New RTF macro Malware from the Dridex gang
March 23, 2016
In the aftermath of Locky many companies started blocking EXE files directly attached or in ZIP files on their mail gateways. Some moved further and started removing active content in DOC, XLS, and other MS Office files. Today an old file type got used again and the virus scanner hit rate was really bad again.
Details
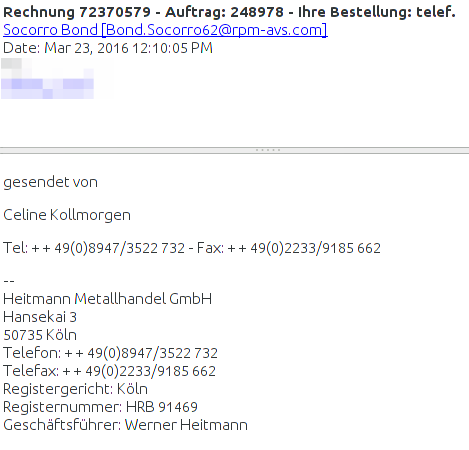
The Malware gets delivered by mails with a RTF file attached (which is often used in the medical area), which e.g. looks like this:
The company exists if you check before opening the attachment. Normally bad RTF files did contain EXE files within them, but not this time. This time it contains highly obfuscated macro code, which MS Word executes. which looks like this:
Sub Document_Open()
Dim HGFDSXDSFVV
HCFDSFDSFB = "hel"
VDSFCDSJ = "qweee"
GoTo PQOycAsH
Dim XJwoBhgN As String
Open "JQJLAG.ANU" For Binary As 66
GoTo pKlIahvf
Dim wVyQZrAv As String
Open "CTTBNH.FEB" For Binary As 18
Put #18, , wVyQZrAv
Close #18
pKlIahvf:
Put #66, , XJwoBhgN
...
which then did use WScript.exe to download a file from
http://wrkstn09.PEORIASENIORBAND.COM/dana/home.php
other researchers report followingURLs:
http://connect.businesshelpa-z.com/dana/home.php
http://wrkstn09.satbootcampaz.com/dana/home.php
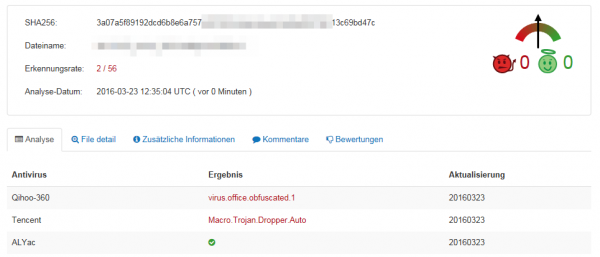
The file is called fuckyourself.ass which is in reality a EXE file, which contains the Malware itself. Uploading this (we’re one of the first it seems 😉 ) to Virustotal showed that only 2 virus scanner detected the Malware:
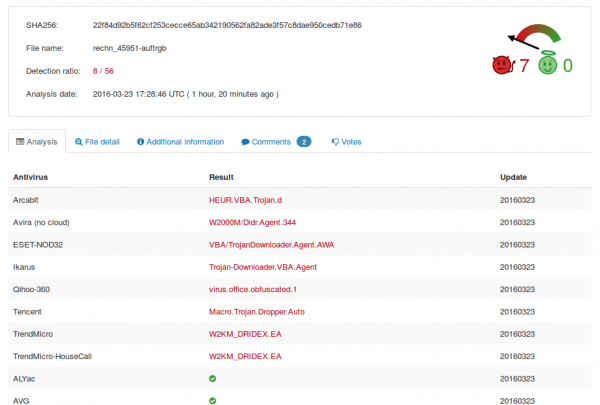
Some hours later and after others saw the file also in the wild and as we reported the file to virus vendors it looks a little bit better, but not good – for the dropper 8/56:
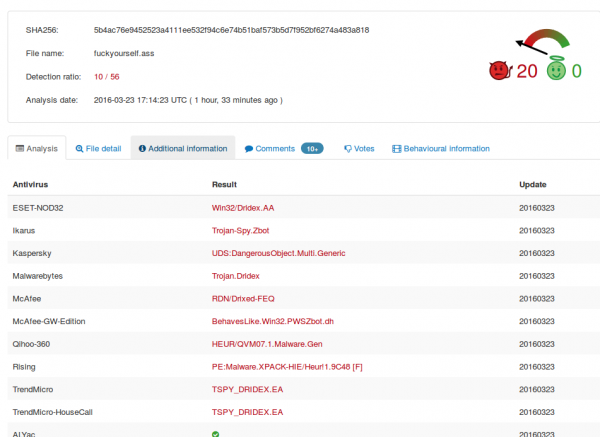
and for the malware itself 10/56:
I normally don’t write about single viruses, but this one is a show case for some opinions I’ve for some time now.
- Forget about normal virus detections – sure keep it on Windows system but don’t count on it.
- You really need to implemented procedures as described in this early blog post.
- It gets more and more important to implement a sand-boxing technology, where all your files which get to you’re company from the internet gets executed / opened. And this means every file .. not only executables. There are also sand boxing technologies that run on premise or in an European data center.
- Bigger companies can mitigate that problem easier, the problem child are home users and small companies.
I don’t have a good solutions for home users so far … maybe someone knows something that I could recommend the Windows home users I know.
2 Comments »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
42 queries. 0.066 seconds.






Hello.
I don’t know if im getting it…
It’s a simple RTF file and it’s only a problem if it’s opened via Word with macros enabled? Where is the macro exactly, how it’s placed in RTF and how is it executed? I thougth RTF is not able to contain macros?
I would appreciate some further information, if you have the time…
Thanks for the article 🙂
Comment by max k. — April 7, 2016 #
Send me a mail and I can send you the RTF file so you can look at it yourself.
Comment by robert — April 8, 2016 #