Dropbox notify feature leaks information
January 20, 2015
While I was routinly looking with Wireshark through traffic … everybody needs a hobby 😉 … I saw something interesting. One client was sending a HTTP GET request every 55 seconds. Looking at that request showed following:
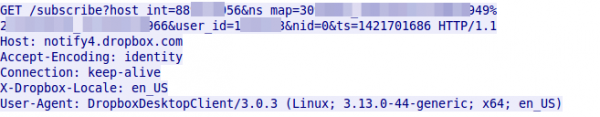
which leads to following response normally:
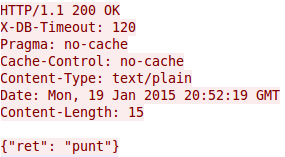
But lets take a look back to the request. This is the Dropbox client doing requests for checking if some other host changed a file. The problem is that it is HTTP and not HTTPS and the user_id and host_int is send in clear text as GET parameters. With this it is easy for some party that sees much of the traffic to track a user over networks and devices. Ok that can also be done via cookies as the Snowden documents show, but they are not send every 55 seconds even if you don’t surf the web – the client does that in the background all the time – a wonderful tracking beacon.
I find that a bad security practice as with HTTPS there would be no information leak and as the SSL connection could also be persistent as the HTTP connection already is, it would be no big additional load on the servers. Anyway – even if HTTP would be a must, it should be POST and not GET, as the GET parameters are stored in proxies servers (e.g. in a transparent ones)
No Comments yet »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
38 queries. 0.060 seconds.





