DNS Servers.
We’ll verify the correct working with following command:
$ host robert.penz.name
robert.penz.name has address 108.162.198.82
robert.penz.name has address 108.162.199.82
robert.penz.name has IPv6 address 2400:cb00:2048:1::6ca2:c652
robert.penz.name has IPv6 address 2400:cb00:2048:1::6ca2:c752
robert.penz.name mail is handled by 10 mail.penz.name.
This looks good … now you’ll only need to configure a firewall on your Mikrotik as you’re clients now have IPv6 address which can be reached worldwide. Your IPv4 firewall is not enough – you need to filter in /ipv6 firewall.
Mikrotik Setup for users with a dynamic IPv4 address
Now we need to make sure the tunnel broker knows our new IPv4 address after each change. For this Hurricane Electric’s provides a web URL which is described here. Thats nice as there are already some DynDNS update scripts available in the Mikrotik Wiki.
I’ve changed the 5.x one in following parts:
- “username”: Your Hurricane Electric’s username
- “password”: Your Hurricane Electric’s password
- “hostname”: Your “Tunnel ID”
- I’ve changed the
/tool fetchline by replacingmembers.dyndns.orgwithipv4.tunnelbroker.net - And at last I added
/interface 6to4 set 0 local-address=$currentIPafter:log info ("UpdateDynDNS: Dyndns Update Result: ".$result)line as we need also to change our local tunnel IP address.
Thats it .. call this script every few minutes and you’ll have IPv6 connectivity even after your IP address changes. I’ll hope this article gets others also in the IPv6 world.
IPv6 OpenVZ VEs and Debian/Proxmox as host system
February 24, 2013
A friend of mine got a new root server and asked me to help him set it up. And of course I helped and as he got a free IPv6 subnet I thought lets configure it. He is running Proxmox as his host system, which is based on Debian.So this guide is also true for Debian systems which have OpenVZ installed.
- You want to use IPv6 for the host system, you need to add at least following to
/etc/network/interfaces
iface vmbr0 inet6 static
address 2001:xxxx:xxxx:xxx::1
netmask 64
up ip -6 route add default via 2001:xxxxx:beef::1 dev vmbr0
down ip -6 route del default via 2001:xxxxx:beef::1 dev vmbr0Replace
vmbr0witheth0if you’re not using Proxmox and only OpenVZ on Debian. - The ISP my friend has the server located at uses a default gateway, which is not in his IPv6 subnet, you need therefore add a host route. Which is done be following 2 lines
up ip -6 route add 2001:4ba0:fff7:1:beef::1 dev vmbr0
down ip -6 route del 2001:4ba0:fff7:1:beef::1 dev vmbr0 - Restart the networking with:
/etc/init.d/networking restart - Test it with following:
ping6 yourOwnIPping6 defaultGWping6 2001:4860:4860::8888(Google IPv6 DNS Server)
- Add following to
/etc/sysctl.confand make sure it is not defined two times
# IPv6 Packet Forwarding and Proxy NDP
net.ipv6.conf.default.forwarding = 1
net.ipv6.conf.all.forwarding = 1
net.ipv6.conf.default.proxy_ndp = 1
net.ipv6.conf.all.proxy_ndp = 1 - Call
sysctl -pto activate it at once (so no reboot is required) - Go to
/etc/vz/vz.confand make sure following is in there
IPV6="yes" - You currently can’t add an IPv6 address through the web GUI of Proxmox – so you need to use the CLI (replace with a IP adresse from your IPv6 range
vzctl set <VEID> --ipadd 2001:xxx:xxx::xxx --save - restart the VE, and try the ping stuff from step 4 in the VE. (ps: It can take up to 5 pings before you get a response the first time.)
More is not needed … its quite easy!
ps: don’t forget to add an IPv6 DNS server, if it is a IPv6 only VE. This can currently not be done via Proxmox web GUI.
pps: iptables does not filter IPv6 .. you need ip6tables for this. don’t think that you’re secure, if you didn’t open anything with iptables.
List of IEEE 802.1x hotfixes for Windows 7
February 16, 2013
Most companies which want to enable 802.1x for their wired network run Windows 7 SP1. After activating 802.1x you’ll run into various problems with your Windows 7 boxes. It will work fine in lap tests but it will fail in the real world. Why is that? Because there are many 802.1x bugs in it.
