Home partition encryption with LUKS under Linux
December 25, 2008
I’m often asked how I crypt my notebooks. I normally crypt only my home partition and sometimes (more on servers in remote locations, than on notebooks) the swap partition. I use for this Linux Unified Key Setup (Luks), as it allows up to 8 passwords for a partition and you can change them without reformatting the partition. It also stores the used encryption method so you can use it also for encrypting external hard disks and you don’t need to keep track which encryption algorithms you used for it.
First you install your notebook with a swap and a root partition, but leave space for a /home partition. After the installation is finished you create the partition e.g. with cfdisk or fdisk. You need to restart your system after creating a new partition. In my example I call it /dev/sda3. Now you can tell cryptsetp (which you need to install on Ubuntu with apt-get install cryptsetup, reboot after installing it if the setup does not work) to create a container with following command
cryptsetup --cipher aes-cbc-essiv:sha256 --key-size 128 luksFormat /dev/sda3
After you did this, you need to open the container with
cryptsetup luksOpen /dev/sda3 home
Now you can format the container:
mkfs.ext3 -m 0 /dev/mapper/home
ps: -m 0 means that no blocks are reserved for root, as it is our home partition.
Now you need to go to the console of your system (ALT-CTRL-F1) and login there and stop the X server (log off before that 😉 ). On Ubuntu you do this by calling /etc/init.d/gdm stop on Kubuntu /etc/init.d/kdm stop.
Now you can mount the new partition on a temporary location and copy your home directory over.
mount /dev/mapper/home /mnt/
cp -a /home/* /mnt/.
Now we need to unmount it and close the crypto container.
umount /mnt/
cryptsetup luksClose home
Now we need to configure the system that it is launched at the boot time. Add following line to /etc/crypttab:
home /dev/sda3 none luks
and in your /etc/fstab you add following:
/dev/mapper/home /home ext3 noatime,nodiratime 0 0
Now everything is done. Reboot your system and you will be prompted for the password of your home partition. If you don’t enter it your system will use the “old” home directory.
BasKet: A KDE application for implementing the “Getting Things Done” method
December 24, 2008
Are you also using a Post-It application (like KNotes) on your computer to store your ideas and todos? At least I do, but I found a better application. Welcome to BasKet Node Pads. It takes your notes, but it also lets share them with others. You can integrate it into Kontact and store not only text but also images, links, email addresses, files and you can even pick a from screen. After you stored you ideas, todos, ….. you surely want to access them easily. BasKet supports this by a full text search or it also allows you to set tags and intelligent todo list management.
Maybe your ideas are secret, if so you should use the buildin encryption of BasKet. And best of all, it is OpenSource and you can download it for KDE or it is already shipped with your distribution of choice.
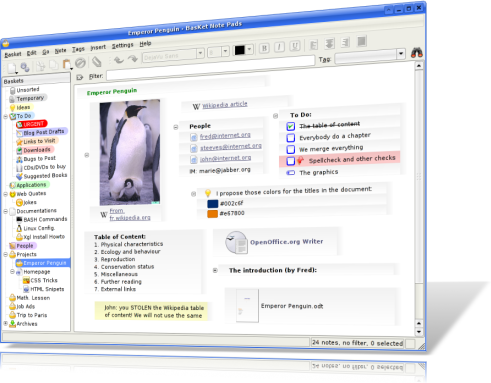
Ah, before I forget it. One of the various ways you can use BasKet is to implement the “Getting Things Done” method to get more organized. Get more information by reading Wikipedia article or this wikisummaries book summary.
ps: Merry Christmas and a happy New Year!
No SWAP Partition, Journaling Filesystems, … on a SSD?
December 7, 2008
I’m going to get an Asus Eee PC 901go, which has a Solid State Disk (SSD) instead of a normal hard disk (HD). As you know me I’ll remove the installed Linux and install my own Kubuntu. I soon started to look at the best way to install my Kubuntu and I found following recommendations copy and pasted on various sites:
- Never choose to use a journaling file system on the SSD partitions
- Never use a swap partition on the SSD
- Edit your new installation fstab to mount the SSD partitions “noatime”
- Never log messages or error log to the SSD
Are they really true or just copy and pasted without knowledge. But first why should that be a problem at all? SSDs have limited write (erase) cycles. Depending on the type of flash-memory cells they will fail after only 10,000 (MLC) or up to 100,000 write cycles for SLC, while high endurance cells may have an endurance of 1–5 million write cycles. Special file systems (e.g. jffs, jffs2, logfs for Linux) or firmware designs can mitigate this problem by spreading writes over the entire device (so-called wear leveling), rather than rewriting files in place. So theoretically there is a problem but what means this in practice?
