Hypo Tirol – Repeat after me: HTTP is bad, HTTPS is good
January 24, 2015
As I know many friends which are Hypo Tirol banking customers and are using the mobile banking app – and my wife is on a business trip and its dark outside – I took a short look at the mobile banking app for Android. And “Oh my God” the same mistakes banks made 10 years ago with online banking are made again.
I downloaded the app and launched it … I got to following
So what does Wireshark tell me after the I started the app?
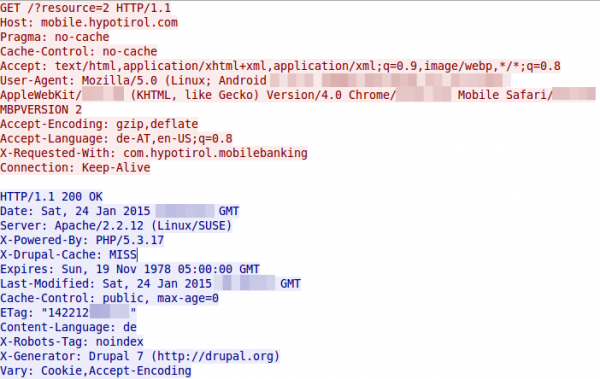
Yes, there is some (most part) HTTP … so lets open the URL on my PC.
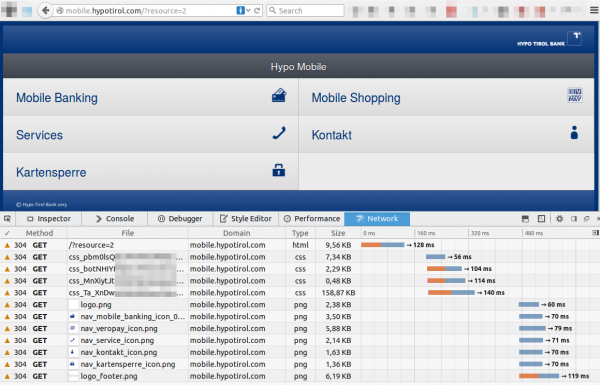
so the whole starting GUI of the banking app is transferred from the server via HTTP.
Attack vector
An attacker can use this to change the content to his liking and as the URL is not shown in the app it could be anything. An idea would be a site that looks like the banking site. The link “Mobile Banking” goes to the HTTPS URL
https://mbp.banking.co.at/appl/mbp/login.html?resource=002
The attacker just can copy and paste the pages and change the links, so it looks identical for the user ;-). So the only question remains – how an attacker can change the content:
- The DNS servers return the IP address of the attacker for mobile.hypotirol.com
- there are many know worms that change the DNS server settings of consumer internet routers
- DNS poisoning attacks … seen in the wild for banking attacks
- A Man in the Middle attack on a public Wifi, but the first two are much easier and can be exploited remotely.
Fix
Use HTTPS everywhere – no HTTP. And check the certificates.
3 Comments »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
40 queries. 0.061 seconds.






[…] app for Android. And “Oh my God” the same mistakes banks made 10 years […], Security Bloggers Network, robert, […]
Pingback by Security-Vision » Hypo Tirol – Repeat after me: HTTP is bad, HTTPS is good — January 25, 2015 #
Concerning blurring of sensitive content read http://dheera.net/projects/blur (Why blurring sensitive information is a bad idea) 🙂
Comment by Simon — January 26, 2015 #
@Simon: that content was not that secure … but for the next post I did it hopefully better 😉
Comment by robert — February 9, 2015 #