Normally I blog about Linux, networking and security and not Windows related stuff. I’m not an Windows expert but I needed to get it authenticated with my network so needed to look into the matter. I hope it helps other networks guys. I’m working for over 8 month (no not all the time 😉 ) now to get Windows 7 SP1 100% of the time working with 802.1x. Its working 99% of the time, but there are still errors (under rare and special condition) that occur. ;-(
At the time of writing this list I didn’t find any other site that lists the available hotfixes, so I though I start a list. And the description texts from Microsoft to these hotfixes are sometimes brain dead. Anyway some entries are the result of working with the Microsoft Premier Support on cases. If you’ll find any other hotfix, fixit, … please let me know.
ps: We’re using EAP-TLS so I can only write about patches I needed for it.
- KB2481614
If you’re configuring your 802.1x settings via Group Policy you’ll see sometimes EAP-PEAP request from clients in your radius server log during booting even if you’ll set EAP-TLS. This error happened in our case with 1/3 of the boots with some models. The error is caused by a timing problem during startup. Sometimes the 802.1x is faster and sometimes the Group Policy is, and if the 802.1x is faster than the default configuration is taken, which is PEAP. Which lead to a EAP-NAK by the radius server. - KB980295
If an initial 802.1x authentication is passed, but a re-authentication fails, Windows 7 will ignore all later 802.1x requests. This hotfix should also fix a problem with computers waking up from sleep or hibernation – but we’ve disabled these features so I can’t comment on them. - KB976373
This hotfix is called “A computer that is connected to an IEEE 802.1x-authenticated network via another 802.1x enabled device does not connect to the correct network”. I can’t comment on this, as we’ve not deployed 802.1x for our VoIP phones at this point. But it solves one other problem, which is described here. The Windows Vista hotfix for the same problem, linked in the article (There is a third hotfix related but not linked in the article, its for XP – so it seems the problem is through the whole product line), states that if an error occurs Windows is normally hard-coded to ignore EAPOL packets for 20min. I would guess it is the same for Windows 7 too. The linked article tells you to install the patch and set some registry key to lower the value. - KB2769121
A short time ago I found this one: “802.1X authentication fails on a Windows 7-based or Windows 2008 R2-based computer that has multiple certificates”. At time of writing I’m not sure if it helps for something in my setup. According to the symptoms list of the hotfix, it does not, but maybe it helps for something else, as the one before does. - KB2736878
An other error during booting – this time it happens if the read process starts before the network adapter is initialized. Really seems that they wanted to get faster boot times, no matter the costs. - KB2494172
This hotfix fixes a problem if you’ve installed a valid and invalid certificate for 802.1x authentication. The workaround is just deleting the invalid certificate. I’m not sure at this point if it affects also wired authentication. - KB976210
This problem occurs only during automated build processes and if you use an EAP method which needs user interaction – as I don’t do that I can’t comment on this hotfix.
So far this is my list – with the list you should get running Windows 7 and 802.1x nicely, but it is not perfect – Do you know any other patches or workarounds?
Howto force scheduled DSL reconnects on Mikrotik routers
November 10, 2012
In my last blog post I have shown how to connect to a PPPoA provider with a Mikrotik router and get the public IP address on the router. I also mentioned that my provider has the bad habit of disconnecting every 8h. As thats not exactly 8h, it tends to wander, but I want at least always the same times. This blog post shows you how to do that if you want the same.
What the script basically does is to force a reconnect at a given time once a day. First we need to make sure that we’ve the correct time on the router. The simplest way to do that is following line:
/system ntp client set enabled=yes mode=unicast primary-ntp=91.189.94.4
But you can only use an IP address there, if you want DNS names take a look hat this script. Also verify that you’ve configured the correct time zone with this command:
/system clock set time-zone-name=Europe/Vienna
Verify the current time with
[admin@MikroTik] > /system clock print
time: 20:56:44
date: nov/04/2012
time-zone-name: Europe/Vienna
gmt-offset: +01:00
dst-active: no
Now we need to write the script, which we to in 2 steps. First we create the script ….
