Jitsi Workaround for CVE-2021-44228/LogJam/Log4Shell
December 10, 2021
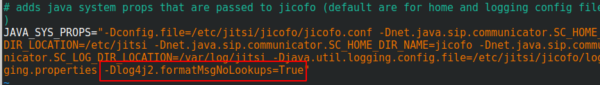
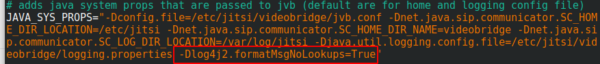
You surely heard of the LogJam / Log4Shell / CVE-2021-44228 – if not, take a look at this blog post. If you’re running Jitsi is most likely vulnerable and as there is no fix currently, you need a workaround which I provide here for you. You need to add -Dlog4j2.formatMsgNoLookups=True at the correct places in the file – the position is important.
/etc/jitsi/jicofo/config
/etc/jitsi/videobridge/config
And restart the processes or restart the server.
No Comments yet »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
42 queries. 0.217 seconds.