JavaScript engines comparison
November 1, 2008
A friend of mine has done a comparison of different browsers on a state of the art system. The System runs under Windows XP SP3 on a Core 2 Quad Core CPU (Q9450, 2,66GHz) with 3,5 GB RAM. He did use following test. Smaller bars are better, as the browser was able to process the data faster. The x-axis shows the seconds a browser took for the test.
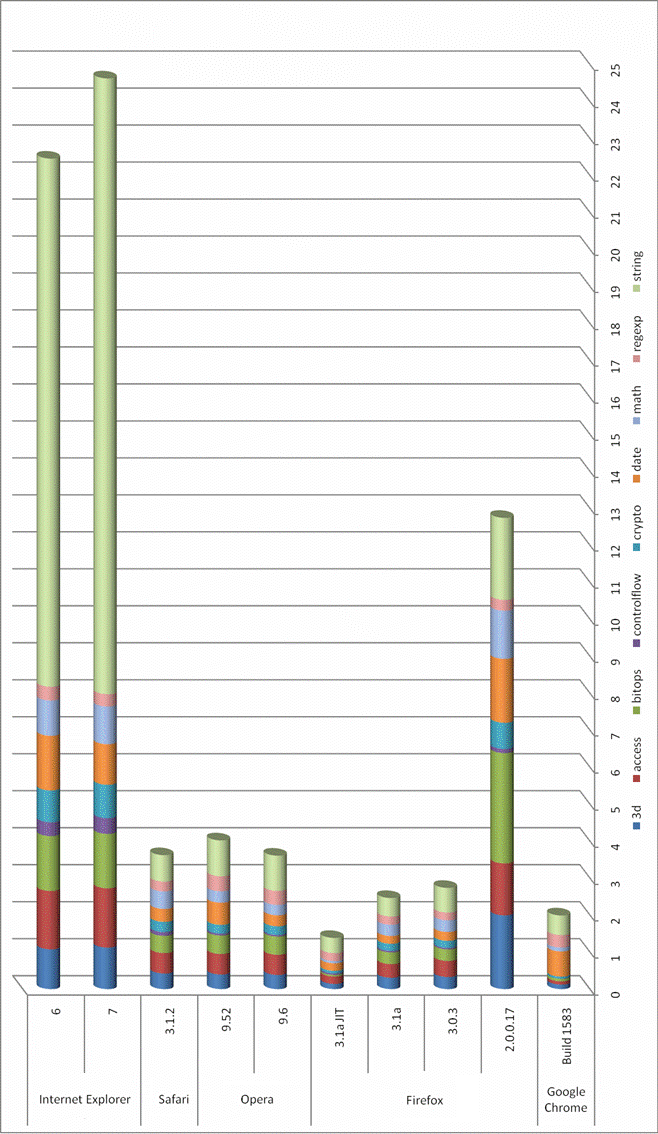
As you can see there are quite some differences which you should be able to “feel” also on current AJAX driven sites. Specially the new JIT (only in beta and not activated by default currently) for Firefox should make it the performance leader.
Need help comparing x with y?
September 28, 2008
Here is something that helps you: WikiVS is the the one stop for up-to-date comparisons. Be it a comparison of MySQL vs PostgreSQL, Lighttpd vs Apache or Qt vs GTK. This website has all to help you base your decision on facts.
What are the benefits of such an site for you? The comparison should be up-to-date and you don’t need to look through long threads (some of them flame wars) discussing that topic. At last you can also contribute to the comparisons.
So it’s the open source / community way of doing something like this and I think thats great!
UPC (Austrian ISP) started using Sitefinder Service (Update)
September 3, 2008
The Austrian ISP UPC (Chello, Indo, Telesystem) has activated a system which sends your browser to UPC site if a domain could not be resolved. They say that this helps their less tech-savvy customers but I believe it helps them more. Because they can put some ads on this site. They are not the first to try this. 2003 Versign tried something similar (called Sitefinder) but it was stopped by ICCANN and user protests. But that was not a provider.
The system is an Opt-Out one and not Opt-In. You need to perform 5 clicks, fill out a form and time to wait for a support employee to get it deactivated. You should really Opt-Out as the system can lead to problems if an DNS server is responding too slow and the system tells you you’ve a wrong domain name. The other question is what happens with the data gathered by the search engine on this site, which tries to guess what you meant.