/system script add name=scriptForcedDslReconnect source=""
… than we open it in the editor and add the actual code
[admin@MikroTik] > /system script edit 0
value-name: source
After this you get an editor and just copy and paste following lines:
/interface pptp-client set [find name="pptpDslInternet"] disabled=yes
/interface pptp-client set [find name="pptpDslInternet"] disabled=no
/log info message="pptpDslInternet forced reconnect. Done!"
and press CRTL-O. You can now check if all is correct with (everything should be colored in the script)
/system script print
Now we only need to add it to the scheduler
/system scheduler add name=schedularForcedDslReconnect start-time=00:40:00 interval=24h on-event=scriptForcedDslReconnect
And we’re done, it will disconnect always at 00:40, 8:40, 16:40 … as we wanted.
Howto use a Mikrotik as router for a PPPoA DSL Internet connection
November 4, 2012
I live in Austria and the biggest Internet provider is A1 Telekom Austria and they use PPPoA and not PPPoE. I’ve searched through out the Internet to find some documentation on how to configure a Mikrotik router for this. I wanted to have the public IP address on the Mikrotik and not on the provider router/modem. I did not find any documentation. But as I got it working I’ll provide such a documentation now. 😉
1. The Basics
PPPoA is the abbreviation for PPP over ATM or some say PPP over AAL5 and it is used to encapsulate PPP into ATM cells to get into the Internet via ADSL connections. The more commonly used standard in this space is PPPoE (PPP over Ethernet), but which has somewhat more overhead as you need also to encapsulate the Ethernet header too.
There are now two possibilities:
The first is that the provider modem/router handles everything and you get only a private IP address behind the router, and the router masquerade the private IP addresses. This is normally the default as it works for 95% of the customers but your PC or own router does not get a public IP address. You need to use port forwarding if you want to provide services which are reachable from the Internet. And something which I specially need. You don’t get a event when you get disconnected and assigned a new IP address. A1 Telekom Austria has the bad habit to disconnect you every 8 hours … 3 times a day. As I want to have the disconnects always at the same time I need my own router to time it once a day, so it gets reseted to my desired reconnect times.
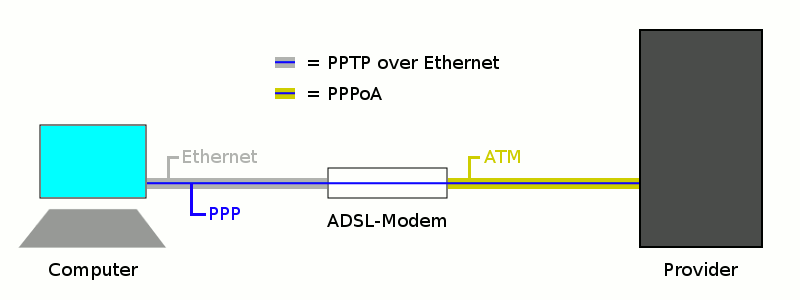
The second way it to get somehow the public IP address on the PC or router. In this case your need a provider modem/router with a PPPoA-to-PPTP-Relays. Take a look at the picture I took from the German Wikipedia(CC-BY-SA-3.0, Author Sonos):
The computer (or Mikrotik router) thinks it establishes a PPTP tunnel with the modem, but instead the modem encapsulates the packets and send them on via ATM to the provider backbone. So the computer or Miktrotik router does not need to be able to talk PPPoA it is enough if it is able to talk PPTP, the rest is handled by the modem.
2. Requirements
But of course there are some requirements:
- The provider modem needs to be able to make a PPPoA-to-PPTP-Relays and which is important you need to be able to configure it, as some provider firmwares restrict that.
- You need to know the username and password which is used for the ppp authentication
- And for the sake of completeness – you need a Mikrotik router 😉
3. Provider modem / router
My provider gave me a Thomson Speedtouch TG585 v7 modem/router. The firmware is old (8.2.1.5) and branded but I was able to upload a new configuration via the web interface.
And as it works stable I did not see a reason to upgrade. I found in the Internet a INI file, which configured the router to PPPoA-to-PPTP-Relays mode. Three important notes:
- If you search the Internet for a configuration file … look for “single user” or “single user mode” (SU), the masquerade mode is called “multi user mode” (MU)
- It is also possible to configure the single user mode via telnet, there are some howto’s out there. The specific ones for Austria are of course in German.