The experts at storagesearch.com have written an article SSD Myths and Legends – “write endurance” which takes a closer look at this topic. They provide following simple calculation:
- One SSD, 2 million cycles, 80MB/sec write speed (that are the fastest SSDs on the market), 64GB (entry level for enterprise SSDs – if you get more the life time increases)
- They assume perfect wear leveling which means they need to fill the disk 2 million times to get to the write endurance limit.
- 2 million (write endurance) x 64G (capacity) divided by 80M bytes / sec gives the endurance limited life in seconds.
- That’s a meaningless number – which needs to be divided by seconds in an hour, hours in a day etc etc to give…
The end result is 51 years!
Ok thats for servers, but what is with my Asus 901go?
- Lets take the benchmark values from eeepc.it which makes it to a max of 50 MByte/sec. But this is a sequential write, which is not the write profile of our atime, swap, journaling… stuff. That are typically 4k Blocks which leads to 2 MByte/sec. (Side node: The EeePC 901go mount the same disk of SSD ‘EeePC S101, to be precise model ASUS SATA JM-chip Samsung S41.)
- We stay also with the 2 million cycles and assume a 16GB SSD
- With 50 MByte/sec we get 20 years!
- With 2 MByte/sec we get 519 years!
- And even if we reduce the write cycles to 100.000 and write with 2 MByte/sec all the time we’re at 26 years!!
And all this is with writing all the time, even ext3 does write the journal only every 30 secs if no data needs to be written. So the recommendation to safeguard SSDs, as the can not write that often is bullshit!!
So lets take a closer look at the 4 points at the beginning of this blog post.
- Never choose to use a journaling file system on the SSD partitions: Bullshit, you’re just risking data security. Stay with ext3.
- Never use a swap partition on the SSD: If you’ve enough space on your SSD use a SWAP partition it will not be written onto it until there is to less RAM, in which case you can run a program/perform a task which otherwise you could not. And take a look at this article.
- Edit your new installation fstab to mount the SSD partitions “noatime”: That is a good idea if all the programs work with this setting as this will speedup your read performace, specially with many small files. Take also a look at nodiratime.
- Never log messages or error log to the SSD. Come on, how many log entries do you get on a netbook? That is not an email server with > 1000 log lines per second.
Please write a comment if you disagree or even agree with my blog post. Thx!
CPanel – Plesk – Open Source Alternatives?
November 26, 2008
Many people that are in the web hosting business (Ok, most of them “one server hoster”) are talking about CPanel or Plesk and that they can’t do it without them. But I think that this is not necessary true ,as there are open source alternatives.
- The best one I know is ISPconfig. They are reported to have a good support and great howto’s.
- There is also DTC, but it is quite unknown to me,
- There’s also WEBcp.
- Also such programs are SysCP (which is supported by Hetzner and DomainDiscount24) and
- VHCS.
I hope this list helps someone and please at additional programs I mist in the comments. Thx.
Update: Take a look at this comparison.
Do you know SmokePing or StrafePing?
November 25, 2008
The word part “ping” leads you to ICMP packages, Ok – but what is special with Smoke or Strafe Ping? Basically they send multiple ICMP echo requests on block to a given target on block and stores the response-time of each as well as the packet loss. SmokePing is the inventor of this technique and consists of a daemon process which organizes the latency measurements and a CGI which presents the graphs.
