The insecurity of the online version of the Tiroler Tageszeitung
January 17, 2015
This is the first post in over a month, why? As always I was at the Chaos Communication Congress in Hamburg and as I came back there was finally snow –> so I went ski mountaineering. Anyway here is new post, as today its raining so let’s write a post. 😉
This post is about the lack of security awareness at the major tyrolian news paper Tiroler Tageszeitung (in short TT). So lets start why I believe that is true. To be more accurate what I found within 5minutes of looking – it took much longer to write this post.
The subscriber area
When you access http://user.tt.com/ you get following Login prompt.
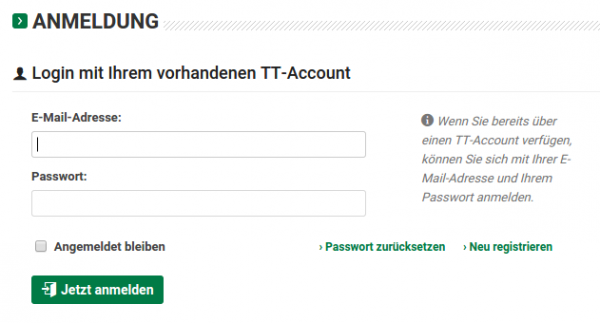
But look above ….
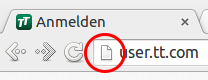
Yes, this site is not HTTPS protected. This is generally not a good idea as an attacker is able to change the URL the passwords are sent to after pressing the login button. But Ok, in 2011 that was not that bad, bad but not that bad. Why I talk about 2011 I’ll tell you later.
So lets enter our mail address and password and click the login button. What request is send?
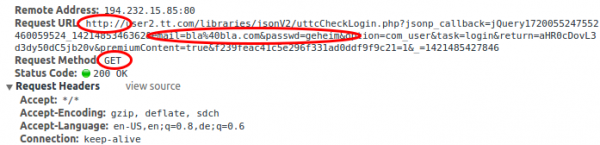
Yeap!
- It is HTTP and not HTTPS? In 2014 using HTTP for login? That was even in 2011 bad.
- They are using HTTP GET with the password as parameter. I can’t believe it. Why? GET parameters are logged on web servers and even worse on proxy servers. Newer, Newer summit passwords with GET, use POST and use HTTPS!
So reading the online TT while waiting for something in a public WiFi network (which is most likely unencrypted) is not a good idea. How many TT users are reusing their password (the email address is a given) ? How may users a potentially affected?
At least I’m able to answer the second question. There is the Österreichische Auflagenkontrolle (ÖAK) … which counts how many copies of a given print media are sold.
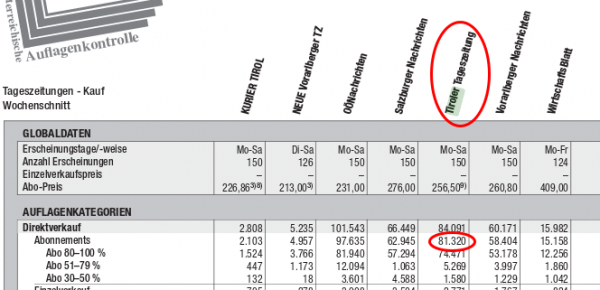
Thats from 2012, the ones from 2013 are sightly smaller but not that formated that nicely for showing a screenshot here. So over 80.000 affected users. The state of Tirol has about 720.038 citizens according to Wikipedia. So over 10% of the population is affected.
The server side
While looking at the get request I found something else interesting. At least the user.tt.com server seems to be running Debian Lenny.
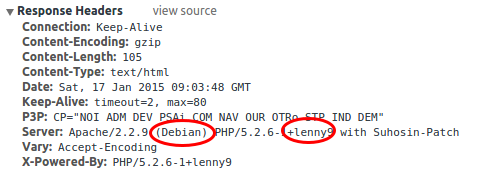
Why is that important? Let’s go to the Debian Wiki and have a look.
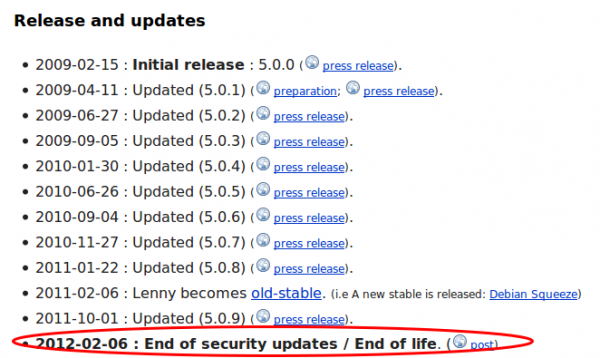
Yes, you read that correctly. No security updates since 2012 and it I believe nobody installs a system with a operation system that is old-stable, the server install and setup must be at least be from 2010. So lets take a look what vulnerabilities be could possible find for Apache 2.2 and PHP 5.2.6 patched the last time in 2012. Let’s have a look at PHP first and followed by Apache. Apache is better than PHP, but for PHP there are some pretty high rated vulnerabilities, one even with the highest rating. Basically you can get everything from the box if you want. When I took a look which JavaScript made the HTTP GET request with the password I found following.
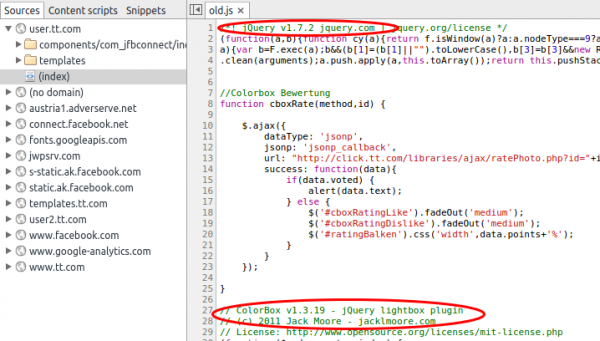
jQuery 1.7.2 that sounds old …. a look at the release notes tells 21.3.2012, not new but only a medium vulnerability … attacking PHP is easier.
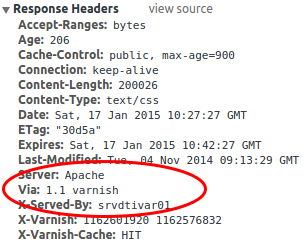
Basically we could own the user.tt.com server easily, but whats about the other servers. Are they better? What is obvious from the start that the servers for the main site are different ones and they are using Varnish as is an HTTP accelerator and the learned to hight the Apache version in the HTTP header.
A short look in the Whois shows that the user.tt.com seems to be hosted by the TT itself and the frontend server for www.tt.com by the APA guys. It seems that they are filtering the bad stuff from the backend TT servers. As I didn’t want to dig deeper than whas possible in 5 minutes I stopped here … Just one thing I found which is not security related: tt.com is heavy using Google services for example Google Analytics.
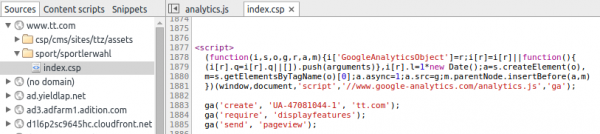
The option _anonymizeIp() is missing here to not violate the Austrian data protections law and you need to post a information for your visitors (could not find one on tt.com) and make a opt-out possible.
So much for my 5 minutes analytics of the Tiroler Tageszeitungs homepage. 😉
No Comments yet »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress
Entries and comments feeds.
Valid XHTML and CSS.
40 queries. 0.075 seconds.