- The version numbering is quite broken. The A1 Telekom Austria branded firmwares are often higher (e.g. 8.6.9.0) than the newer generic firmwares (e.g 8.2.6.5_AA).
After configuring the router as PPPoA-to-PPTP-Relays it has the IP address 10.0.0.138/24 for my setup.
4. Mikrotik PPP configuration
So now to the Mikrotik configuration … we start with resetting the configuration with no defaults.
/system reset-configuration no-defaults=yes
Then we rename the first interface and add a transit network IP address
/interface ethernet set 0 name=ether1vlanTransitModem
/ip address add address=10.0.0.1/24 interface=ether1vlanTransitModem
And now we only need to configure the PPTP
/ppp profile add change-tcp-mss=yes name=pppProfileDslInternet use-compression=no use-encryption=no use-vj-compression=no
/interface pptp-client add add-default-route=yes connect-to=10.0.0.138 disabled=no name=pptpDslInternet password=YourPassword profile=pppProfileDslInternet user=YourUsername
this configuration should lead after connecting the ether1 with the modem to following log entries:
[admin@MikroTik] > /log/print
00:29:03 pptp,ppp,info pptpDslInternet: initializing...
00:29:03 pptp,ppp,info pptpDslInternet: dialing...
00:29:05 pptp,ppp,info pptpDslInternet: authenticated
00:29:05 pptp,ppp,info pptpDslInternet: connected
you should see the IP address too:
[admin@MikroTik] > /ip route print
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme, B - blackhole, U - unreachable, P - prohibit
# DST-ADDRESS PREF-SRC GATEWAY DISTANCE
0 ADS 0.0.0.0/0 xxx.xxx.xxx.xxx 1
1 ADC 10.0.0.0/24 10.0.0.1 ether1vlanTrans... 0
2 ADC xxx.xxx.xxx.xxx/32 yyy.yyy.yyy.yyy pptpDslInternet 0
But if you try to ping something you’ll get
[admin@MikroTik] > ping 8.8.8.8
HOST SIZE TTL TIME STATUS
8.8.8.8 timeout
8.8.8.8 timeout
sent=2 received=0 packet-loss=100%
whats the problem? the router uses the wrong source IP address, try following (the xxx.xxx.xxx.xxx is the IP address from /ip route print (entry 2) )
[admin@MikroTik] > /ping src-address=xxx.xxx.xxx.xxx 8.8.8.8
HOST SIZE TTL TIME STATUS
8.8.8.8 56 46 37ms
8.8.8.8 56 46 36ms
8.8.8.8 56 46 37ms
8.8.8.8 56 46 37ms
8.8.8.8 56 46 37ms
8.8.8.8 56 46 37ms
sent=6 received=6 packet-loss=0% min-rtt=36ms avg-rtt=36ms max-rtt=37ms
Now the Internet connection is working, we just need to make it usable ….
5. Mikrotik on the way to be usable
The first thing we need is a masquerade rule that we use the correct IP address into the Internet, following does the trick.
/ip firewall nat add action=masquerade chain=srcnat out-interface=pptpDslInternet
But we want also a client to test it … so here is the configuration I use for the clients (without explanation as it is not the topic of this Howto)
/interface ethernet set 2 name=ether3vlanClients
/ip address add address=10.23.23.1/24 interface=ether3vlanClients
/ip dns set allow-remote-requests=yes servers=8.8.8.8,8.8.4.4
/ip dns static add address=10.23.23.1 name=router.int
/ip pool add name=poolClients ranges=10.23.23.20-10.23.23.250
/ip dhcp-server add address-pool=poolClients authoritative=yes disabled=no interface=ether3vlanClients name=dhcpClients
/ip dhcp-server network add address=10.23.23.0/24 dns-server=10.23.23.1 domain=int gateway=10.23.23.1
Connect a client behind it, set it to DHCP and everything should work. I hope this Howto demystifies PPPoA and Mirkotik.
UniFi Lab for Ubiquiti UniFi Access Points
October 14, 2012
I don’t know how widely the UniFi Access Points are known. So here are some short facts:
- Central management software which is written in Java and runs basically on any Linux, Windows and MacOS System and can be controlled via browser. At I must say it is a really nice GUI – at least compared to the Motorola one I used previously. 😉
- You only need to buy the Access Point and not also licenses for the management software.