Here are some screenshots from the authors homepage:
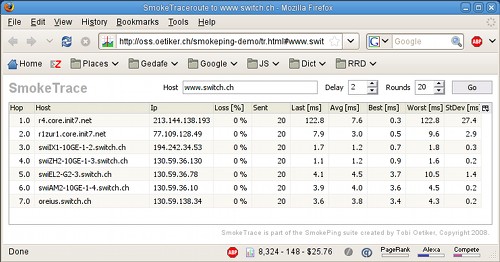
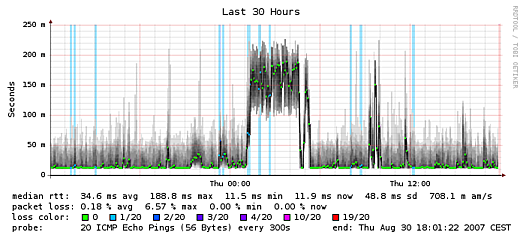
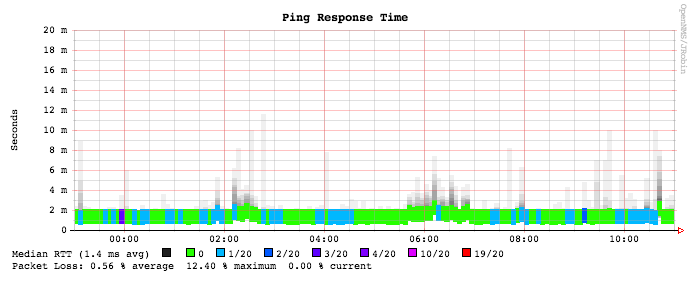
StrafePing is a feature in OpenNMS, which is a network management system and you can activate it for the nodes it monitors. Here is a screenshot for this too:
secure file uploading with scponly
November 23, 2008
If you’re administrating Linux servers you may need someone or some script to copy files onto your server. You could now install a special service like a ftp server or you could use a normal ssh user for this. The problem with the first is that you need an extra service which adds complexity and also provides an additional attack vector. The problem with the normal ssh user is that you provide the script or user functionally on your server that he/it does not need for his/its work (like exciting programs) – this is never a good idea.
What I recommend for this is a program called scponly. It does basically what the name says, if a ssh user has it set as its shell the user is only able to use scp functionality. Ubuntu and Debian provide a package for it but you should read an article like this one to know to setup it up securely. For example it is a really bad idea to allow the user to write into his home directory as a writable home directory will make it possible for the user to subvert scponly by modifying ssh configuration files.
Local audio recording to boost the audio quality for asterisk recording
I’ve written a Howto for recording a podcast with asterisk. This setup is working for our podcast (in German) for some time now, but we wanted to boost our audio quality over the codecs quality asterisk supports. For this we use arecord, a command-line sound recorder for the ALSA soundcard driver, to record locally under Linux. So we use asterisk to talk with each other but normally we use the locally “with CD quality” recorded files for the podcast. The Asterisk recorded stuff is used as backup, as it happened already once that one lost his local recording. 😉
Kubuntu 8.10 Intrepid additional packages install script
November 1, 2008
This script is for my friends, who most know the previous versions already. It installs additional packages for kubuntu 8.10 Intrepid. I use it for the initial setup of a desktop system. First install Kubuntu from CD and than use this script to get the system which, has all codecs and commonly used programs (be it free or non free software) installed. So this blog entry is for my own reference and for my friends. Basically after running this script you’ll have a system which is ready for usage by a standard user.
Workaround for Kubuntu 8.10 (Intrepid) problems with “.local” DNS addresses
October 18, 2008
I installed Kubuntu 8.10 (Intrepid) Beta on one of my Workstations at work this week and I had really problems to get into the internet. Why? We have a PAC (proxy auto-config) script for our proxies and that PAC is reachable under http://pac.companyname.local (You put that into your Browser.). The problem with this setup is that somehow Kubuntu has problems resolving the .local DNS Zones. I did following as a workaround:
$ sudo vim /etc/nsswitch.conf
Replace:
hosts: files mdns4_minimal [NOTFOUND=return] dns mdns4
with:
hosts: files dns
I hope Google helps others to find this post fast, so they don’t need to search that long for a workaround.
Scalp: web log file analyzer to detect attacks
September 29, 2008
The tool Scalp written by Romain Gaucher detects attacks onto web applications by analyzing the Apache log files. This python script uses regular expressions from the PHP-IDS-Project to match attacks against PHP web applications. It is able to detect Cross-Site-Scripting (XSS), Cross-Site Request Forgery(CSRF) and SQL-Injection attacks, but as Apache does not save the variables from POST requests it is only possible to detect GET request attacks. Take a look at this example HTML protocol of the script. The program has no problem with some hundred Megabyte big apache log files, but you can also select a specific time period or kind of attacks. To use the analyzer you need to download the python script an the search pattern file.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
36 queries. 0.083 seconds.