Update:
This site (german) contains all info how you can Opt-Out.
UDP Flood DDOS attack against my blog
April 24, 2008
Starting 18:00 CET (23.04.2008) someone started with a distributed denial of service attack against my blog. The UDP Flood attack was carried out, as showed my investigation by hacked servers and not zombie windows clients. At the time of writing the attack is still underway but got weaker after the first 24h.
The traffic accounting reports so far >750gb incoming traffic, but in reality it will be even higher as not every packet was counted in the beginning of the attack as it consumed large amounts of network resources. The data center my server is located at removed the route for the sub network from the border gateways, so the operation of the whole data cents was not affected. After I guess some network admins detected that some of their machines got misused for a DDOS and did shut them down, the traffic went down. After this happened the subnetwork has been reactivated again, and the blog is online again.
But why should someone attack my little blog in the first place? I didn’t post in the last 14 days. The only idea I’ve is that the hacker I found at the server of a friend and wrote about it wanted to get even. What counts for this theory is that it is carried out by hacked servers from and to random UDP ports – a feature the found bot also has.
I’ll investigate further and report in my blog about it.
Update: Following IP are still attacking me after >30h … it seems to be time to try to contact the admins.
202.147.170.5 (Pakistan) - informed - not active anymore after 48h
222.122.46.92 (Korea) - informed - not active anymore after 48h
72.36.175.98 (USA) - informed - reacted within 12h
85.214.100.202 (Germany) - informed - reacted within 12h
62.112.193.46 (Hungary) - informed - still active after 3 days
195.219.156.98 (Spain) - informed - reacted within 24h
211.174.182.13 (Korea) - informed - still active after 3 days
Update2: 3 days after the start of the attack it still continues. ok only with lonely 2 systems, whose admins don’t seem to care about the attack and my mail. whats the reason for this? did the hacker lose control over them? what does he gain with it – the side is online without any problems for the users. Has anyone an idea?
1+13+40+3+4 = 60 or 61?
March 22, 2008
A normal calculator would know the correct answer but not a Sequoia voting machine, which was used in a New Jersey Election. Take a look at the post “Evidence of New Jersey Election Discrepancies”, which shows a summary tape for the presidential primary election. Now the word is out, what is the reaction of Sequoia? Sure, threat the guy who had the insolence to recalculate the numbers on the summary tape, so he buckles under rather than show how poorly designed Sequoia’s e-voting machines are. But what do we know about bloggers? That this will evoke the Streisand Effect as bloggers around the word will now know about it and will blog about it.
That shows this again, we can’t let something as important as our demography depend on trade secrets. Voting computers are just a bad idea, as every citizen needs to be able to verify the correct enumeration. Sure most won’t do it, but they could and some even will specially in turbulent times, when it specially counts.
Take also a look at this humorous little video (which I found here) concerning how insecure voting machines are.
Goals and purpose of this blog
December 30, 2007
This blog is about Linux (and open source in general), IT security, and tips and tricks and if possible some off topic stuff. I define Linux in this case as the whole ecosystem which is built around the Linux kernel. Still to fuzzy?
In my spare time I often write small scripts which help me to save time. These are often small scripts, but even the medium ones (at least in the beginning) are too small for a dedicated project page (e.g. on sourceforge) like I did for ignis or cdemu. I specially don’t know if anyone is
interested in them and/or what additional features and functionality are needed. In this blog I can just post them and attach the source to post and look if they are interesting for others.
In my daily life I come also across problems where I’m not able to find HowTos or good solutions by simple searching in Google. Maybe it’s because I’m not entering the correct search terms ;-). In this cases I will post the problem and solution in this blog so Google will hopefully find it for others who search with the same terms I do.
This blog should also be the place which links my various online stuff together, and provide it hence with a higher Page Range in Google and makes all of my stuff easier findable for others.
The above topics are mostly about making stuff, which I would have also done without this blog, easier accessible for others, which will be the major part of the blog’s content (at least in the beginning), the following topics are more likely to generate content explicitly for this blog.
IT security interested me since my time at the university – and my master thesis with the topic “Analysis and design of a SIM based authentication solution for WLAN” was also in this field. As you see I’ve quite an interest in this field, and I therefore thought it should be fun to blog about it. There won’t be many articles as I’m not thinking about just linking to other information and saying. “Yeah they’re rightâ€
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
34 queries. 0.114 seconds.