- Various models which include following features: standard PoE, 802.1n, outdoor, 2,4 and 5Ghz, captive portal … The SOHO version for small deployments start at 70-80 Euro per piece, the pro version is at about 200 Euro.
- I’ve it running 2 installations, one with over 60 access points , so it also scales.
Take a look at their site and also at the faq.
Anyway there is now a new software in beta, which the power users of this solution surely like. Its written in Python and is Open Source (modified BSD license). At the moment is does following:
- MAC addresses white list
- Poor signal reconnect (or Minimum RSSI)
- WLANs on/off schedule
- Periodically Reboot APs
You can download UniFi Lab from github. Details are on following wiki page: http://wiki.ubnt.com/UniFi_Lab
And as it is Open Source and in a scripting language it should be easy adopted to your special wishes/needs.
Howto get Ubiquiti AirView running under Ubuntu 12.04
September 9, 2012
Ubiquiti AirView is a spectrum analyzer for the 2.4GHz band, which is sadly End-of-Life, but you can still get it from various online stores. Why would you get such a product? Because it is much much cheaper (around 70 Eur) than the other spectrum analyzers I found on the net and its software runs under Linux. This short howto shows you, how to get it running under Ubuntu 12.04.
First you need to install openjdk-7-jre with following command:
apt-get install openjdk-7-jre
Than you need check which java version is the default one:
$ java -version
java version "1.6.0_24"
As in this case it is the wrong one … change it following command:
$ sudo update-alternatives --config java
There are 2 choices for the alternative java (providing /usr/bin/java).
Selection Path Priority Status
------------------------------------------------------------
* 0 /usr/lib/jvm/java-6-openjdk-i386/jre/bin/java 1061 auto mode
1 /usr/lib/jvm/java-6-openjdk-i386/jre/bin/java 1061 manual mode
2 /usr/lib/jvm/java-7-openjdk-i386/jre/bin/java 1051 manual mode
Press enter to keep the current choice[*], or type selection number: 2
update-alternatives: using /usr/lib/jvm/java-7-openjdk-i386/jre/bin/java to provide /usr/bin/java (java) in manual mode.
As you see I’ve have chosen 2 and the check confirms it:
$ java -version
java version "1.7.0_03"
OpenJDK Runtime Environment (IcedTea7 2.1.1pre) (7~u3-2.1.1~pre1-1ubuntu3)
OpenJDK Server VM (build 22.0-b10, mixed mode)
Now you just need to to download, extract and run the software (don’t forget to insert the AirView into the USB port ;-):
wget http://www.ubnt.com/airview/download/AirView-Spectrum-Analyzer-v1.0.12.tar.gz
tar xzf AirView-Spectrum-Analyzer-v1.0.12.tar.gz
cd AirView-Spectrum-Analyzer-v1.0.12/
./airview.sh
Following screenshot shows it running on my system. I’ve switched to “waterfall view” in the settings. Click onto it to see the unscaled version:
FreeRADIUS and CRLs – Done the right way [Update]
May 28, 2012
Update: I changed the FreeRADIUS in-line CRL verification to an external program – running it now for several month at it works without restart of FreeRADIUS.
While I was implementing 802.1x EAP-TLS with FreeRADIUS I googled for documentation on how to implement Certificate Revocation Lists (CRL) in FreeRADIUS. The first text was in the eap.conf:
# Check the Certificate Revocation List
#
# 1) Copy CA certificates and CRLs to same directory.
# 2) Execute 'c_rehash '.
# 'c_rehash' is OpenSSL's command.
# 3) uncomment the line below.
# 5) Restart radiusd
check_crl = yes
CA_path = /etc/freeradius/certs/CA/
Which is basically correct, but it is so short on information that I googled on and found following posts:
- A solution where you need to combine the CA and the CRL in one File (and you need to restart FreeRADIUS to reload the CRL)
- Also ignoring the c_rehash stuff and using a variable crl_file (and I guess, as in this case as didn’t try it, restart FreeRADIUS to reload the CRL)
Both where not the solution I needed as I didn’t want to restart FreeRADIUS all the time and I have multiple sub CAs. I than started googling for more information on c_rehash, as the version on RHEL5/CentOS5/SL5 don’t need to have a man page. Take a look at this online man page.
