Take care if using Ubuntu 12.04 as a client – TLS 1.2 is not enabled by default
October 24, 2014
It got fixed with Ubuntu 14.04 but 12.04 is still supported and many people are still using 12.04 and even with the OpenSSL package update (2014-10-02) TLS 1.2 is not enabled by default. Take a look at this bug report and the statement from Marc Deslauriers (Ubuntu Security Engineer):
That USN doesn’t re-enable TLSv1.2 by default for clients in Ubuntu 12.04. It simply fixes an issue if someone _forced_ TLSv1.2 to be enabled.
You’re asking why we got into that problem in the first place … Marc tells us also this:
Ubuntu 12.04 contains openssl 1.0.1, which supports TLS v1.2. Unfortunately, because of the large number of sites which incorrectly handled TLS v1.2 negotiation, we had to disable TLS v1.2 on the client.
So someone thought again he is smarter than the OpenSSL guys … but this was not the first time …. lets remember this “optimization” of OpenSSL by the Debian guys .. could they please clean up their mess and enable TLS 1.2 by default as in 14.04?
Mikrotik changed the update policy in their license agreement
October 13, 2014
Just as information for you guys using Mikrotik’s RouterOS but who don’t monitor the wiki for changes or are regular readers of the forum. Mikrotik changed its license concerning the updates. Before this summer following paragraph was on their license wiki page:
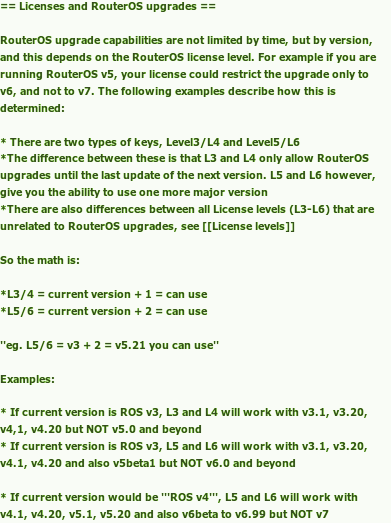
You can take a look at the full old version here. Anyway this whole paragraph has been removed. Also with RouterOS 6.20 the following got removed when typing /system license print on the router:
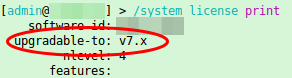
So what does that mean now? jarda from the forums put it nicely:
Protect your PC against the BadUSB attack on Linux and Windows
October 12, 2014
At the Black Hat conference this year researchers from Berlin-based Security Research Labs (SRLabs) showed an attack method they called “BadUSB“, which allowed them, with manipulated USB device firmwares (e.g. from a USB Stick), to simulate an keyboard. With this keyboard they executed commands on the victims computer without he/she knowing it. The victim just inserted a USB stick to copy some data …. but the new keyboard executes some commands in the background.
To protect yourself against such an attack the computer needs to configured in a way that it does not bind any newly added device as new keyboard without asking the user. For Linux there is a kernel feature starting with 2.6.13-rc3 ( = since 2005) which allows to bind and unbind drivers from devices manually from user space. More information can be found on this topic here and here. And this blog post from Christian Vogel shows how to use it against BadUSB. What is currently missing is a simple GUI program which allows you to allow/deny devices with on click.
On the Windows site there is already such a program. This freeware program is made by the German security vendor (e.g. anti virus software) G DATA and is called “G DATA USB KEYBOARD GUARD” and can be downloaded from here. After installing you’ll be prompted following screen if a new keyboard is inserted.
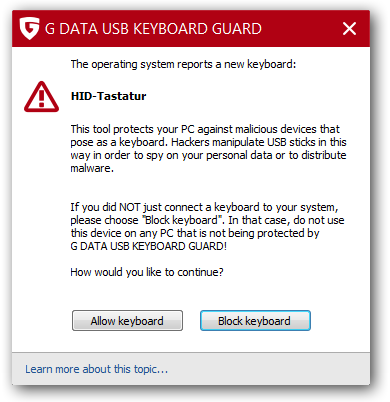
It would be nice if the various desktop environments on Linux add a similar feature … the kernel support is there already.
Check your hardening index of your Linux systems
October 6, 2014
I found a small program called Lynis, which does a system check of your Linux and Unix System. From the homepage:
Lynis is an open source security auditing tool. Primary goal is to help users with auditing and hardening of Unix and Linux based systems. The software is very flexible and runs on almost every Unix based system (including Mac). Even the installation of the software itself is optional!
To test a system is really easy, just download the tar.gz from here and extract the tar as root (otherwise it will complain) and change into its directory and call
./lynis -c
for the interactive mode (waits after each section) or
./lynis -q
for the quick mode which only logs the results to the log file. In both cases the log is written to /var/log/lynis.log.
For the following screenshots a I did setup a test system with some changes to show you some errors and warnings :-):
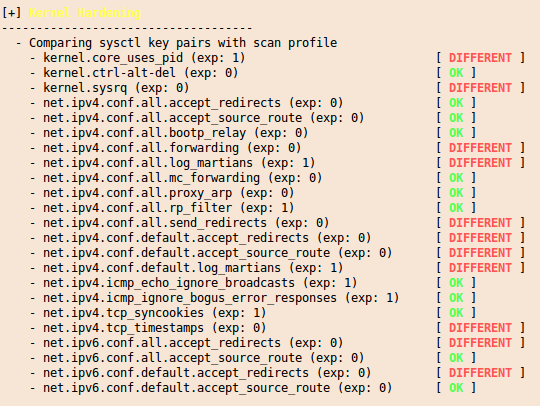
and at the end you get a summary with entries like this:
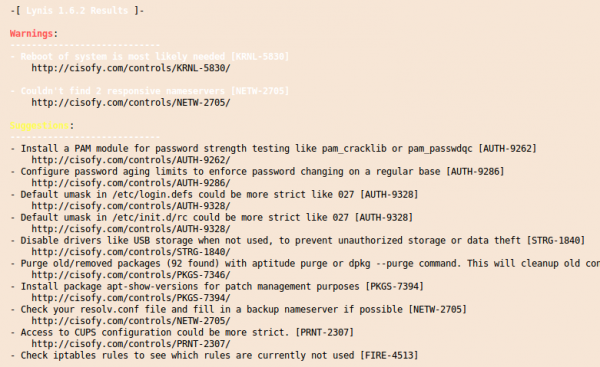
And you’ll get also a “Hardening index” which allows you to compare various systems against each other. 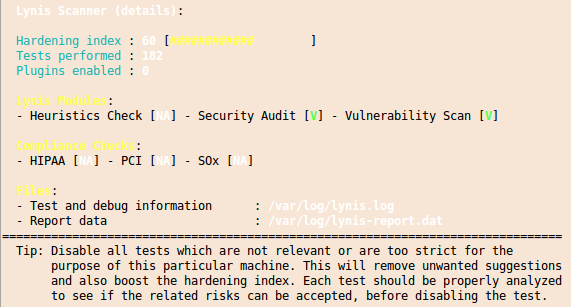
I you want to check multiple systems it it also possible to create an rpm file with the lynis.spec file from the Lynis homepage. You should run this software every time you setup a new system to make sure that you didn’t leave the big whole open.
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
31 queries. 0.057 seconds.