And just as info as it is not that clear which package has c_rehash: yum provides "*/c_rehash" --> yum install openssl-perl. Basically c_rehash needs to be provided a directory with .pem files in it (also the CRLs need to be name .pem) and it than creates symlinks with the hashes of the files as names. After I got a prototype working but before I wrote this blog, Erik Inge Bolso wrote this blog post describing the same thing.
You need at least FreeRADIUS 2.1.10 (shipped with Centos/RHEL 5 (inc. updates) and later) for this solution to work.
After I got the prototype working I wrote a script which does download multiple CRLs, converts them from DER (e.g. used by Windows CAs) to PEM, verifies them and than uses c_rehash to hash them for FreeRadius. You need to do following steps to get it working for you.
- Create some directories
mkdir /var/tmp/cacheCRLs
mdir /etc/pki/crl/
- download this script cacheCRLs4FreeRadius.py to /usr/local/sbin/
cd /usr/local/sbin/
wget http://robert.penz.name/wp-content/uploads/2012/05/cacheCRLs4FreeRadius.py
- edit
/usr/local/sbin/cacheCRLs4FreeRadius.pyand change the URLs and names to your CAs - run
/usr/local/sbin/cacheCRLs4FreeRadius.py, no output means no error and check the content of/etc/pki/crl/ - check that your radius config contains following and restart FreeRADIUS after the change
# we're using our own code for checking the CRL
# check_crl = yes
CA_path = /etc/pki/crl/
....
tls {
....
verify {
tmpdir = /var/tmp/radiusd
client = "/usr/local/sbin/checkcert.sh ${..CA_path} %{TLS-Client-Cert-Filename}"
}
}
/usr/local/sbin/checkcert.sh should contain following
#!/bin/sh
output=`/usr/bin/openssl verify -CApath $1 -crl_check $2`if [ -n "`echo $output | /bin/grep error`" ]; then
RC=1
else
RC=0
fi
echo $output
exit $RC
- If you need more performance replace the shell script a C program, as this program is started at every authentication request.
- Try to authenticate with an revoked certificate and you should get following. If you’re running FreeRADIUS with -X you should see following (this log looks a little bit different when using the external program, which is the method I’m using now) :
[eap] Request found, released from the list
[eap] EAP/tls
[eap] processing type tls
[tls] Authenticate
[tls] processing EAP-TLS
[tls] eaptls_verify returned 7
[tls] Done initial handshake
[tls] < << TLS 1.0 Handshake [length 05f8], Certificate --> verify error:num=23:certificate revoked
[tls] >>> TLS 1.0 Alert [length 0002], fatal certificate_revoked
TLS Alert write:fatal:certificate revoked
TLS_accept: error in SSLv3 read client certificate B
rlm_eap: SSL error error:140890B2:SSL routines:SSL3_GET_CLIENT_CERTIFICATE:no certificate returned
SSL: SSL_read failed in a system call (-1), TLS session fails.
TLS receive handshake failed during operation
[tls] eaptls_process returned 4
[eap] Handler failed in EAP/tls
[eap] Failed in EAP select
- run the script via cron in intervals that are required in your setup. e.g. once a day or once every hour
Howto enable SSH public key authentication on Ubiquiti AirOS (e.g. NanoStation2)
March 31, 2012
First you need to check if the ssh service is enabled and than you need to login and use following commands. First you need to make sure your home directory is the same as mine:
echo ~
should return /etc/persistent, which is used in this Howto. So lets start the actual work:
chmod 750 /etc/persistent/
cd /etc/persistent/
mkdir .ssh
chmod 700 .ssh
Type on the machine you want to be able to use for public key login:
cat ~/.ssh/id_dsa.pub | ssh [email protected] 'cat >> /etc/persistent/.ssh/authorized_keys'
Now you should be able to login like this
ssh [email protected]
without a password. If so you need to make sure that it stays so even after a reboot:
cfgmtd -w -p /etc/
Type reboot to test it!
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
36 queries. 0.091 seconds.